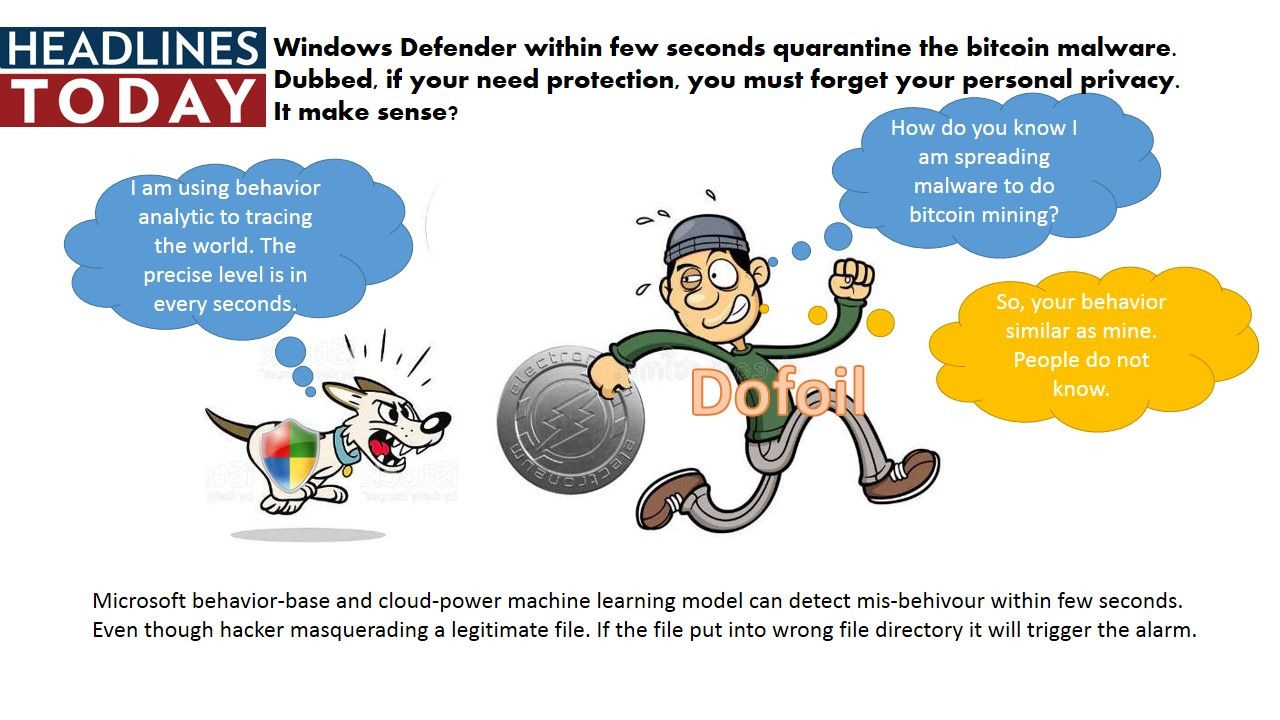
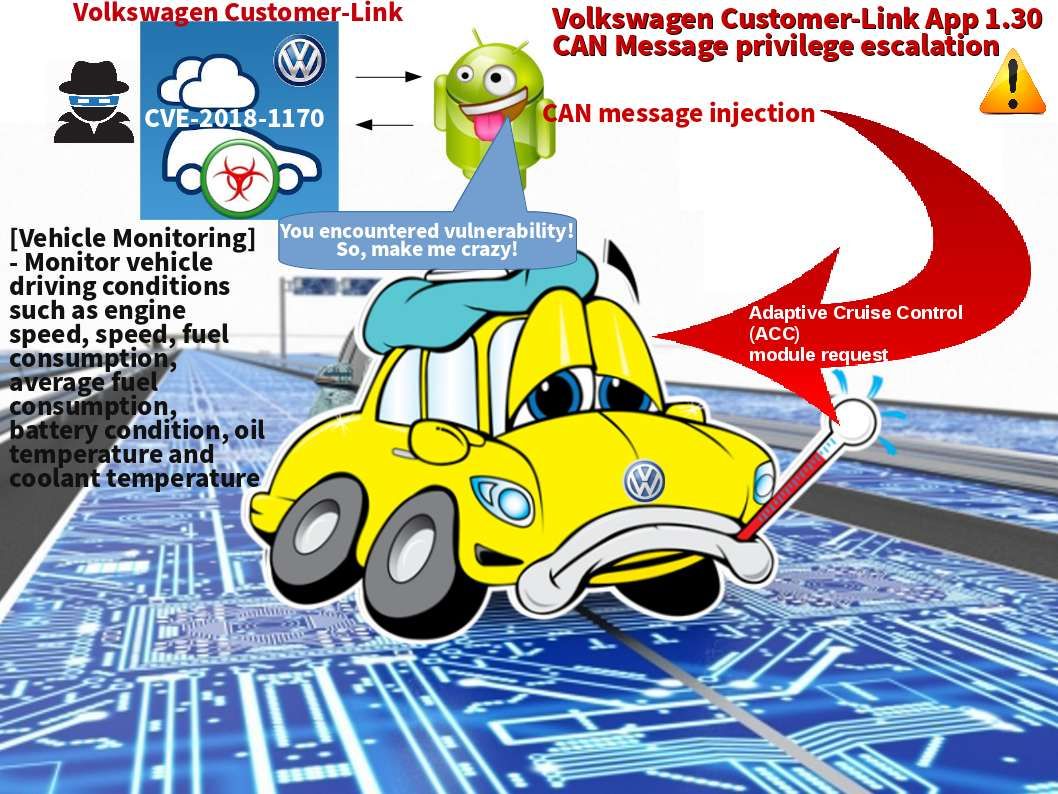
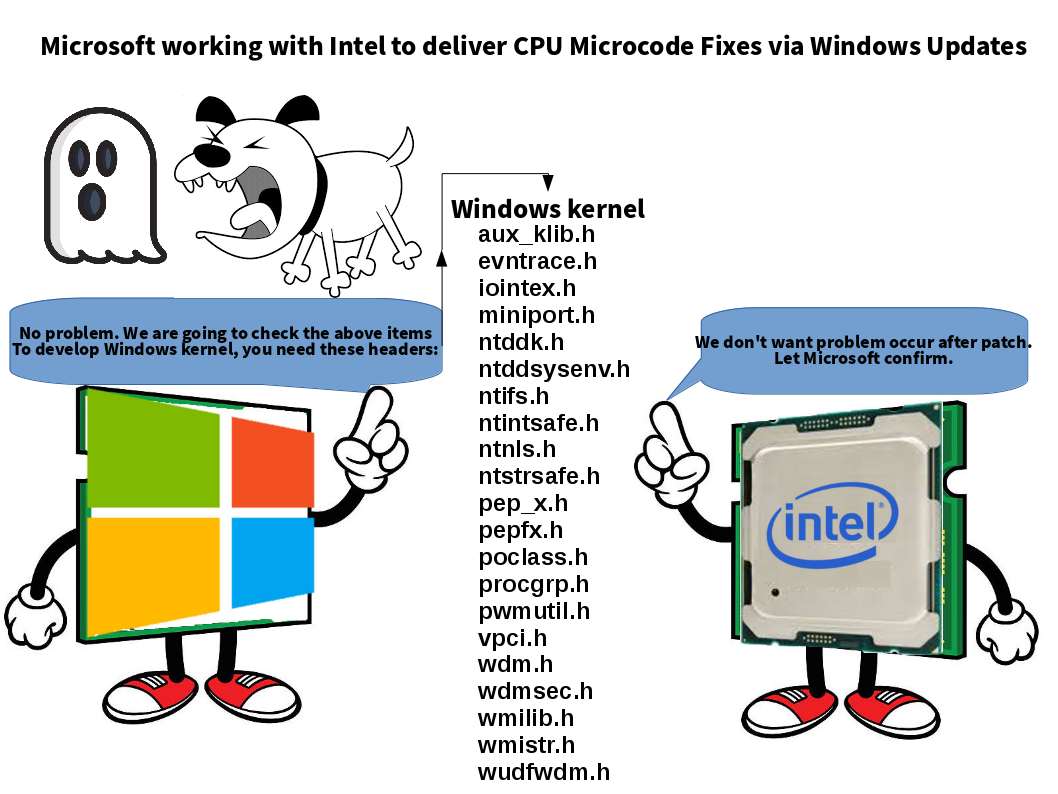
Preface:
Till 2018-02-01, the official announcement provides the following details.
