Preface: In ancient China, there was not only ancient times. Before ancient times, there was a ancient era that we could difficult to explore. With regard to the myth book of China, because of the many legends and myths left. It let me tirelessly exploring.

Background of the Shan Hai Jing:
Shan Hai Jing《山海經》, Chinese pre-Qin (先秦 221 BC) ancient books. A book with an unbelievable ancient historical details. So the Chinese people general opinion categorized that it is a myth book. The are different kinds of strange monsters with total seventy five recorded in “Shan Hai Jing” .
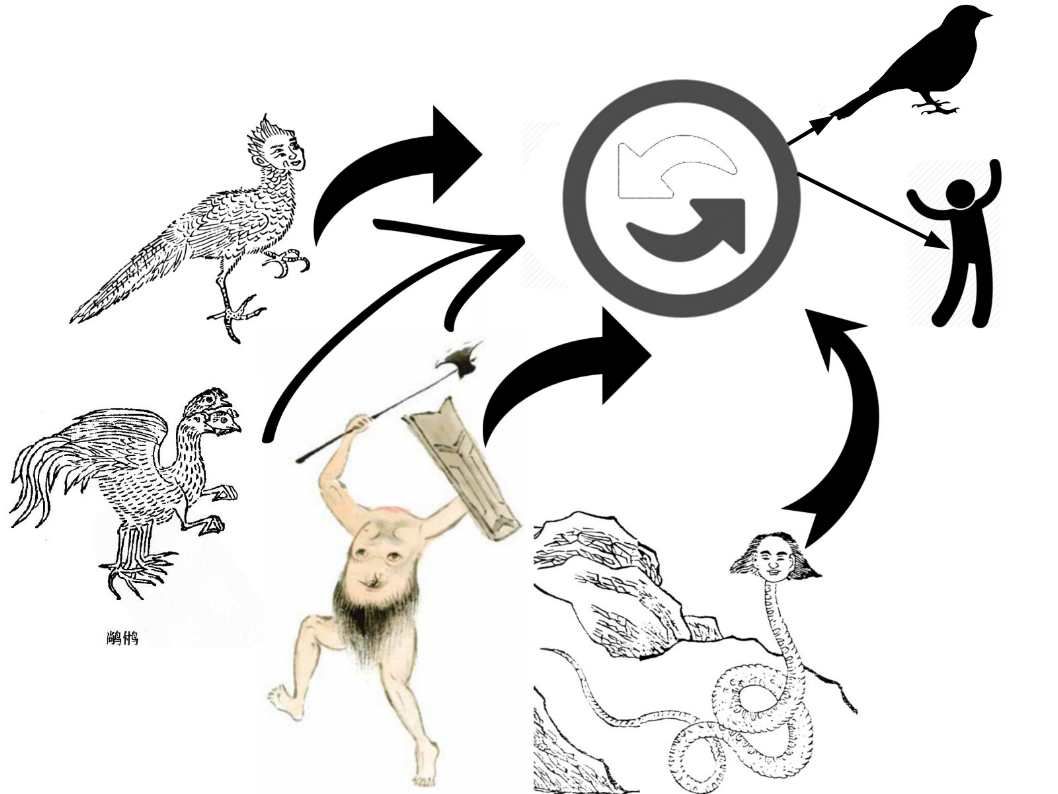
The pictures in Shan Hai Jing are strange. If you read the book, you will found that all the animals looks different compaing with our modern world. For instance a chicken have three legs and double heads. Even though a character looks like a human being but without head. As far as I remember a TV program interview with a professor (Asia country). When the journalist mentions the Shan Hai Jing. Professor reply with simple. It is not true.
Creation of mankind

With different of civilizations in our earth. However, the definition of human creation have similar of ideas. It is create by god? Do you have doubt? Whether it is create by bio-technology (DNA genes)?
