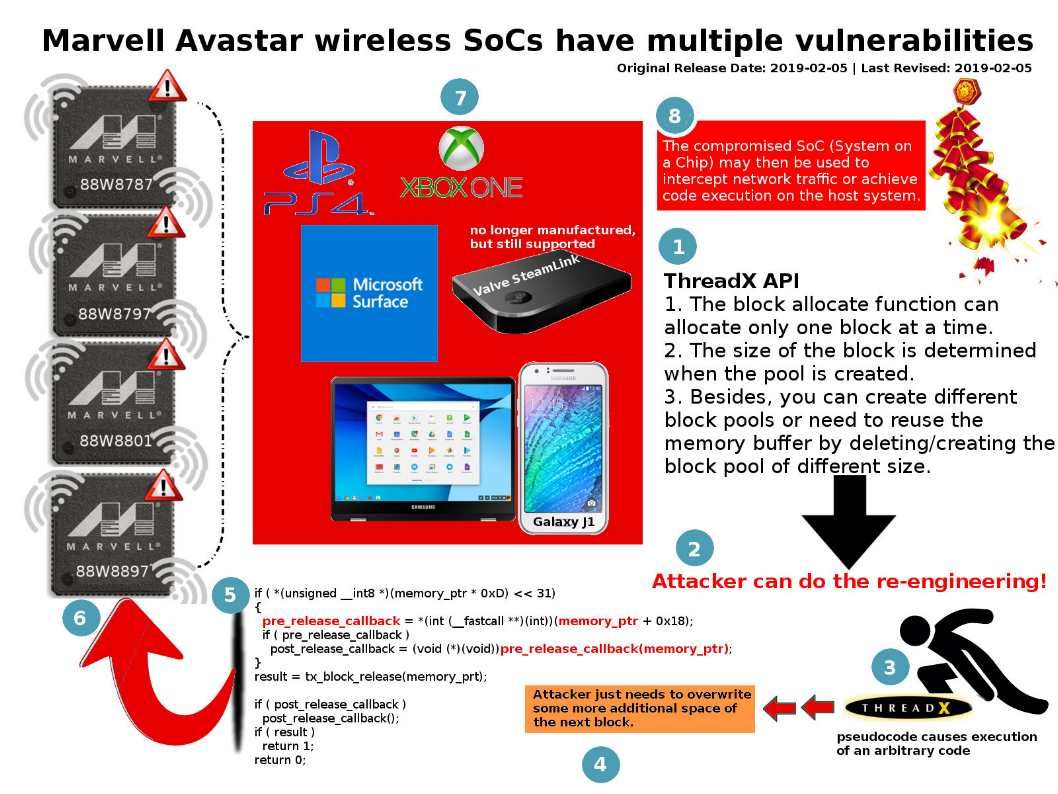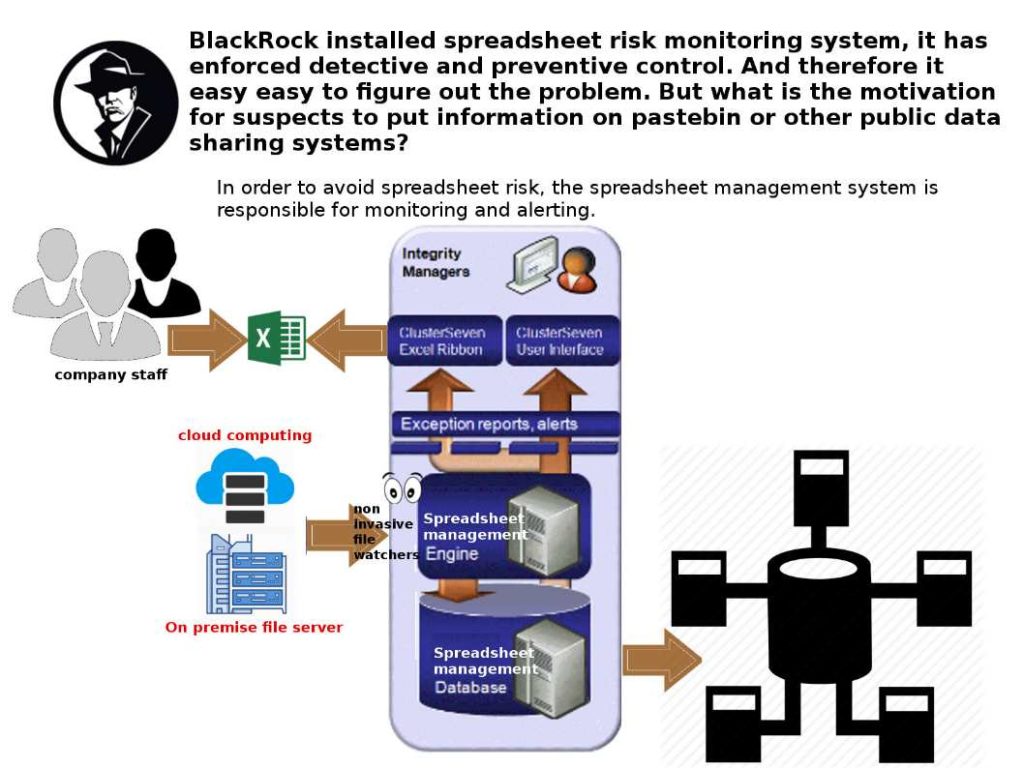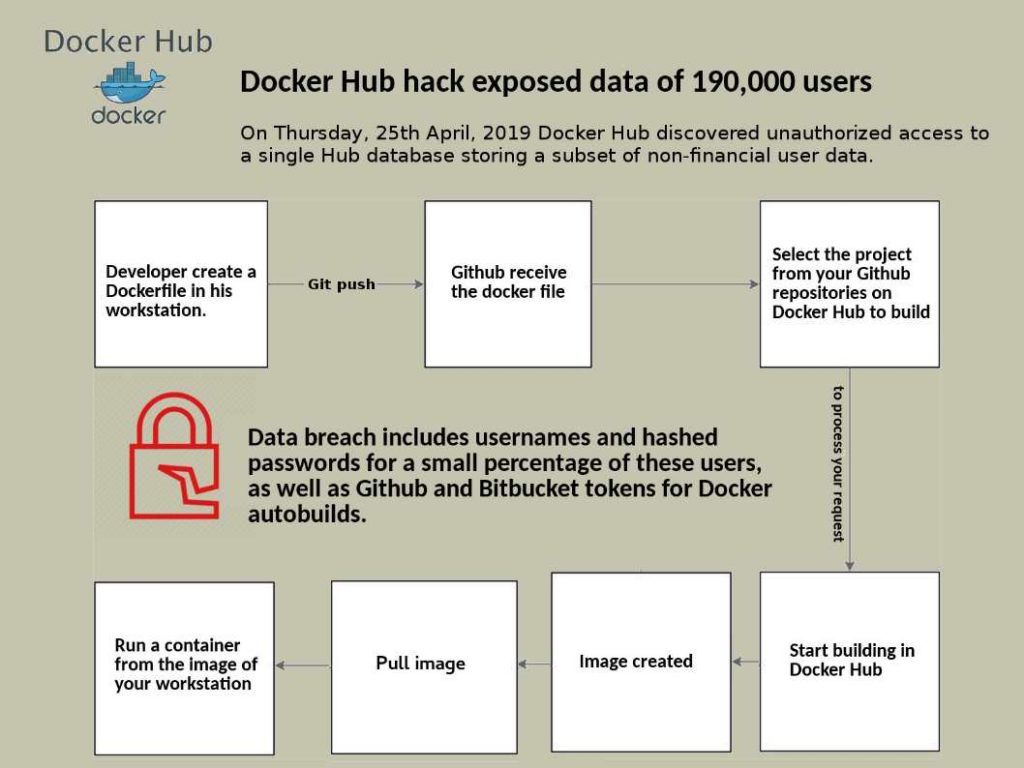
Preface: Docker Hub hack exposed data of 190,000 users
Incident details: On Thursday, 25th April, 2019 Docker Hub discovered unauthorized access to a single Hub database storing a subset of non-financial user data.
Impact: Data breach includes usernames and hashed passwords for a small percentage of these users, as well as Github and Bitbucket tokens for Docker autobuilds.
Doubt: Since Docker provides mirror service for Docker users especially Greater China area. Is there any problem found in this place?
Headline News: https://www.zdnet.com/article/docker-hub-hack-exposed-data-of-190000-users/