Security patch level—Vulnerability details
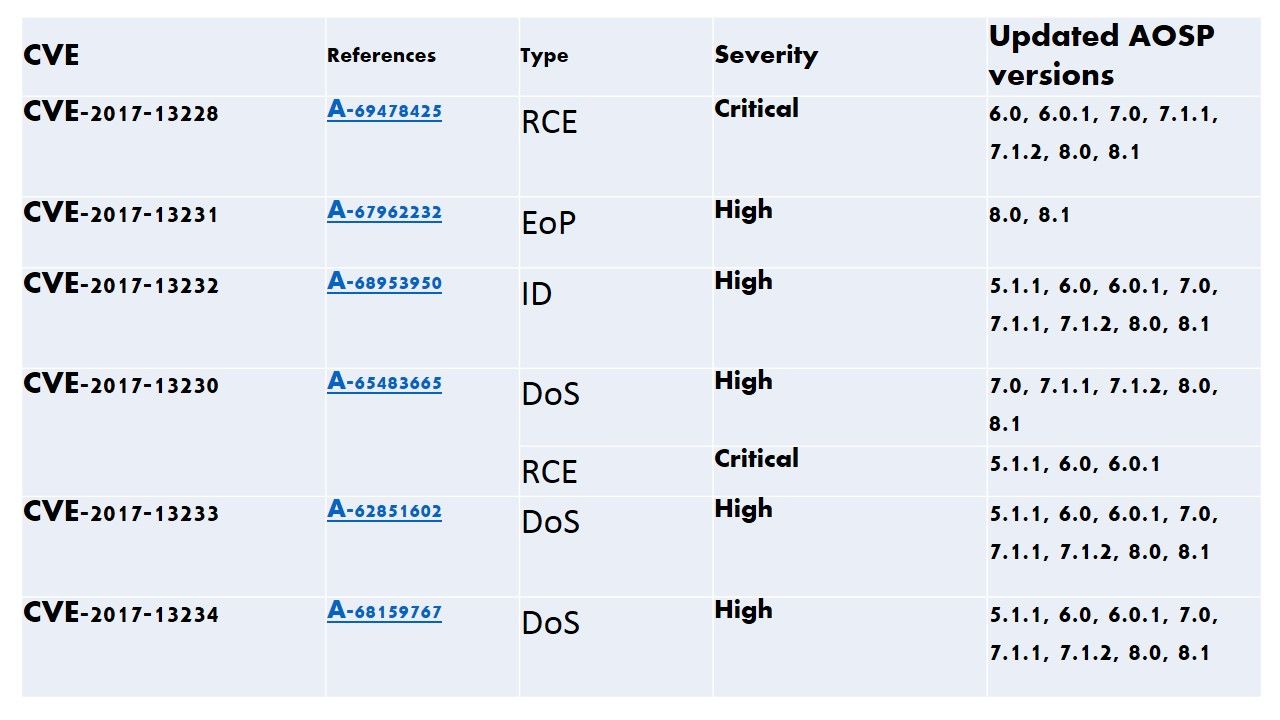
Start discussion:
ART (Android RunTime) is the next version of Dalvik. Unlike Dalvik, ART introduces the use of ahead-of-time (AOT) compilation by compiling entire applications into native machine code upon their installation. Regarding to Android security bulletin on February 2018, the official announcement did not had cyber incident reports of active customer exploitation or abuse of reported issues. But why do security expert said Andorid smartphone system is under cyber attack.