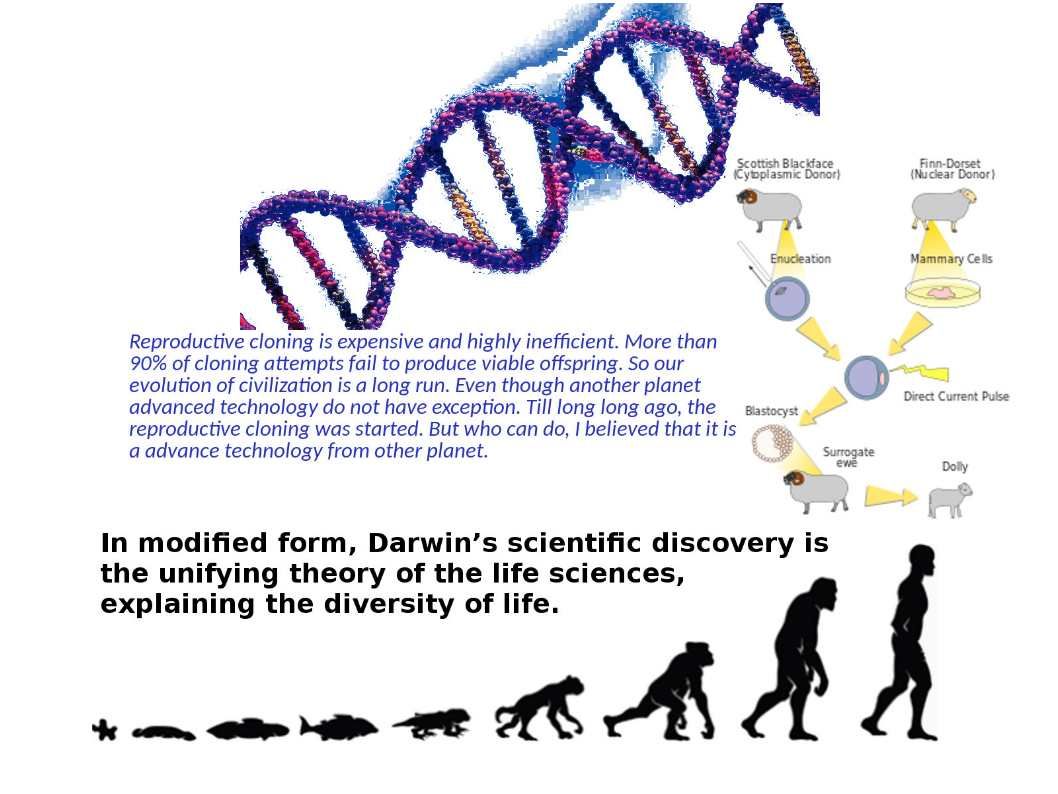
In modified form, Darwin’s scientific discovery is the unifying theory of the life sciences, explaining the diversity of life. The mankind evolution discovered by darwin, it coincidence proof the relationship of Shan Hai Jing between mankind.
Reproductive cloning is expensive and highly inefficient. More than 90% of cloning attempts fail to produce viable offspring. So our evolution of civilization is a long run. Even though another planet advanced technology do not have exception. Till long long ago, the reproductive cloning was started. But who can do, I believed that it is a advance technology from other planet. So we find special animals in myth books especially Shan Hai Jing《山海經》, this is the way I speculate that the intention of ancient Chinese people written down their live experiences.
Shan Hai Jing 《山海經》 has pictures, the text described according to the content of the picture. However, ancient pictures have been lost. The earliest pictures of Shan Hai Jing came from the Ming Dynasty. And it is a draft version not the original. Perhaps people concerns about the integrity of data (genuine)! For more details, please refer following link: https://en.wikipedia.org/wiki/Classic_of_Mountains_and_Seas
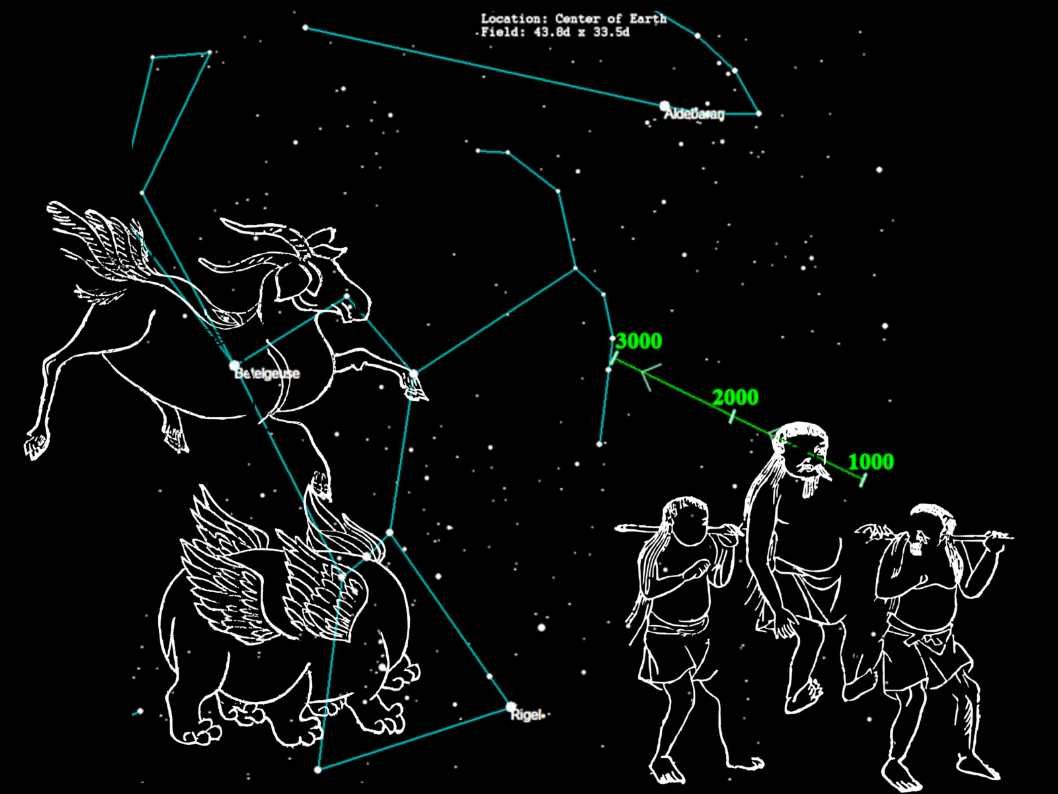
But when we compare Shan Hai Jing 《山海經》 pictures with the civilization of Babylon. Their ancient history also described monster type human and how god create man kind. The monster similar Shan Hai Jing 《山海經》 pictures ideas. The monster looks like mixed with bird, fish and wild animal (see below).
Remark: In biology, cloning is the process of producing similar populations of genetically identical individuals that occurs in nature when organisms such as bacteria, insects or plants reproduce asexually. Following the definition of Darwin evolution theory (see below):

With reference of Babylon ancient history by archeologist. Babylon was the largest city in the world c. 1770 – c. 1670 BC, and again c. 612 – c. 320 BC). The historical record of Shan Hai Jing was founded in Chinese pre-Qin (先秦 221 BC) discovered by archeologist. So I predict that the picture of record by Shan Hai Jing recorded the seen of the witness before 221 BC. From technical point of view, it match with Babylon ancient civilization. Ancient traveler from China to Babylon can go through Silk Road.
