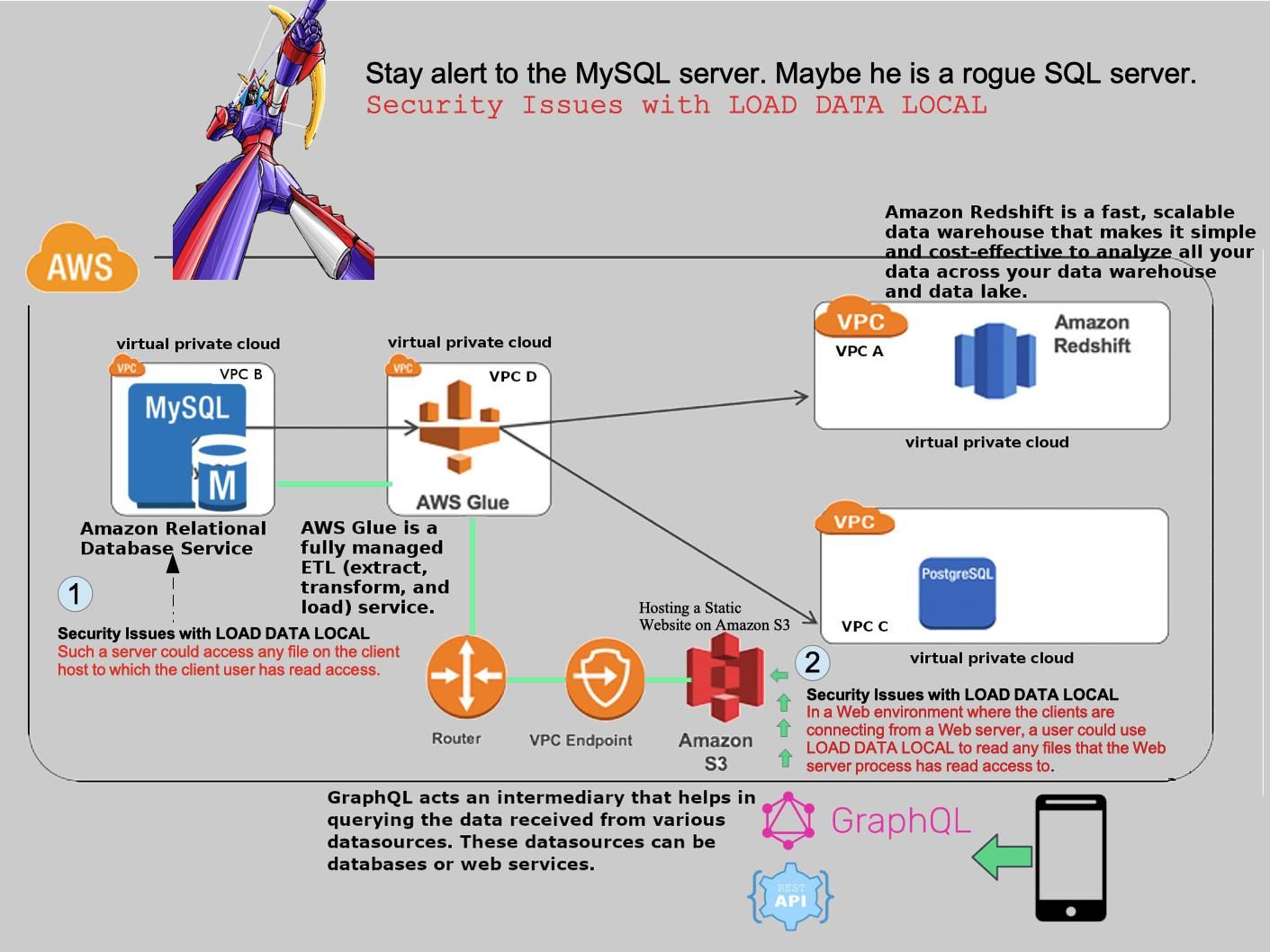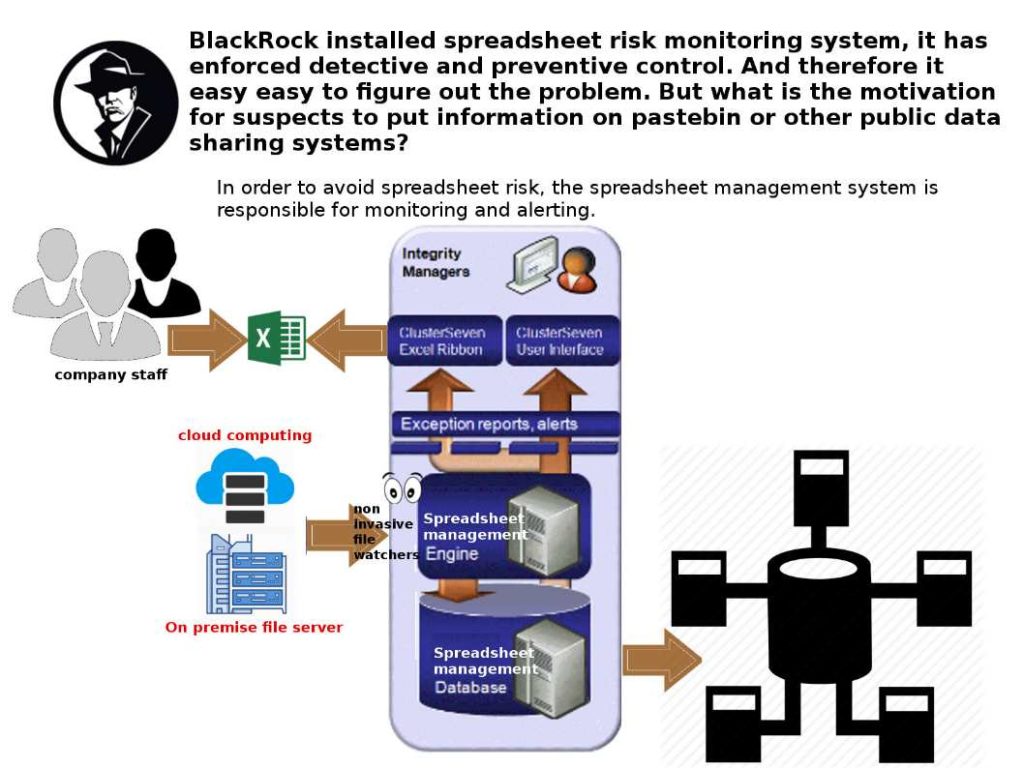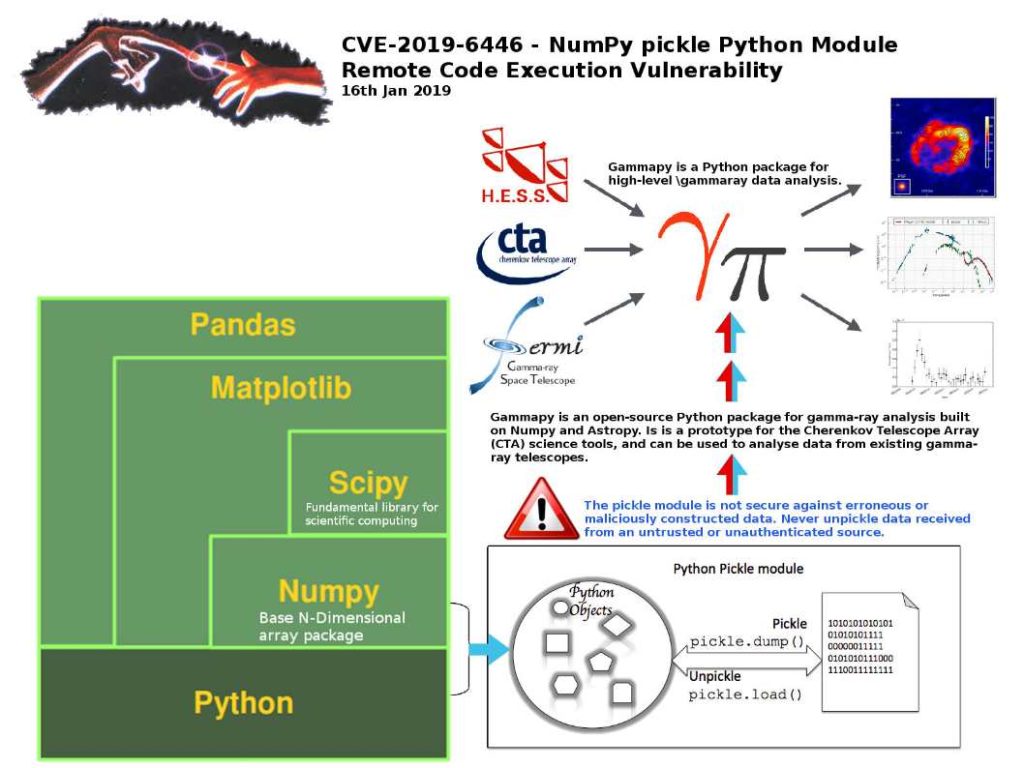