Preface: The registration of CVE records is largely out of sync with the time of the event. Perhaps the new release of CVE record by today, however it was happened few weeks or months ago. But with reference of these vulnerabilities records. Vulnerability scanner can precisely provide a result to you after scan.
Background: SAP SE — SE stands for societas Europaea, a public company registered in accordance with the European Union corporate law.
SAP NetWeaver is a software stack for many of SAP SE’s applications. The SAP NetWeaver Application Server, sometimes referred to as WebAS, is the runtime environment for the SAP applications and all of the mySAP Business Suite runs on SAP WebAS: supplier relationship management (SRM), customer relationship management (CRM), supply chain management (SCM), product lifecycle management (PLM), enterprise resource planning (ERP), transportation management system (TMS)….copy from wiki
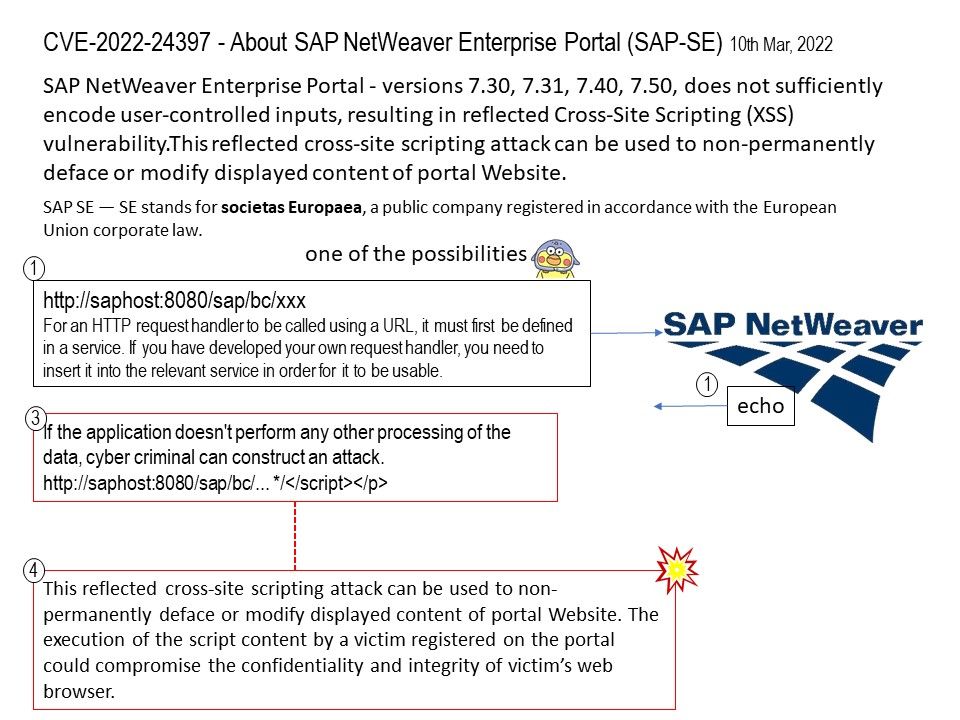
Vulnerability details: SAP NetWeaver Enterprise Portal – versions 7.30, 7.31, 7.40, 7.50, does not sufficiently encode user-controlled inputs, resulting in reflected Cross-Site Scripting (XSS) vulnerability.This reflected cross-site scripting attack can be used to non-permanently deface or modify displayed content of portal Website.
*Cross site scripting attacks can be broken down into two types: stored and reflected.
Stored XSS, also known as persistent XSS, is the more damaging of the two. It occurs when a malicious script is injected directly into a vulnerable web application.
Reflected XSS involves the reflecting of a malicious script off of a web application, onto a user’s browser. The script is embedded into a link, and is only activated once that link is clicked on.
Impact: The execution of the script content by a victim registered on the portal could compromise the confidentiality and integrity of victim’s web browser.