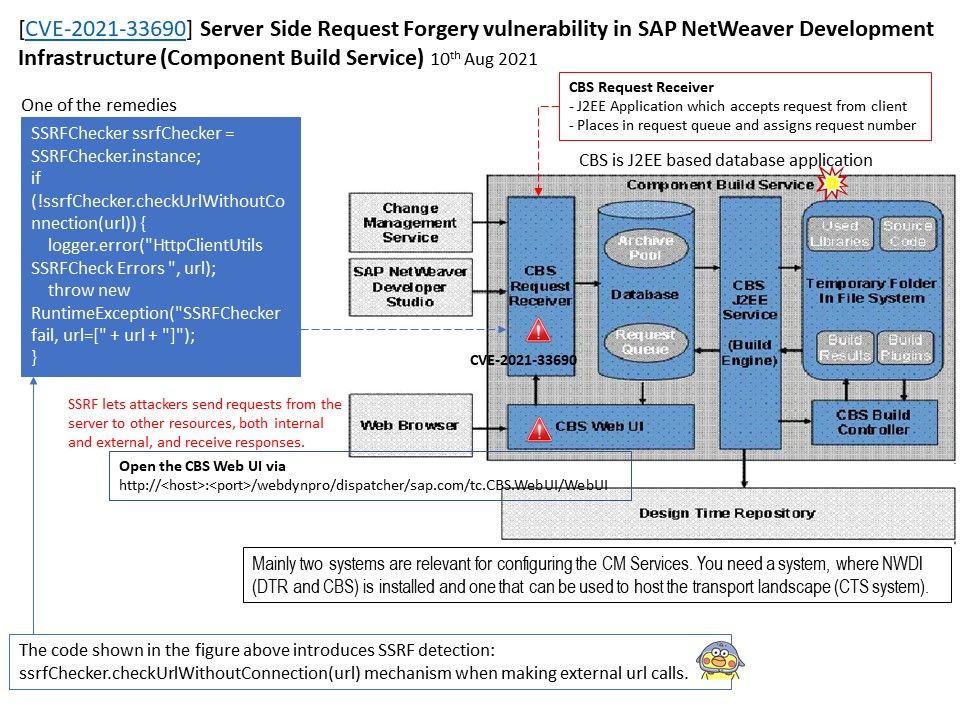
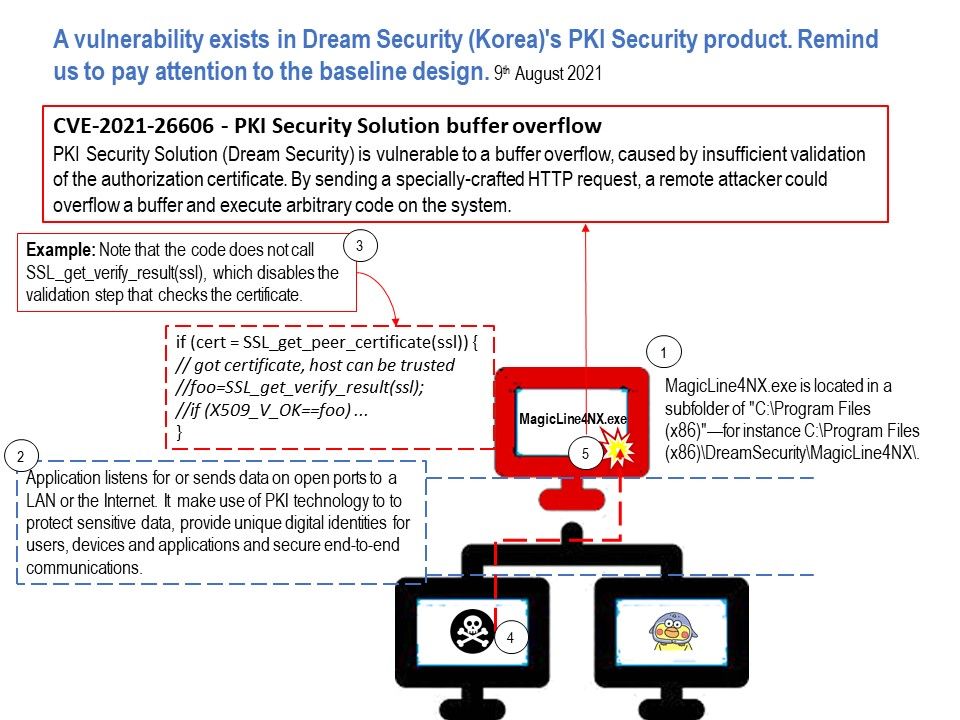
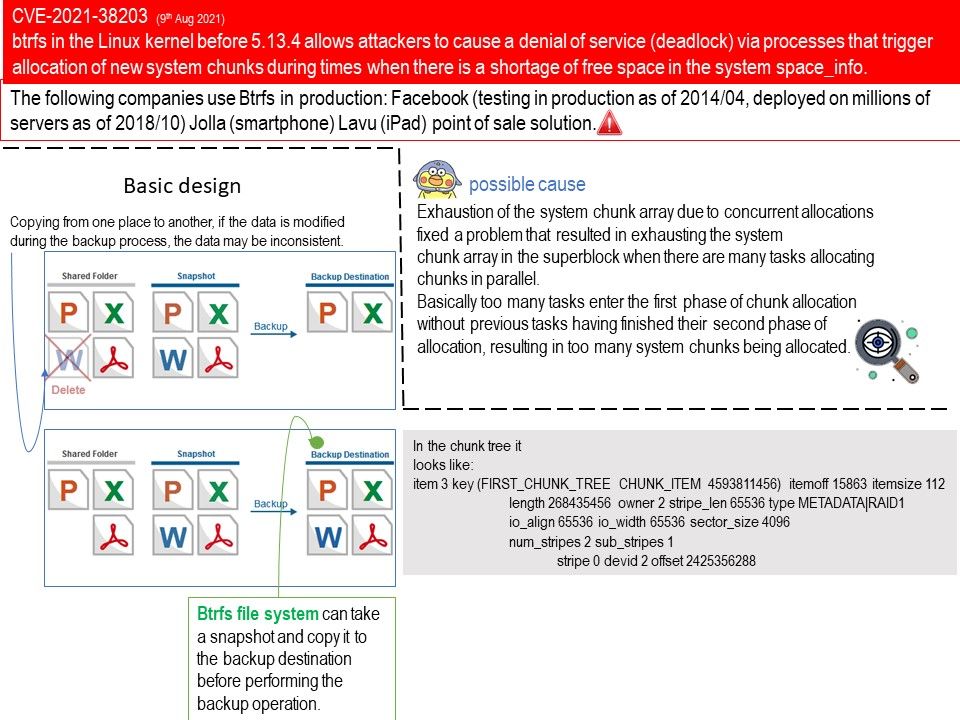
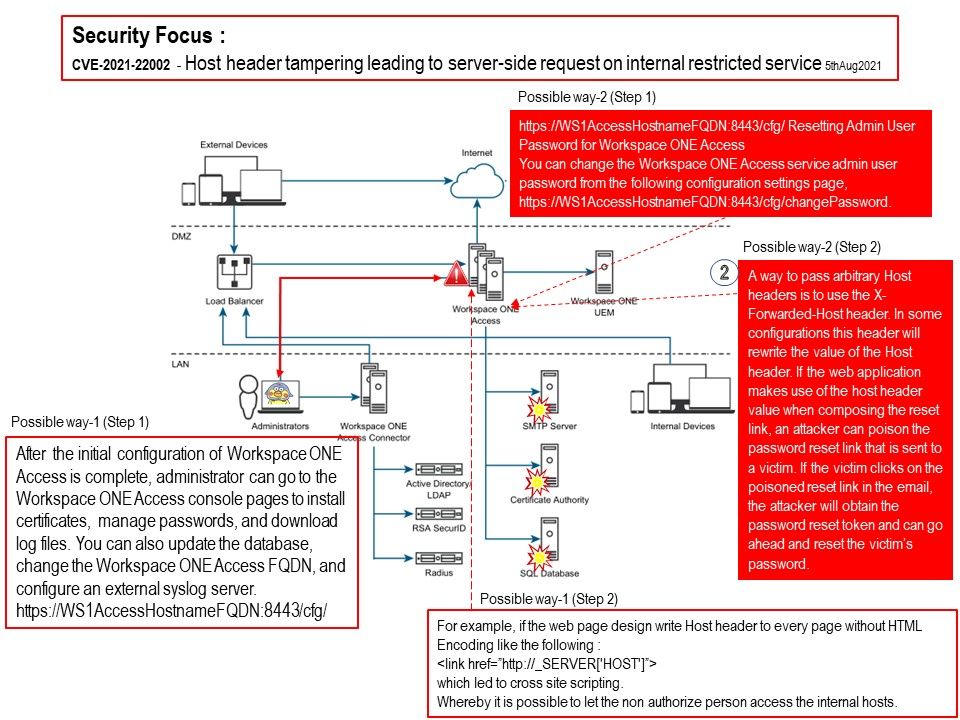
Preface: Type the following command and hit Enter. mklink /J “path to junction link” “path to target folder”. The junction link is thus created.
Background: By creating a new folder structure, changing the user’s shell folder registry key, and placing a connection point in the hierarchy,
you can open any other UsrClass[.]dat file on the system through this process.
Vulnerability details: Microsoft Windows User Profile Service Directory Junction Privilege Escalation Vulnerability (CVE-2021-34484).
An authenticated attacker who successfully exploits this vulnerability could leverage the Windows User Profile Service (ProfSvc) to load registry hives that are associated with other user accounts and potentially run programs with elevated permissions. An attacker must have valid logon credentials and be able to log on locally to exploit the vulnerability.
Official details: Please refer to the link – https://msrc.microsoft.com/update-guide/en-US/vulnerability/CVE-2021-34484