CVE-2024-21969: Whispering Pixels: Exploiting Uninitialized Register Accesses in Modern GPUs.
Preface: How to Enable Secure GPU Mode (Register Clearing)
- This mode is supported on the following AMD GPUs:
- Radeon RX 5000, 6000, 7000, 9000 series
- Radeon PRO W5000, W6000, W7000 series
- Radeon AI PRO 9000 series
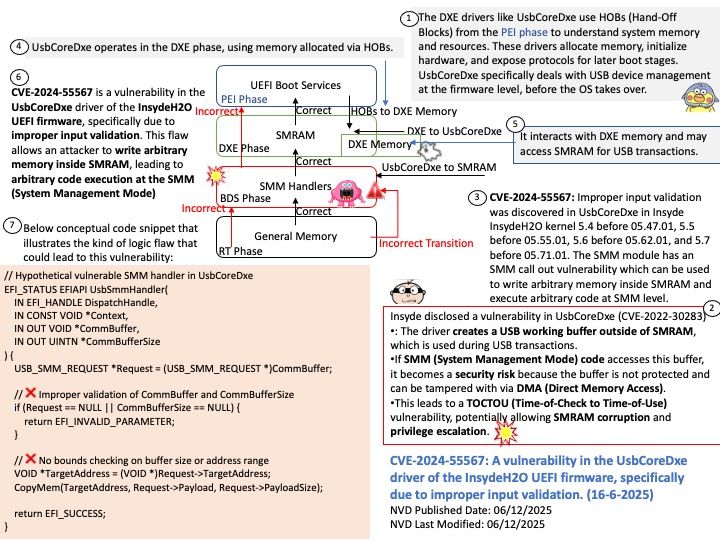
- Radeon VII, RX Vega
- Instinct MI210, MI250, MI300X, etc.
Background: The proliferation of graphics processing units (GPUs) has brought unprecedented computing power.
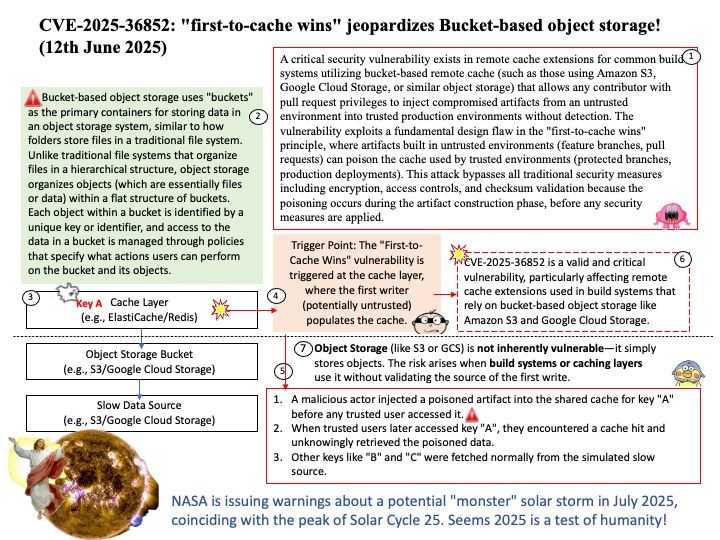
Multiple register-based vulnerabilities found across different GPU implementations.
So-called whisper pixels. The vulnerability poses unique challenges to an adversary due to opaque scheduling and register remapping algorithms present in the GPU firmware, complicating the reconstruction of leaked data.
GPU Programming: An application has to use vendor- provided libraries in order to translate a shader from its high-level source code to an architecture-dependent binary code. Vendors provide these libraries for a variety of high-level languages.
