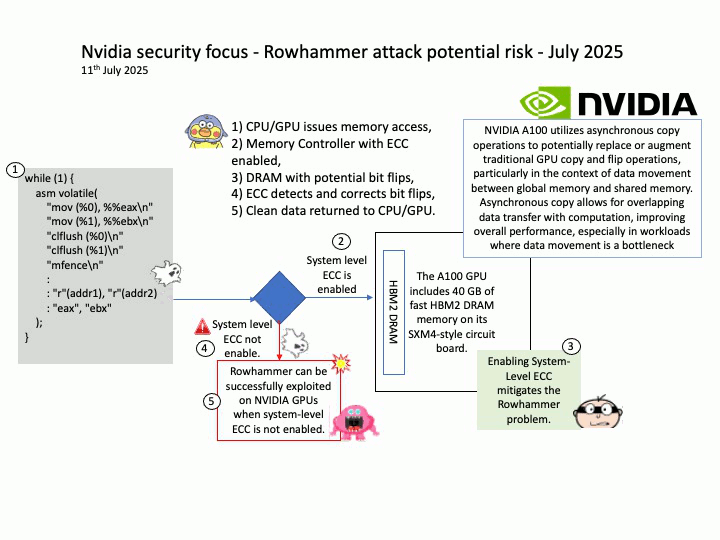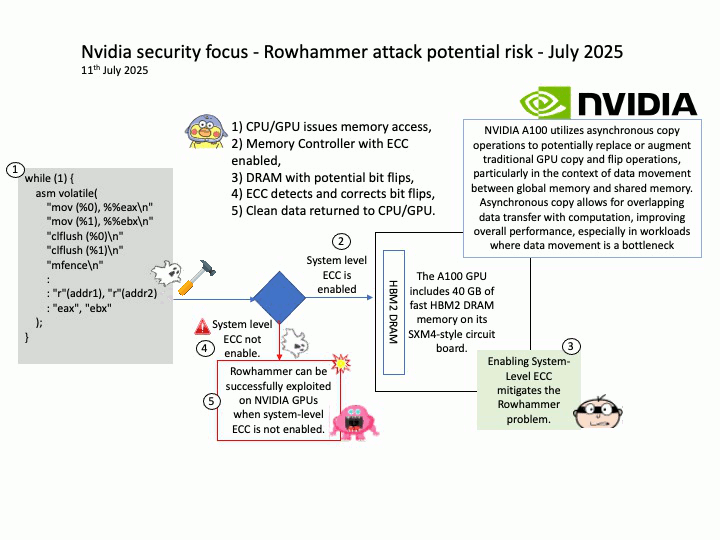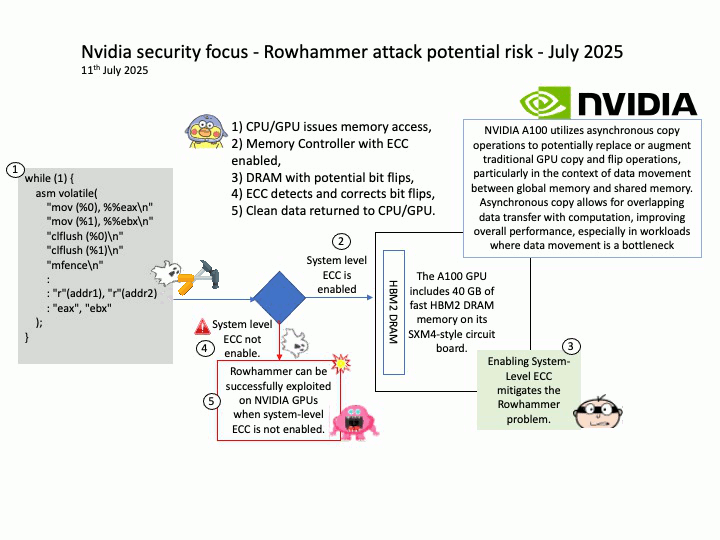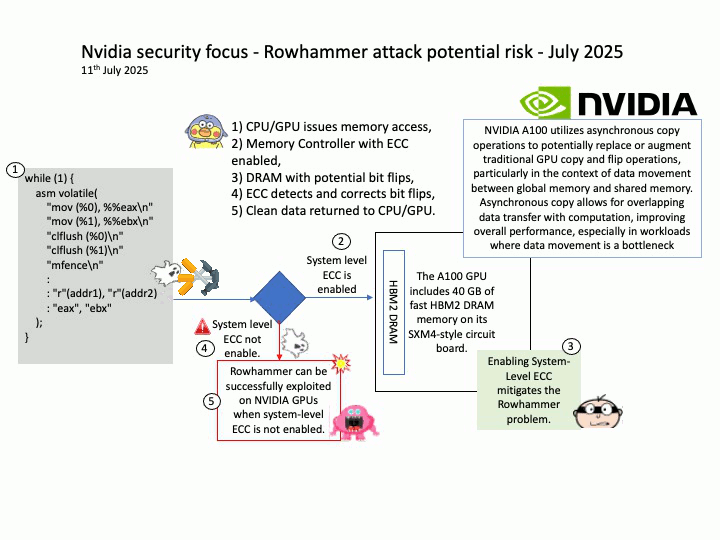
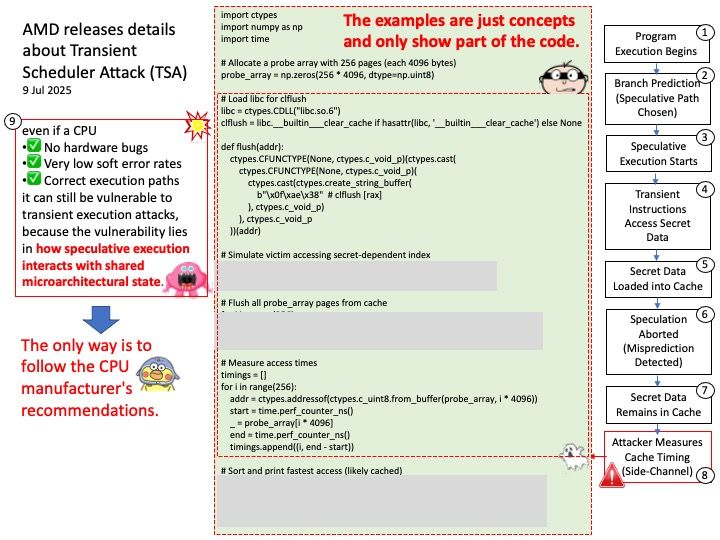
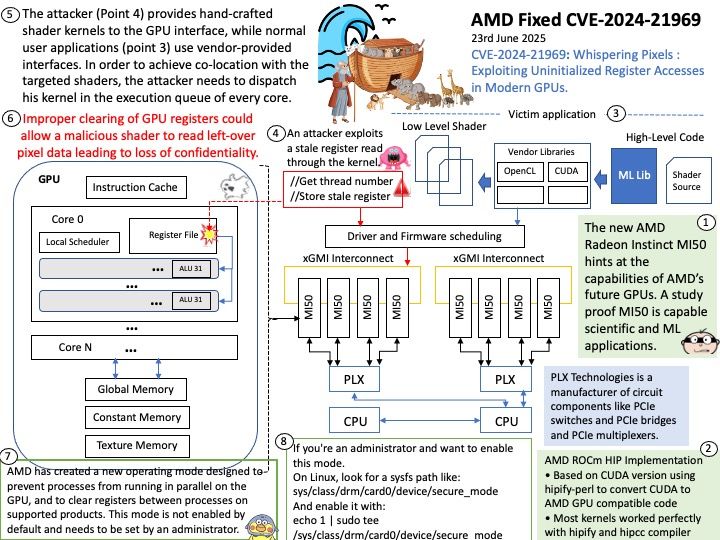
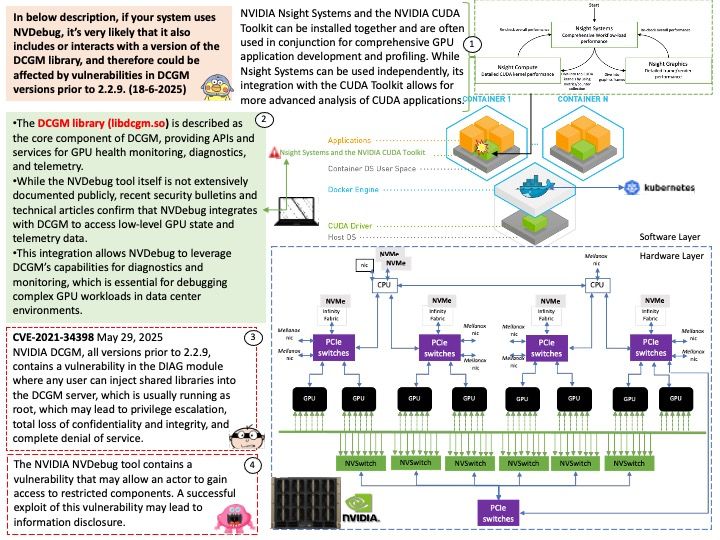
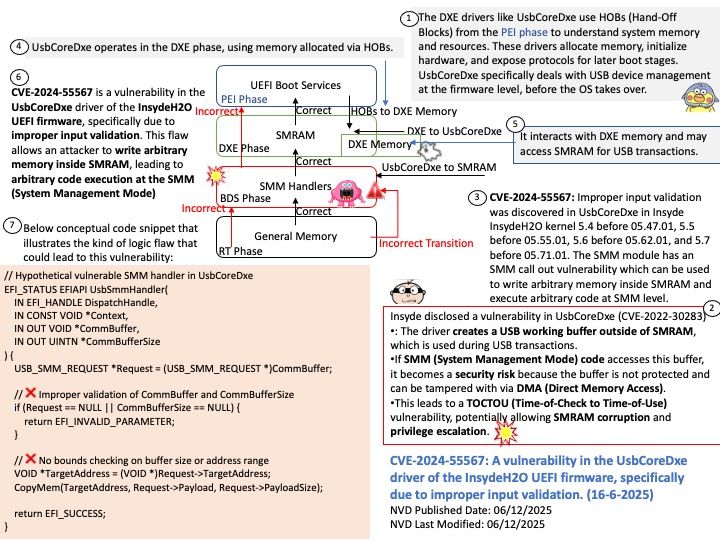
Preface: The main consequence of an RDSEED failure on AMD Zen 5 processors is instability, crashes, and potentially corrupted data, as this issue affects the processor’s ability to generate high-quality random numbers for cryptography and other sensitive tasks. This