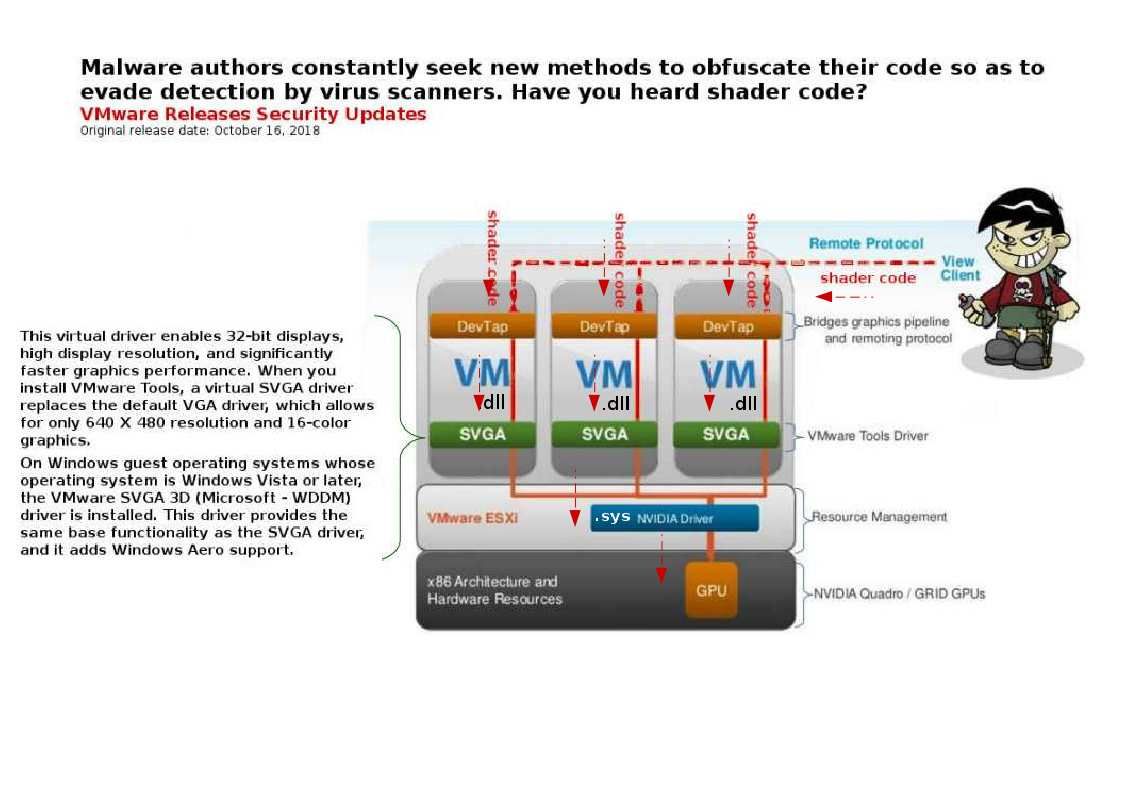
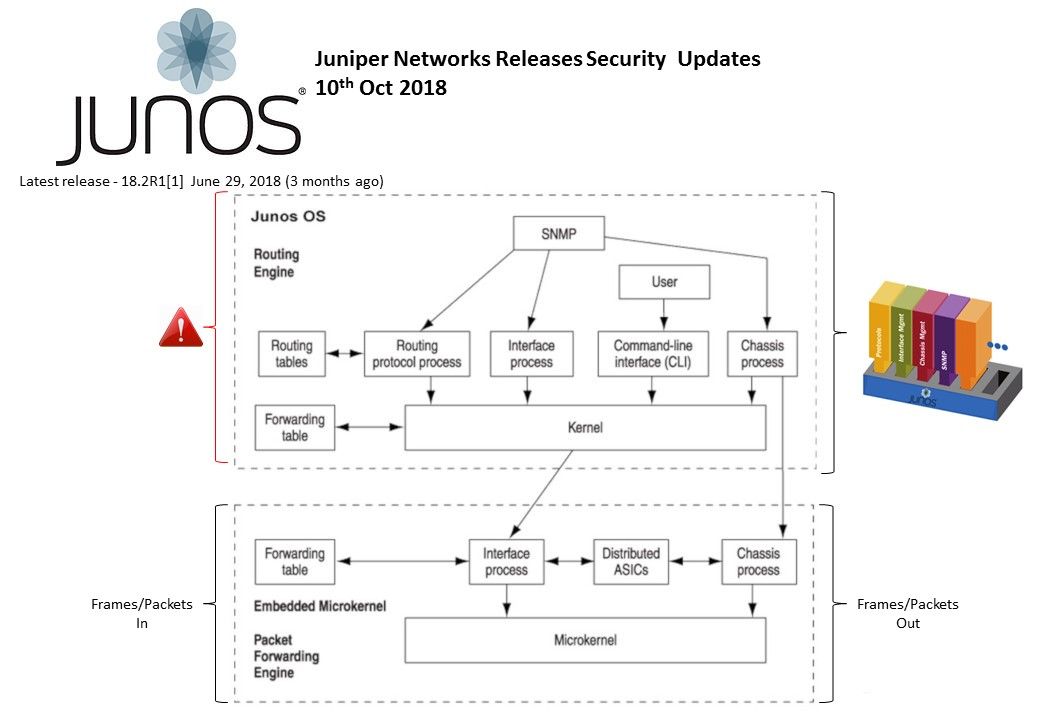
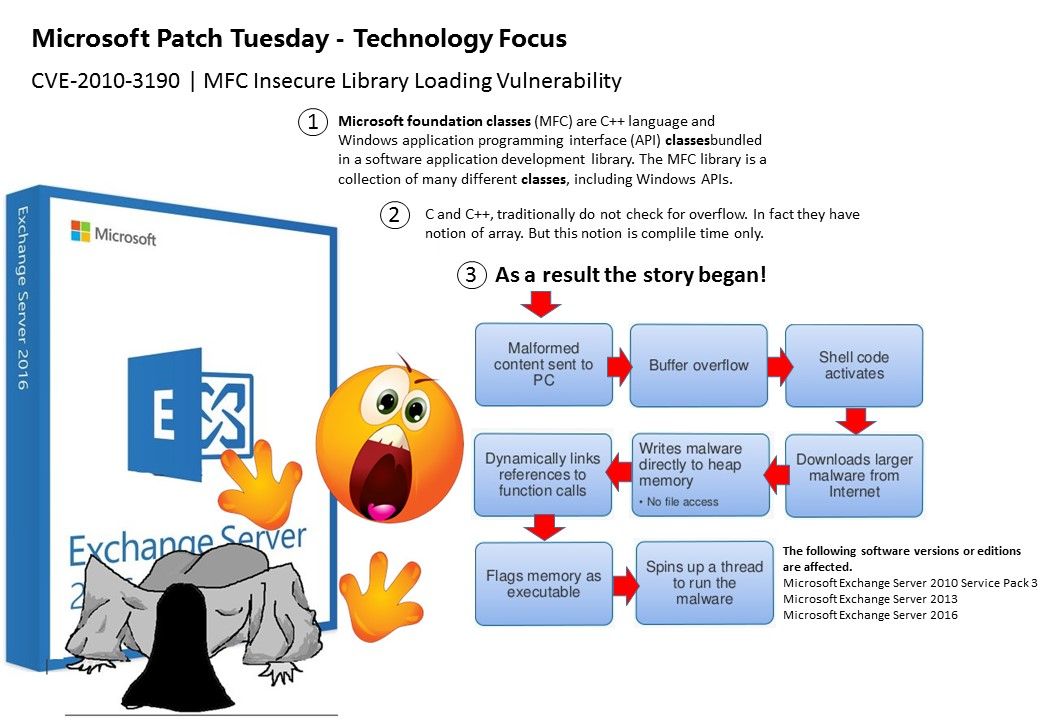
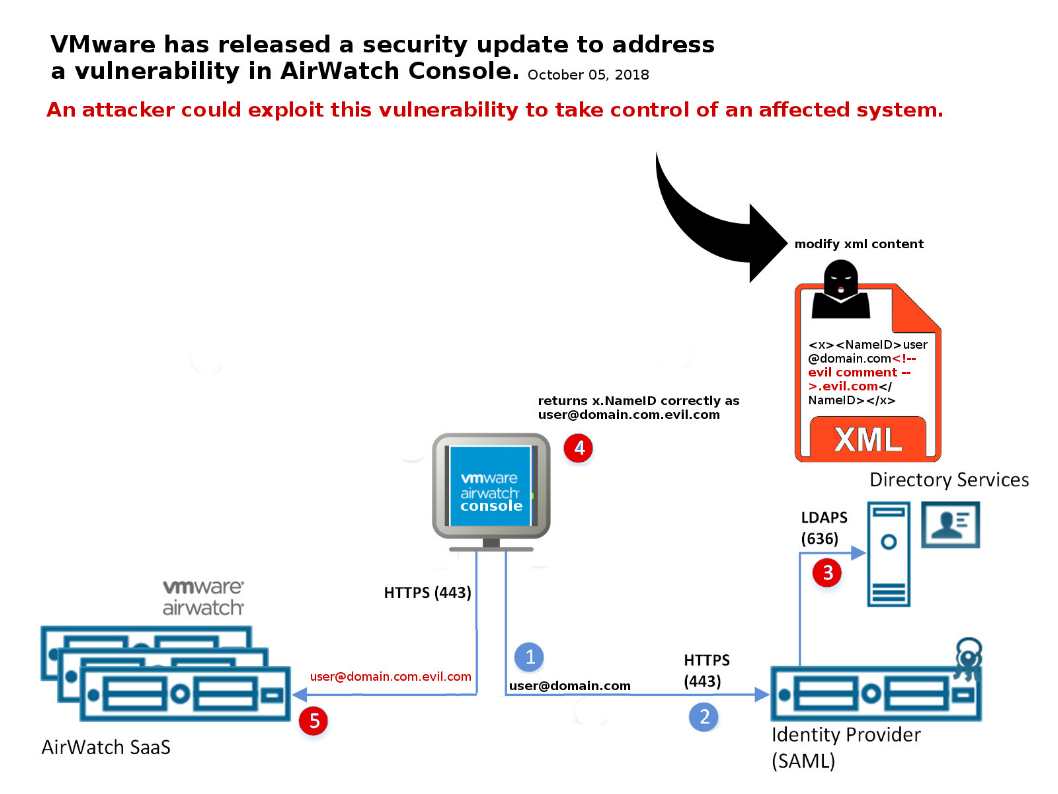
The Yammer desktop app is a native client for Mac and Windows with the full functionality of Yammer. Along with streamlined log in and SSO support, the app integrates with native operating system capabilities such as notifications, shortcuts, and launch on startup.
Microsoft announce vulnerability occurs today. But it looks that it is a old bug found 2013.
Should you have interest of the bud details. Attached diagram can provide hints to you for reference.
If you are going to do the remediation, please refer to below url (Official announcement)
CVE-2018-8569 | Yammer Desktop Application Remote Code Execution Vulnerability
https://portal.msrc.microsoft.com/en-US/security-guidance/advisory/CVE-2018-8569