Preface: The registration of CVE records is largely out of sync with the time of the event. Perhaps the new release of CVE record by today, however it was happened few weeks or months ago. But with reference of these vulnerabilities records. Vulnerability scanner can precisely provide a result to you after scan.
Background: BIND (Berkeley Internet Name Domain) is a software collection of tools including the world’s most widely used DNS (Domain Name System) server software. This feature-full implementation of DNS service and tools aims to be 100% standards-compliant and is; intended to serve as a reference architecture for DNS software.
DS Lookup lets you check DS records for any domain. The online tool allows you to query the DNS servers and identify the Delegation Signers (DS) record for the specified domain.
On 26th Jan, 2022. ISC official announce the release of BIND 9.18.0. This is the first stable release that contains support for DoT and DoH. This branch will be supported for 4 years, through the end of 2025. With this new branch, the BIND 9.11 branch is officially EOL. We will continue to issue security patches for 9.11 for the remainder of Q1 2022, but that will be the end of maintenance for 9.11.
Remark: Support for securing DNS traffic using Transport Layer Security (TLS). TLS is used by both DNS-over-TLS (DoT) and DNS-over-HTTPS (DoH).
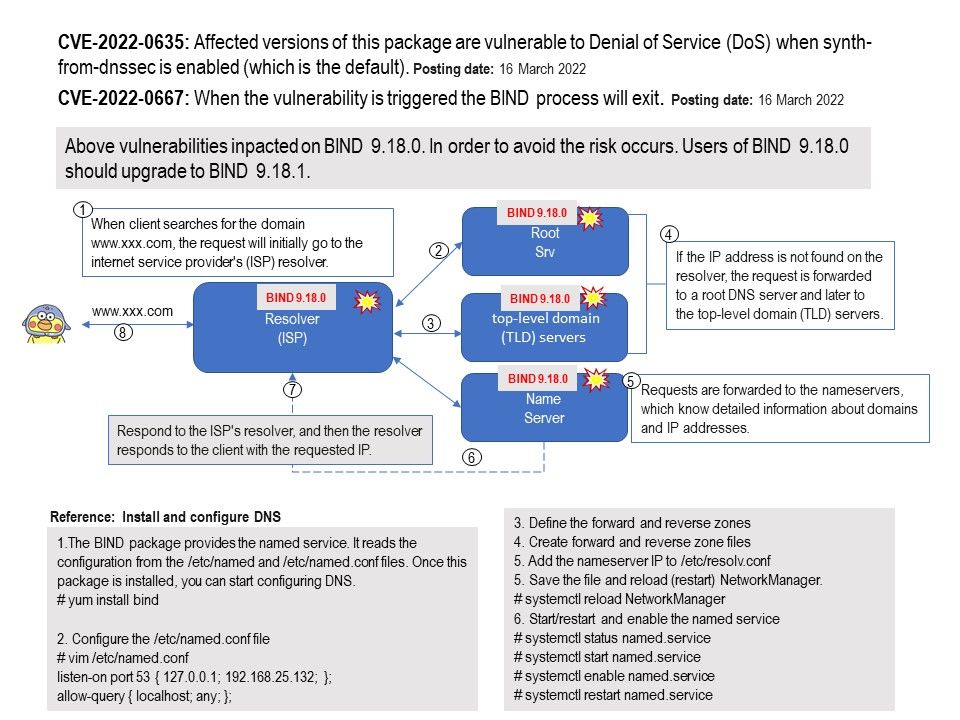
Vulnerability details:
CVE-2022-0635:The vulnerability affects BIND resolvers running 9.18.0 that have both dnssec-validation and synth-from-dnssec enabled. (Note that dnssec-validation auto; is the default setting unless configured otherwise in named.conf and that enabling dnssec-validation automatically enables synth-from-dnssec unless explicitly disabled)
Solution: Users of BIND 9.18.0 should upgrade to BIND 9.18.1
Ref: https://kb.isc.org/docs/cve-2022-0635
CVE-2022-0667:While BIND is processing a request for a DS record that needs to be forwarded, it waits until this processing is complete or until the backstop lifetime timer has timed out. When the resume_dslookup() function is called as a result of such a timeout, the function does not test whether the fetch has previously been shut down. This introduces the possibility of triggering an assertion failure, which could cause the BIND process to terminate.
Solution:Users of BIND 9.18.0 should upgrade to BIND 9.18.1
Ref: https://kb.isc.org/v1/docs/cve-2022-0667
End of topic