has led to the development of Linux kernel patches to temporarily disable RDSEED on affected Zen 5 CPUs until AMD provides a permanent hardware or firmware fix.
Background: RDSEED is a CPU instruction that provides high-entropy random numbers directly from a hardware entropy source, such as the Intel Digital Random Number Generator. It is designed to be used to seed other pseudo-random number generators (PRNGs) for cryptographic applications, ensuring a secure and unpredictable starting point.
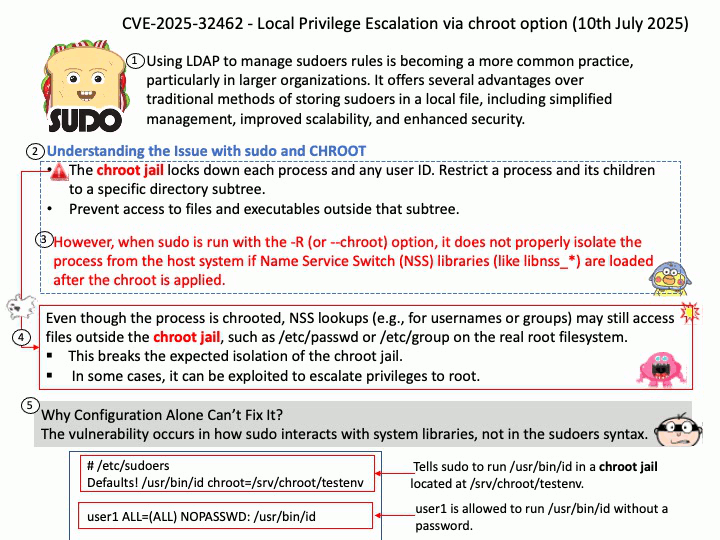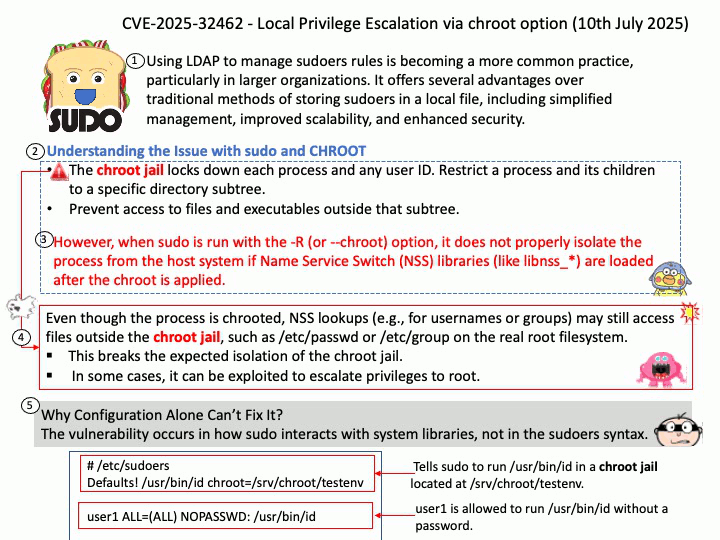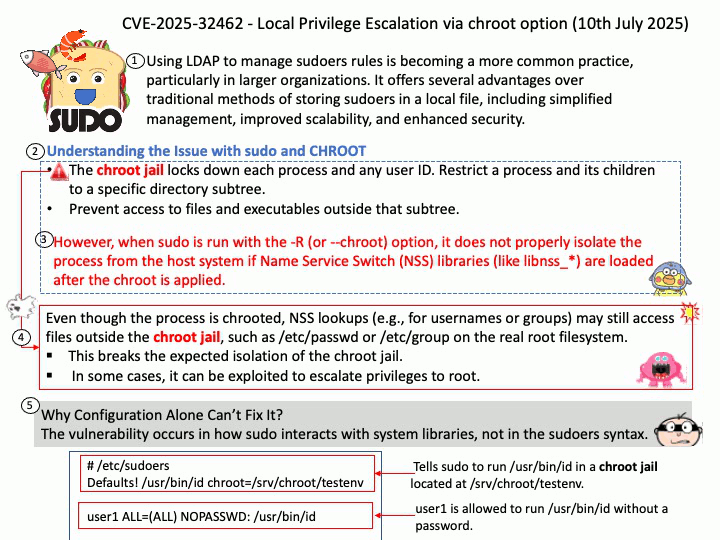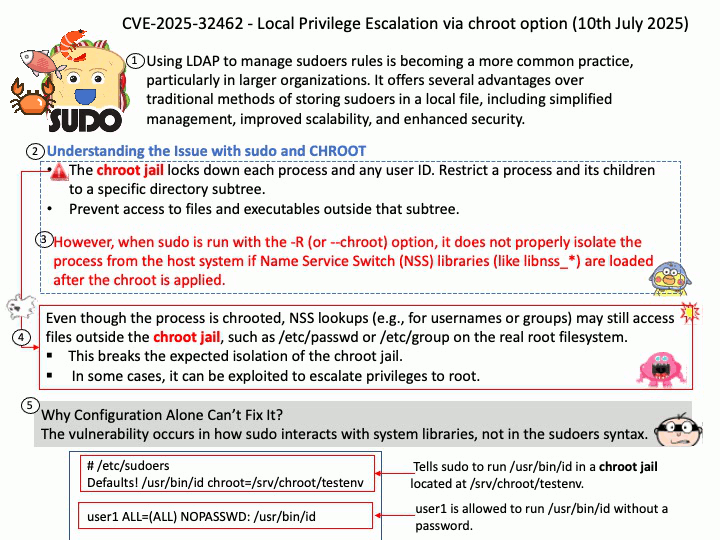
RDSEED is a CPU instruction that provides high-entropy random numbers directly from a hardware entropy source, such as the Intel Digital Random Number Generator. It is designed to be used to seed other pseudo-random number generators (PRNGs) for cryptographic applications, ensuring a secure and unpredictable starting point.
Vulnerability Details: AMD was notified of a bug in “Zen 5” processors that may cause the RDSEED instruction to return 0 at a rate inconsistent with randomness while incorrectly signaling success (CF=1), indicating a potential misclassification of failure as success. This issue was initially reported publicly via the Linux kernel mailing list and was not submitted through AMD’s Coordinated Vulnerability Disclosure (CVD) process.
AMD has determined that the 16-bit and 32-bit forms of the RDSEED instruction on “Zen 5” processors are affected. The 64-bit form of RDSEED is not affected. AMD plans to release mitigations for this vulnerability.
Official announcement: Please refer to the link for details –
https://www.amd.com/en/resources/product-security/bulletin/amd-sb-7055.html