Preface: Apple replaces bash with zsh as the default shell in macOS.
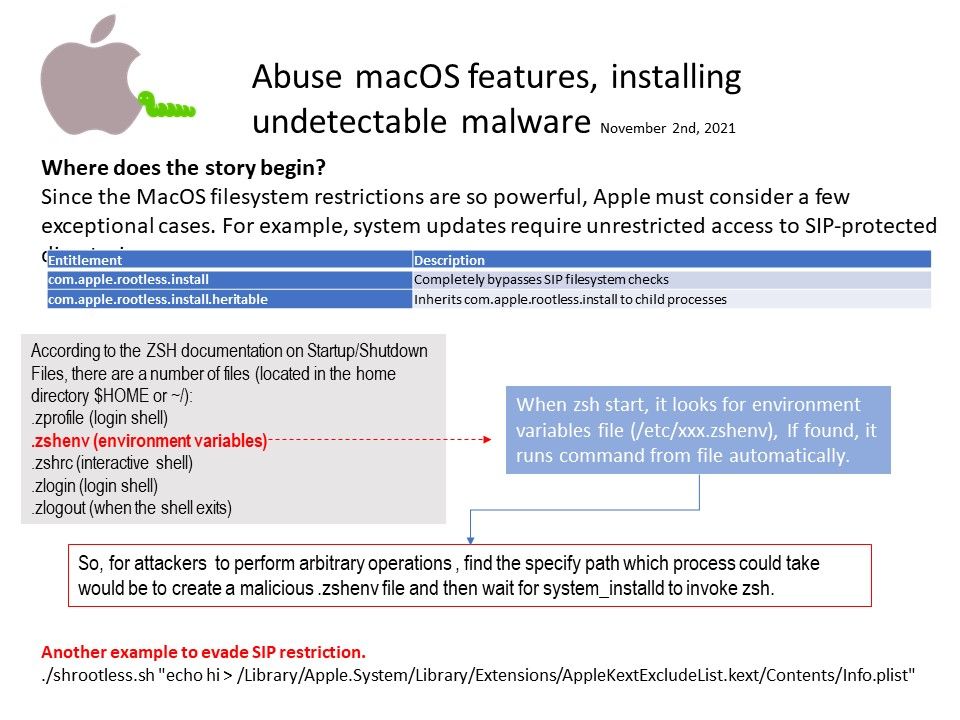
Background: According to the ZSH documentation on Startup/Shutdown Files, there are a number of files (located in the home directory $HOME or ~/):
[.]zprofile (login shell)
[.]zshenv (environment variables)
[.]zshrc (interactive shell)
[.]zlogin (login shell)
[.]zlogout (when the shell exits)
When zsh start, it looks for environment variables file (/etc/xxx[.]zshenv), If found, it runs command from file automatically.
Vulnerability details: The vulnerability is tracked as CVE-2021-30892 and was discovered in macOS Monterey 12.0.1 and Big Sur and Catalina updates.
So, for attackers to perform arbitrary operations , find the specify path which process could take would be to create a malicious [.]zshenv file and then wait for system_installd to invoke zsh.
If you are interested in this matter, please refer to the URL