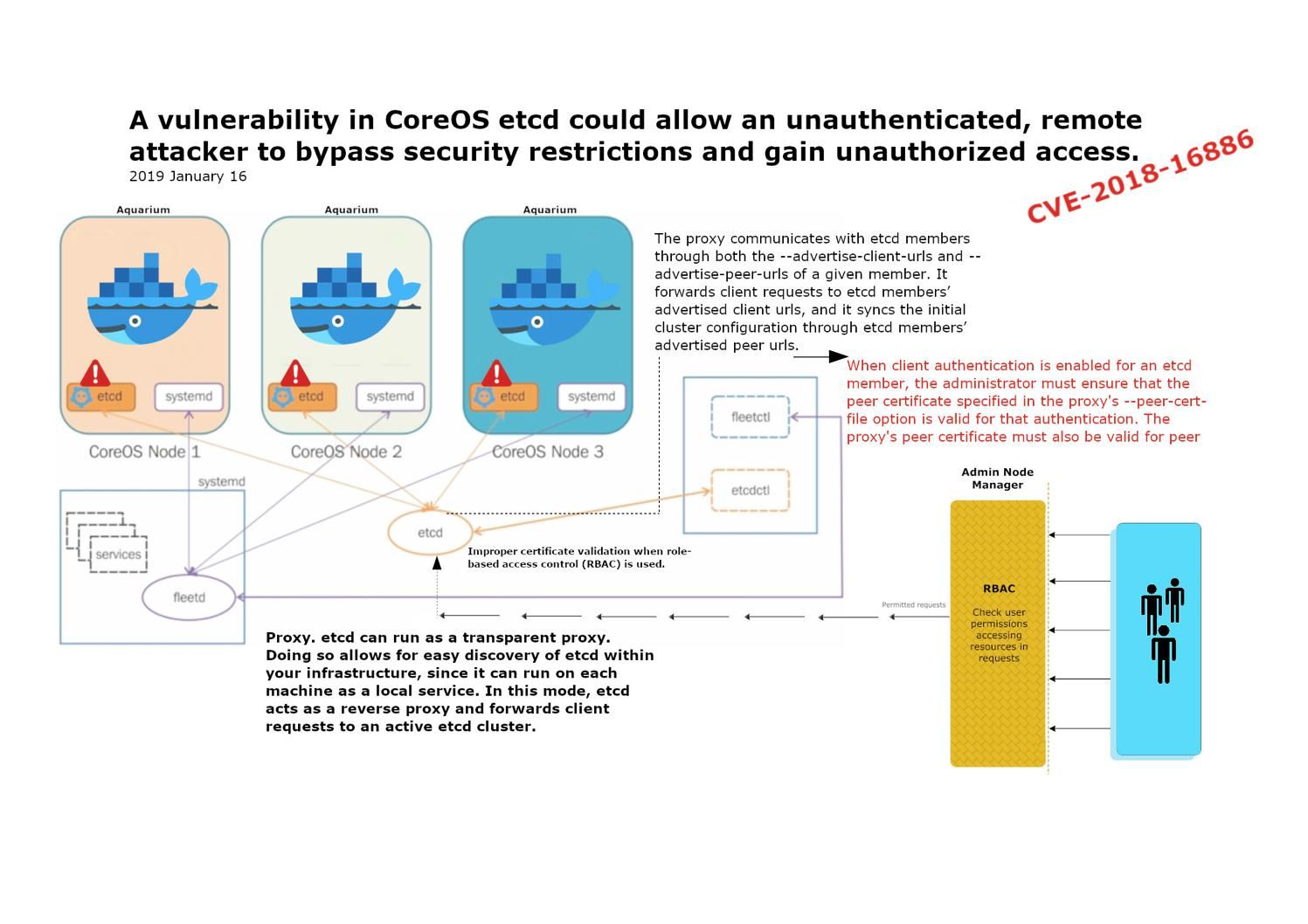
Preface: Every computer has a finite amount of memory so OS might actually need to use more than is physically available on your system. As a result, it is hard to avoid sharing resources feature.