Regarding to the findings by archeologist, they believe that Shan Hai Jing 《山海經》written by Bashu巴蜀 people. Meanwhile, they share the experience through oral communications. The cultural relics shown that Bashu巴蜀 has advanced civilization. For instance Sanxingdui Ruins (三星堆遗址). Although the ancient Shu (古蜀) civilization and the two river civilizations (Euphrates River幼發拉底河, Tigris River底格里斯河) are far apart in absolute age and geographical location, there are many cultural connections and similarities between the two. Perhaps the civilization of ancient Shu State (古蜀國) has relationship with Mesopotamia.

Summary: We are living in modern world, perhaps nobody going to find out the secret of old ancient book. However it is hard to believe that clone a human or create a mankind do not requires bio-chemical technology. Above description mention that reproductive cloning is expensive and highly inefficient. More than 90% of cloning attempts fail to produce viable offspring. So our evolution of civilization is a long run. Even though another planet advanced technology do not have exception. So the advanced intelligent creature may try and error. Our mainstream of thinking that a human only have one head. Birds has one pair of wings. But before creation of everything, human do not have such thinking. So it requires to conduct Test. And therefore the strange animals and ugly monster was born in this period of time. Dinosaur has large scale of body and not suitable living in the earth. So you can say the nature do not allow they live on earth. But why some ancient civilization disappeared? For instance Chichen Itza (Maya) and Mohenjo Daro Ancient City. After this dicussion, do you interest to read Shan Hai Jing 《山海經》?
Reference A: The Yangtze(長江) River Delta, the two lakes, and the Sichuan-Yunnan region (川滇地區),which originated in the Yangtze River, are the general term for these regional civilizations. They were formed in 2000 BC, respectively, by Lingjiatan Culture 凌家灘文化- – Liangzhu Culture 良渚文化, Daxi Culture大溪文化 – Qujialing Culture屈家嶺文化 – Shijiahe Culture石家河文化, Baodun Culture 寶墩文化 – Sanxingdui Culture. After the decline of early civilization, the culture of the late Yangtze River developed Wucheng culture吳城文化, Bashu巴蜀, Jingchu荊楚, Xuguo徐國 and Wuyue吳越.
Reference B: In biology, cloning is the process of producing similar populations of genetically identical individuals that occurs in nature when organisms such as bacteria, insects or plants reproduce asexually.