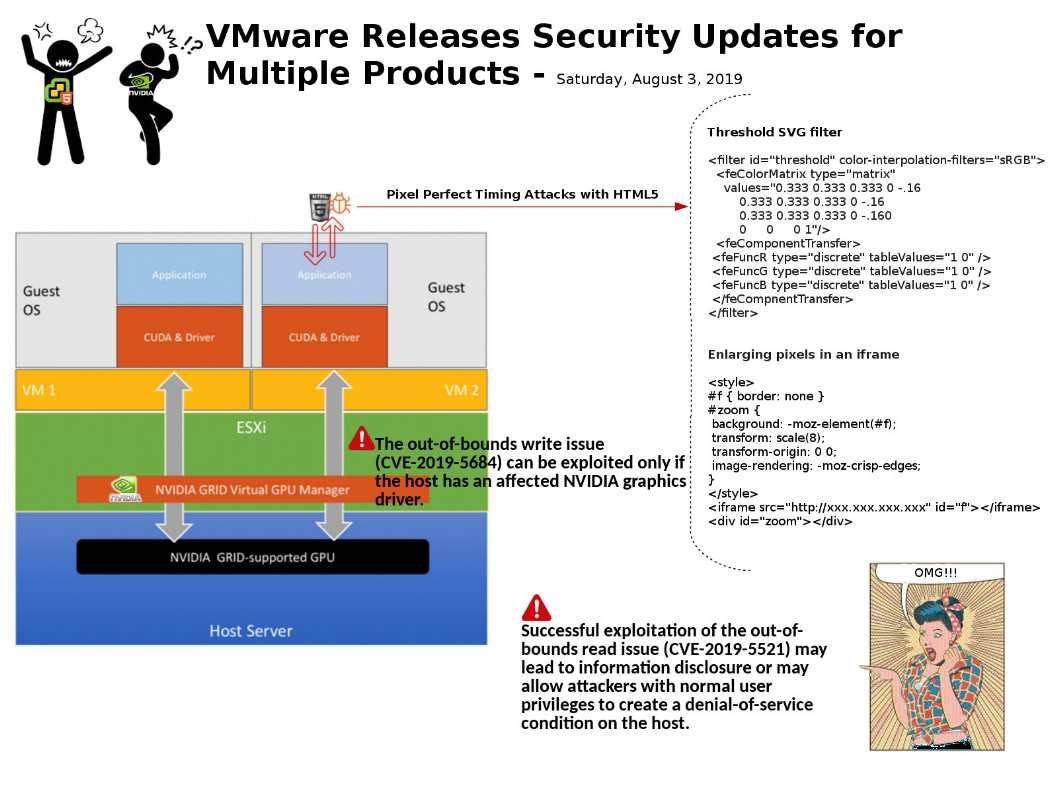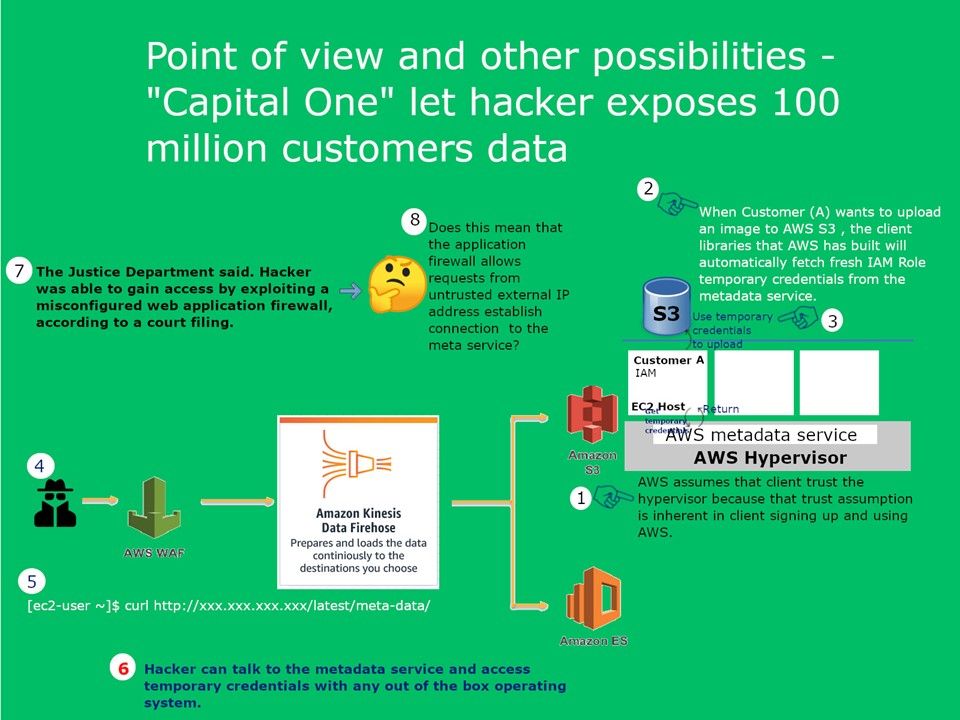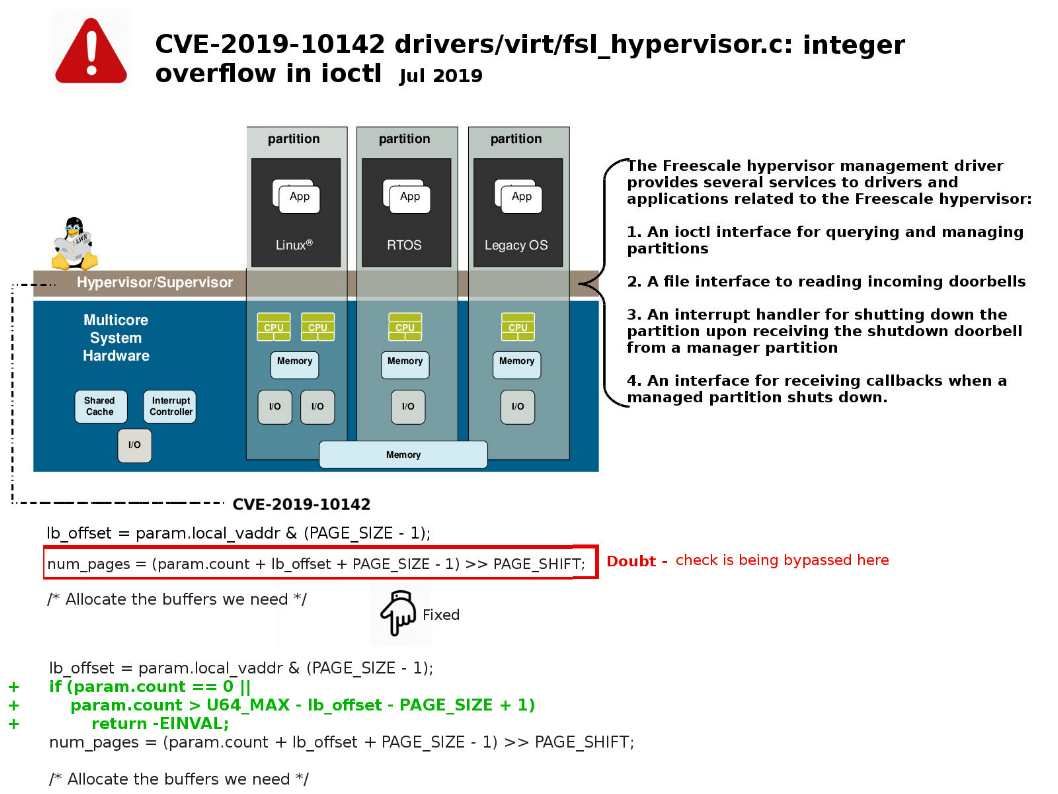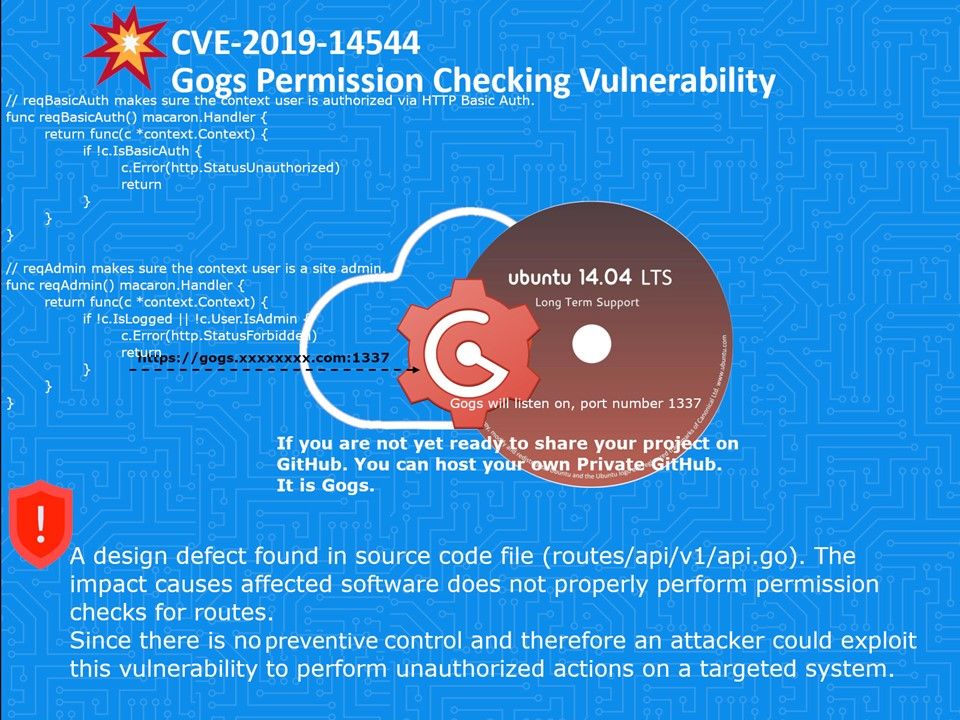
Preface: If you are not yet ready to share your project on GitHub. You can host your own Private GitHub. It is Gogs.
Product background: The goal of Gogs is to make the easiest, fastest, and most painless way of setting up a self-hosted Git service. So all the design concept, program code and perhaps intellectual properties all keep in this place. Since the intension is not go for public and therefore it will be installed on private cloud or a single machine.
Vulnerability details: A design defect found in source code file (routes/api/v1/api.go). The impact causes affected software does not properly perform permission checks for routes.
Since there is no preventive control and therefore an attacker could exploit this vulnerability to perform unauthorized actions on a targeted system. Should you have interested of this issue, see top right hand side of the diagram. You will find part of the enhancement features. Perhaps you will speculate what is the actual problem.
Remedy – See url https://github.com/gogs/gogs/blob/master/routes/api/v1/api.go