Basic understanding of ART boot sequence (see below diagram for reference)
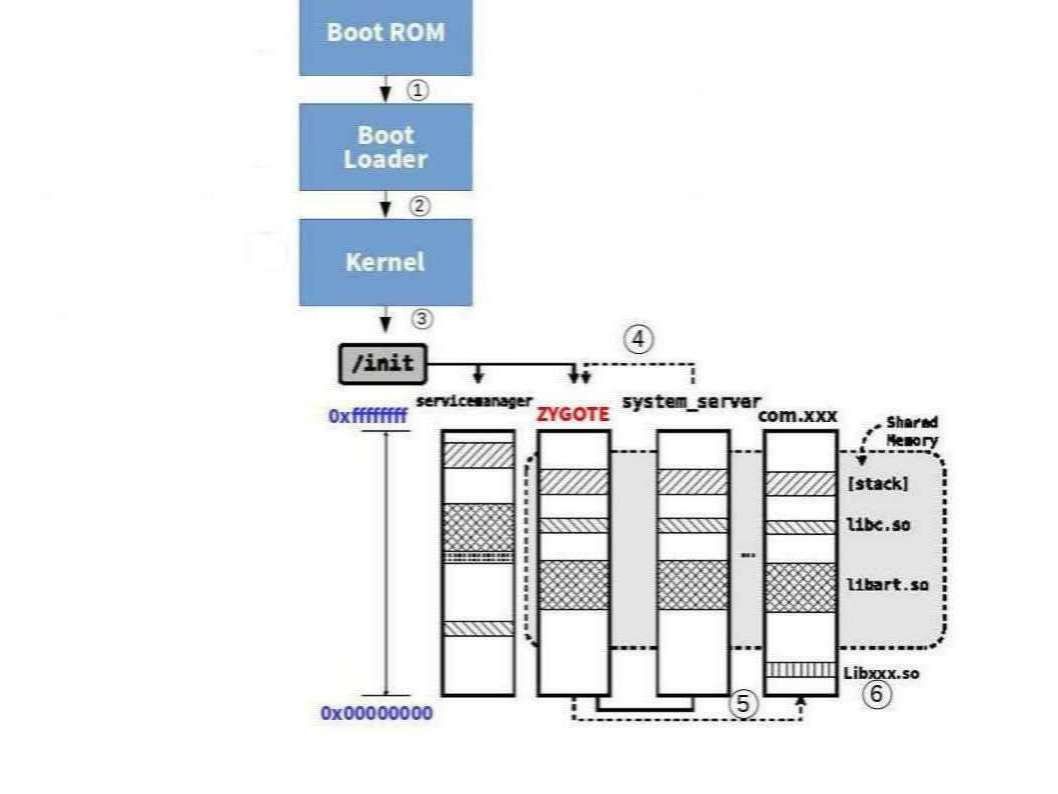
Zygote is running as UID=0 (root). After forking child process, its UID is changed by setuid system call.
