Preface: To be precise, over 250,00 active sites use Magento.
Only 11,000 of those run on Magento 2, though. Many well-known international companies have chosen Magento as their e-commerce solutions, including Coca-Cola, Nike, Harpers Bazar, Fiji Water and Olympus.
Vulnerability details: Adobe has released security updates to address vulnerabilities in Magento Commerce 2 (formerly known as Magento Enterprise Edition) and Magento Open Source 2 (formerly known as Magento Community Edition). An attacker could exploit some of these vulnerabilities to take control of an affected system.
Remedy by Magento:
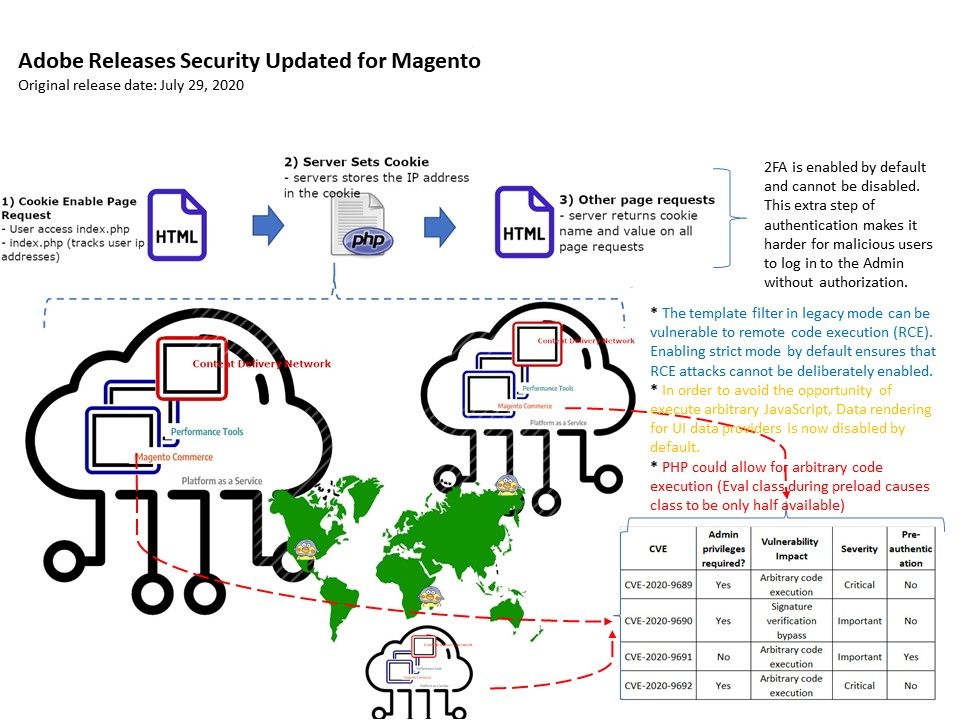
- The template filter in legacy mode can be vulnerable to remote code execution (RCE). Enabling strict mode by default ensures that RCE attacks cannot be deliberately enabled.
- In order to avoid the opportunity of execute arbitrary JavaScript, Data rendering for UI data providers is now disabled by default.
- PHP could allow for arbitrary code execution (Eval class during preload causes class to be only half available)
- 2FA is enabled by default and cannot be disabled. This extra step of authentication makes it harder for malicious users to log in to the Admin without authorization.
Official announcement: For more details, please refer to the link – https://helpx.adobe.com/security/products/magento/apsb20-47.html