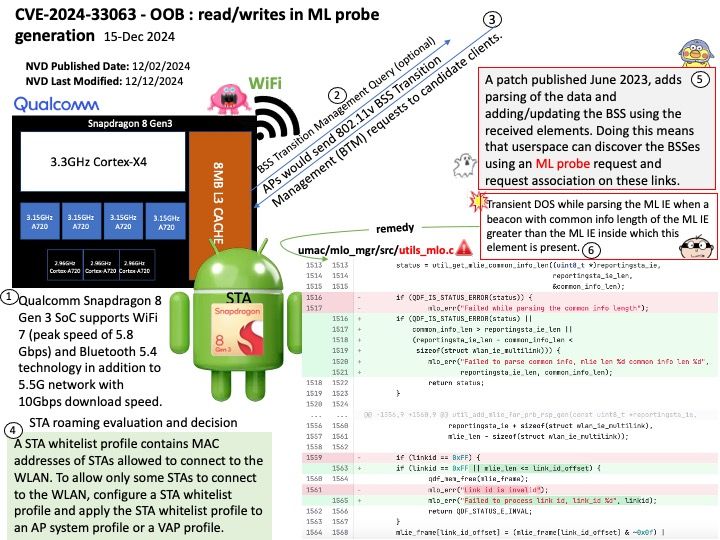
Preface: A patch published June 2023, adds parsing of the data and adding/updating the BSS using the received elements. Doing this means that userspace can discover the BSSes using an ML probe request and request association on these links.
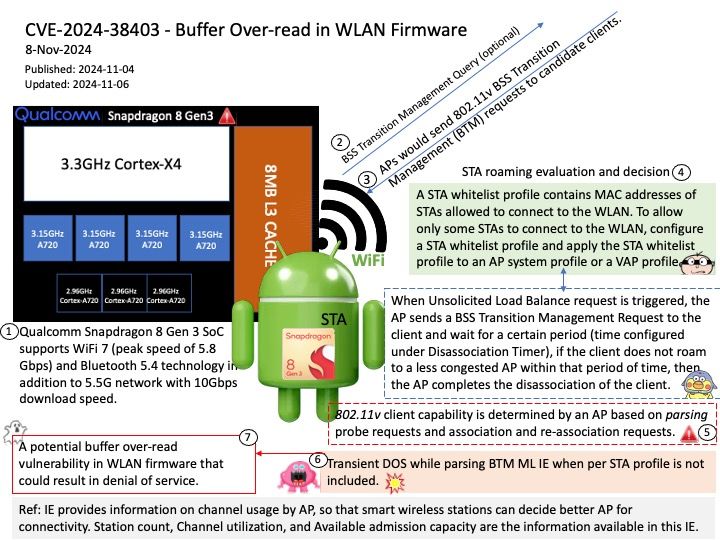
Background: IE provides information on channel usage by AP, so that smart wireless stations can decide better AP for connectivity. Station count, Channel utilization, and Available admission capacity are the information available in this IE.
The term QBSS is used in wireless networks supporting the IEEE 802.11e Quality of Service enhancement. It defines a Basic Service Set supporting a QAP and a number of QSTA.
When enabled, appends QBSS IE in Management frames. This IE provides information of channel usage by AP, so that smart wireless station can decide better AP for connectivity. Station count, Channel utilization and Available admission capacity are the information available in this IE.
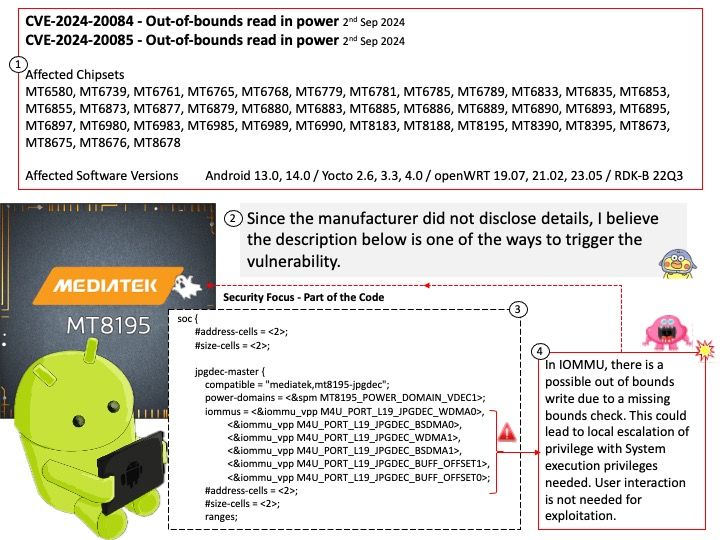
Vulnerability details: Transient DOS while parsing the ML IE when a beacon with common info length of the ML IE greater than the ML IE inside which this element is present.
Official announcement: Please refer to the link for details –