A closer look on above diagram step 4 to step 6 operation flow (see below)
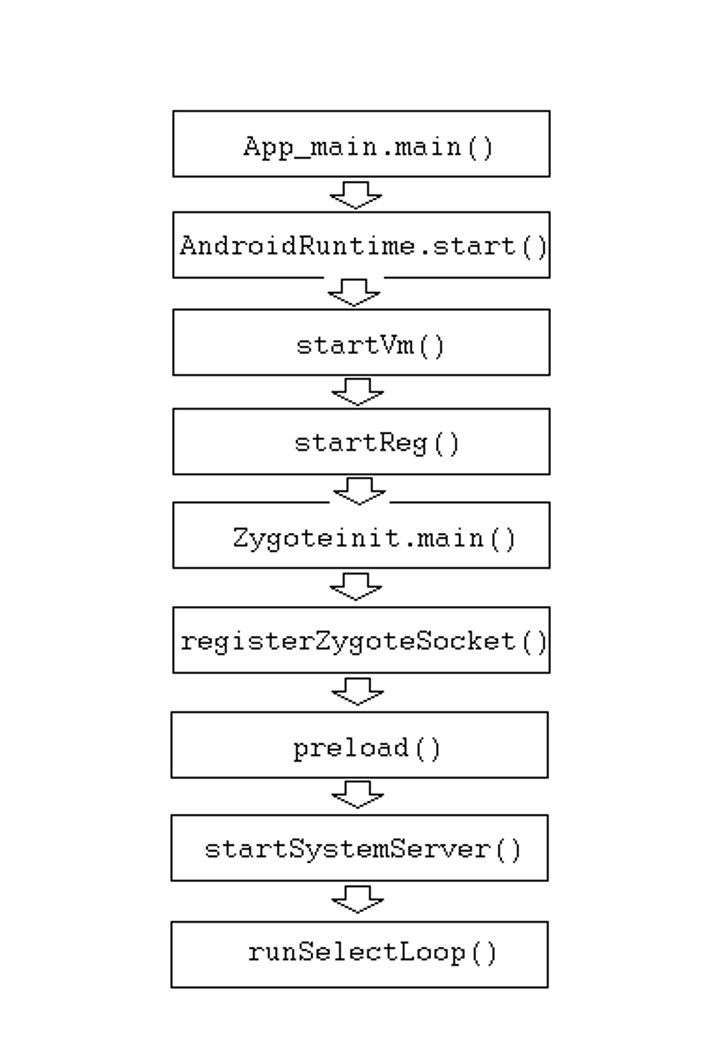
Software/application installation workflow
We heard that Google App store sometimes contains malicious code APK. And such a way compromise the Android OS. Below diagram can explicitly provide an idea how Android download and install a application program in normal way.

Lock down
Refer to above information (3 items of diagrams), we lock down 2 items of components for our investigation.
Zygote – When the application start, the Zygote will be forked, target into 2 units of VM. Since all the core library interconnect with zygote. And therefore both zygote and application sharing the library. The memory will only be copied if the new process tries to modify it.
Even thought the core library is read only. However the copy of memory procedure lure threat actors modifies Zygote system process in the memory to achieve their goal.
How does it works? – The injection code works is that their payload is part of any new process spawned, whereas if you use Frida to inject into Zygote it will stay behind when it calls fork() to become the app to be spawned. (Though technically Frida’s code Frida 9.x) will be part of the newly forked child, but no threads survive the fork except the thread that called fork(), so any hooked functions will call into Frida code (Frida 9.x) in an undefined state.
Summarize of the concept
- spawn([“com.android.xxx”]) with the package name.
- enable_spawn_gating() and listen to the spawned signal in order to do early compromise of memory address. For more details, please see below information for reference.