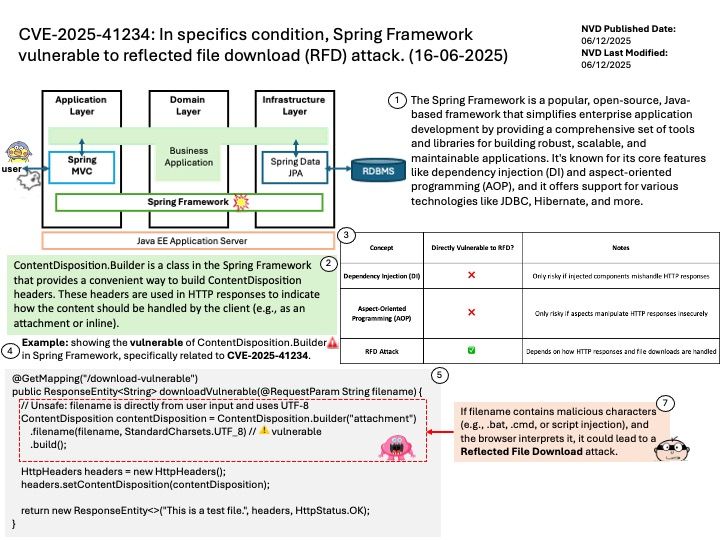
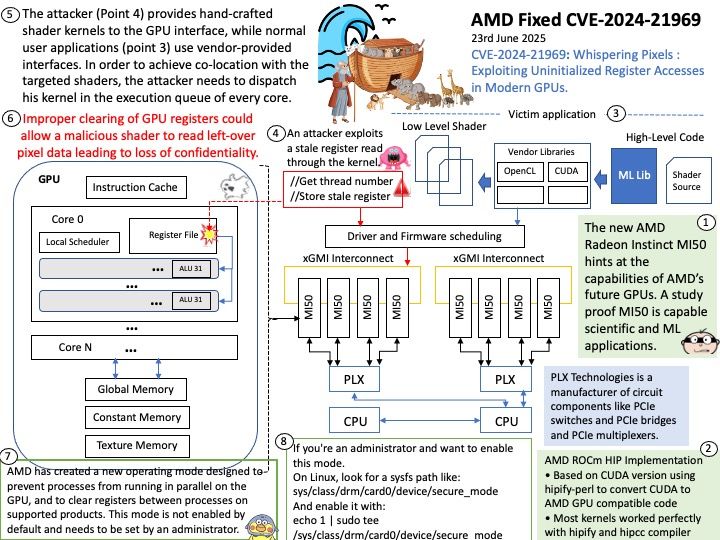
Vulnerability details: Improper clearing of GPU registers could allow a malicious shader to read left-over pixel data leading to loss of confidentiality.
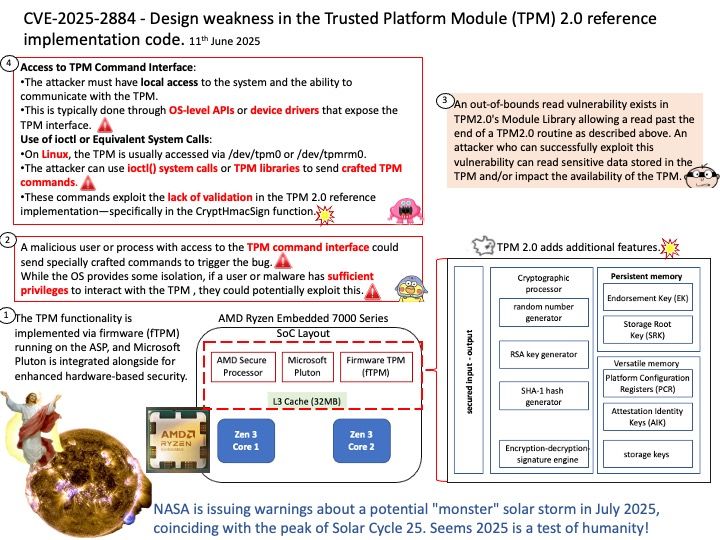
Mitigation (13th Aug 2024): AMD plans to create a new operating mode designed to prevent processes from running in parallel on the GPU, and to clear registers between processes on supported products.
Last Updated Date (23-06-2025): AMD has created a new operating mode designed to prevent processes from running in parallel on the GPU, and to clear registers between processes on supported products. This mode is not enabled by default and needs to be set by an administrator. AMD expects performance impacts if the new mode is enabled in environments where multiple processes would have been running simultaneously on the GPU. The performance impact will be related to the number of processes that would have been running in parallel. Additionally, a lesser performance impact may arise due to the additional clearing of registers between processes.
Instructions for enabling the new mode can be found in the relevant release notes and/or product documentation.
AMD started rolling out mitigation options beginning in May 2024 through applicable driver updates.
Official announcement: Please refer to the website for details – https://www.amd.com/en/resources/product-security/bulletin/amd-sb-6013.html