Our security focus:
In regard to security update announced by Apple. Our security focus of this topic will be follow closely of malicious application may cause unexpected changes in memory shared between processes.
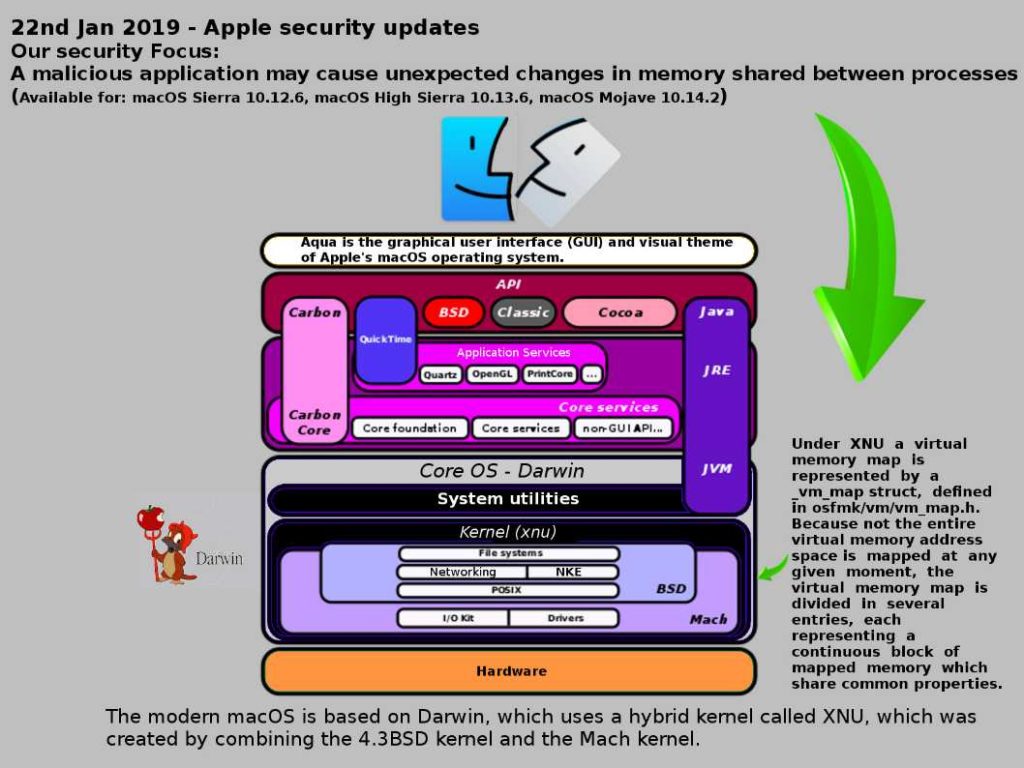
Under XNU a virtual memory map is represented by a
_vm_map struct, defined in osfmk/vm/vm_map.h. Because not the entire virtual memory address space is mapped at any given moment, the virtual memory map is divided in several entries, each representing a continuous block of mapped memory which share common properties.
Design limitation:
CVE-2019-6205 and CVE-2019-6208: A malicious application may cause unexpected changes in memory shared between processes.
Remedy:
The Apple Security Update covers all of its products. For more information, please see the following: https://support.apple.com/en-hk/HT209446