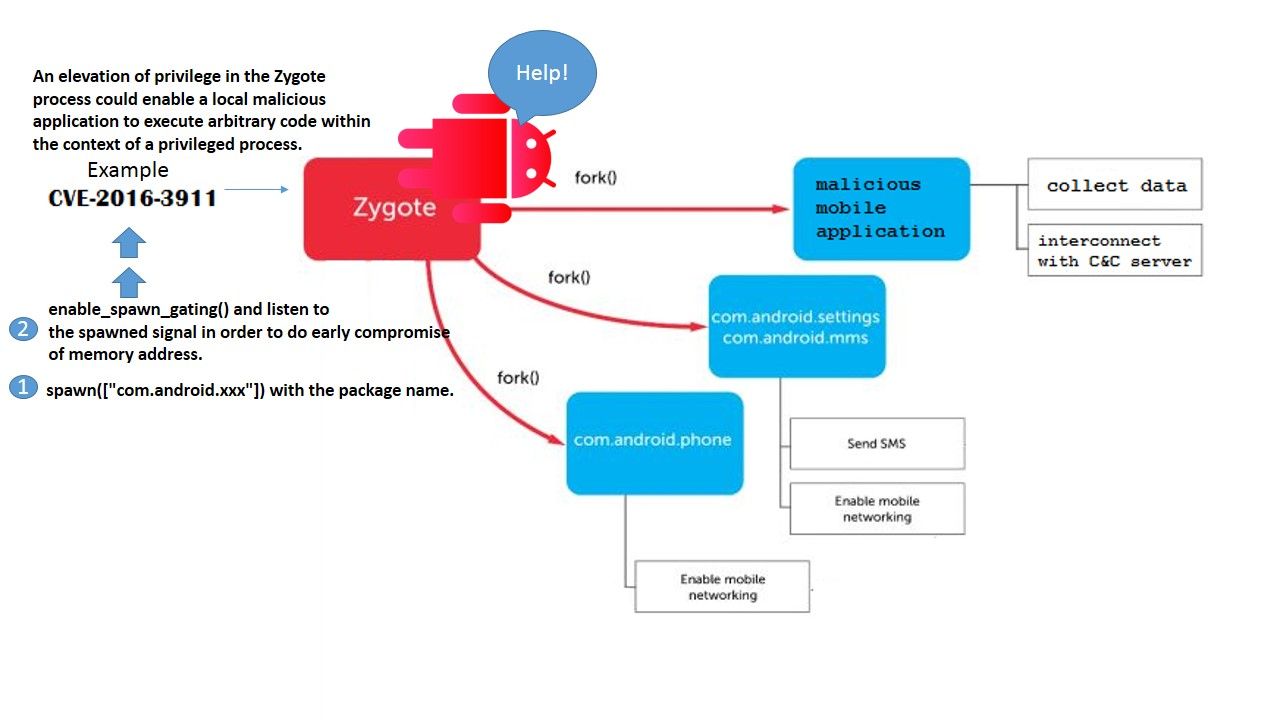
Reference: Frida (Dynamic instrumentation toolkit for developers, reverse-engineers, and security researchers).
APK – We notice that Google scan the apps on their play store to avoid malicious APK place on their store. However the security expert aware that it is hard to scan the APK which contained the malicious script embedded in APK file. Below example may a old style technique. However we only provides awareness and therefore I quote this example for reference.
The Android ZIP APIs do not prevent directory traversals by default, allowing for a file with a directory traversal in the name to be injected into the ZIP. This allows us to gain an arbitrary write in the context of the app. The zip was injected with a directory traversal that writes inside of the app directory. As a result, the malicious zip files were written in the application’s data directory. You can gain an arbitrary file write primitive. But the Arbitrary File contains risk causes remote code execution. For instance, Mercury Browser for Android is prone to directory traversal vulnerability and a security bypass vulnerability. Exploiting these issues will allow an attacker to bypass security restrictions, perform unauthorized actions and access, read and execute files. Information harvested may aid in launching further attacks.
Recommendation
In order to avoid unforeseen cyber incident encounter. Below details is the recommendation provided by federal government.
Federal Mobile Device Security Recommendations
- Create a mobile device security framework based on existing standards and best practices.
- Bolster Federal Information Security Modernization Act (FISMA) metrics to focus on protecting mobile devices, applications and network infrastructure.
- Incorporate mobility into the Continuous Diagnostics and Mitigation program to address the security of mobile devices and applications with capabilities that are similar to those of workstations, servers and other network devices.
- Establish a new program in mobile threat information sharing to address mobile malware and vulnerabilities.
- Coordinate the adoption and advancement of mobile security technologies into operational programs to ensure that future capabilities include security and defense against mobile threats.
- Develop cooperative arrangements and capabilities with mobile network operators to detect and respond to threats.
- Create a new defensive security research program to address vulnerabilities in mobile network infrastructure.
- Increase active participation by the federal government in mobile-related standards bodies and industry associations.
- Develop policies and procedures regarding U.S. government use of mobile devices overseas.
— End of discussion —