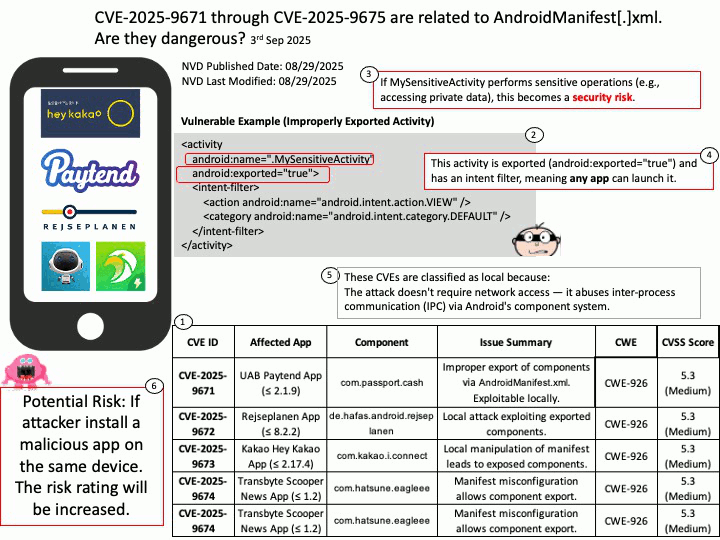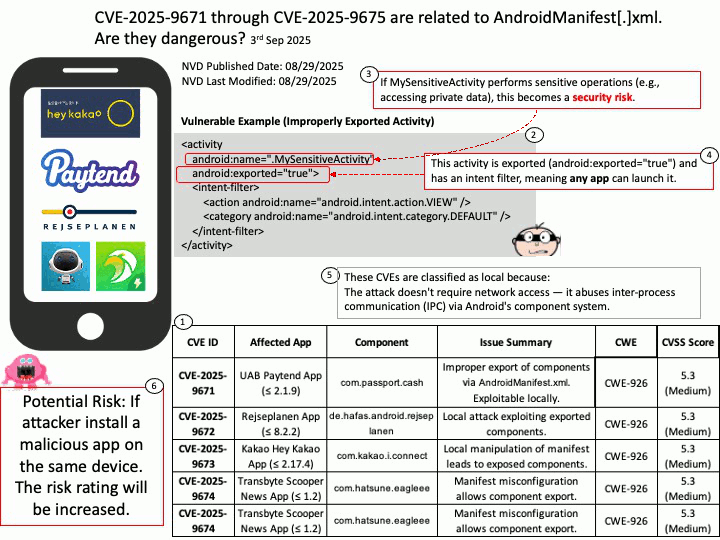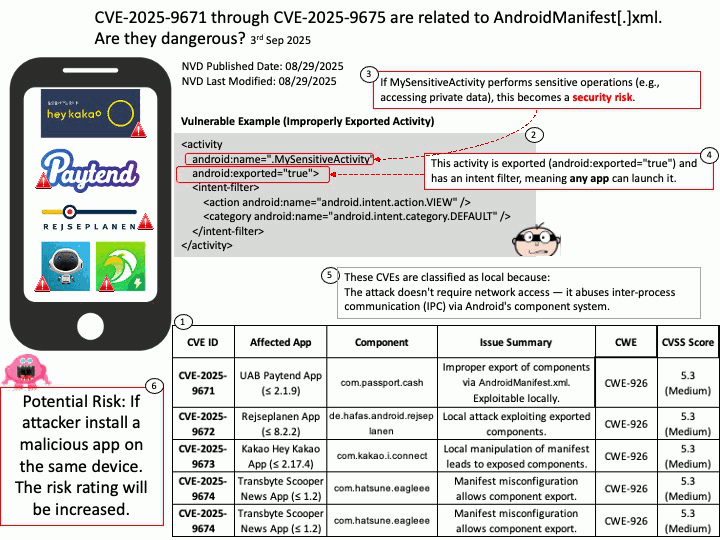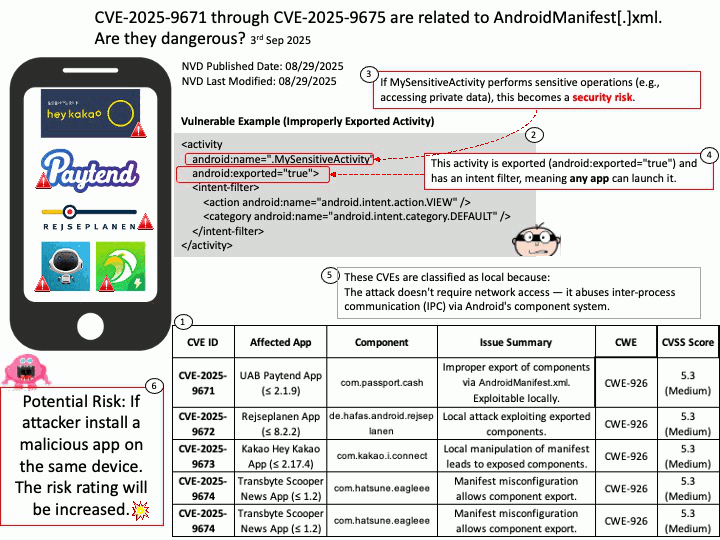
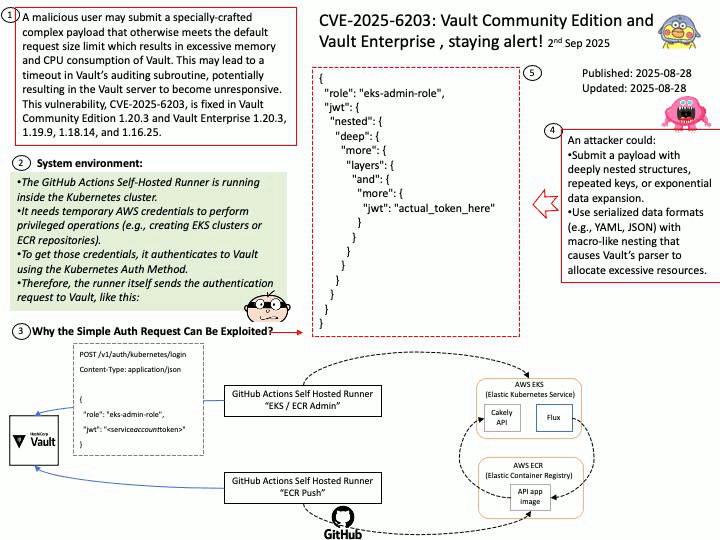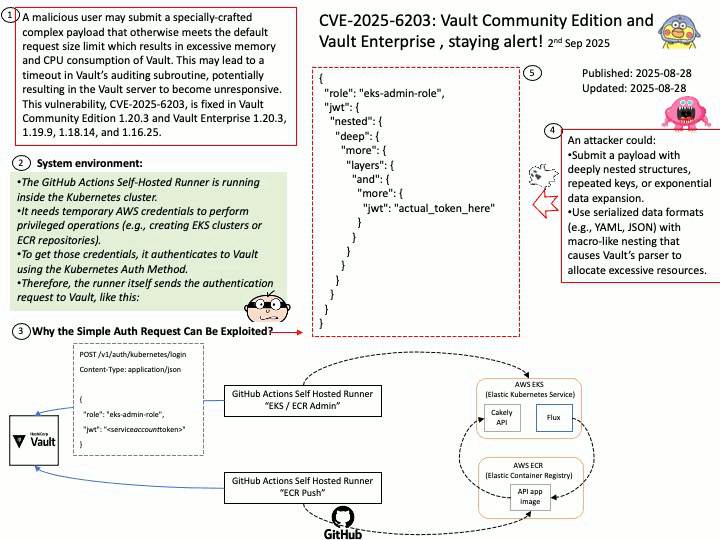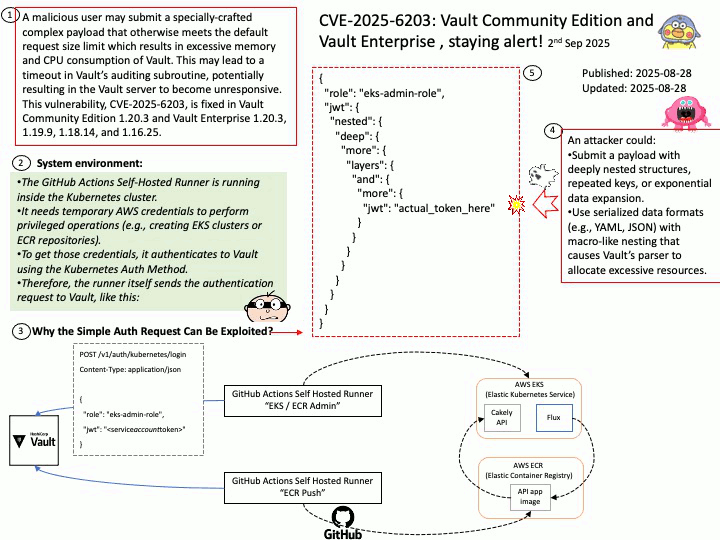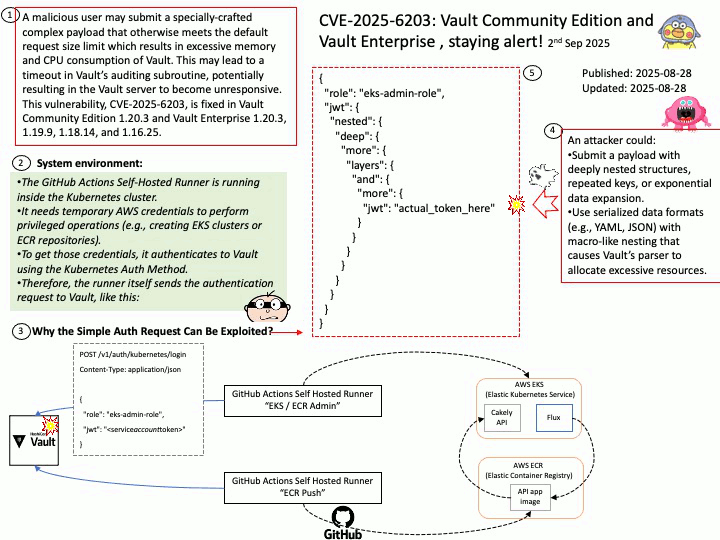
Preface: PLMNs are public networks, while private networks (NPNs) serve specific users (such as enterprises). SNPNs (Standalone NPNs) are completely independent, dedicated networks that do not rely on the functionality of public PLMNs.
Background: “Qualcomm Multi-Mode Call Processor” is a component of their Modem-RF system, which is a comprehensive 5G module-RF system designed to provide multi-band, multi-mode connectivity for various devices. These integrated solutions combine the cellular modem, RF transceiver, and RF front-end components to enable 5G, 4G LTE, and legacy cellular network support in a single, cohesive platform.
Each PLMN is identified by a PLMN ID, which includes a country code and mobile network code. The UE uses this ID to distinguish between different PLMNs.
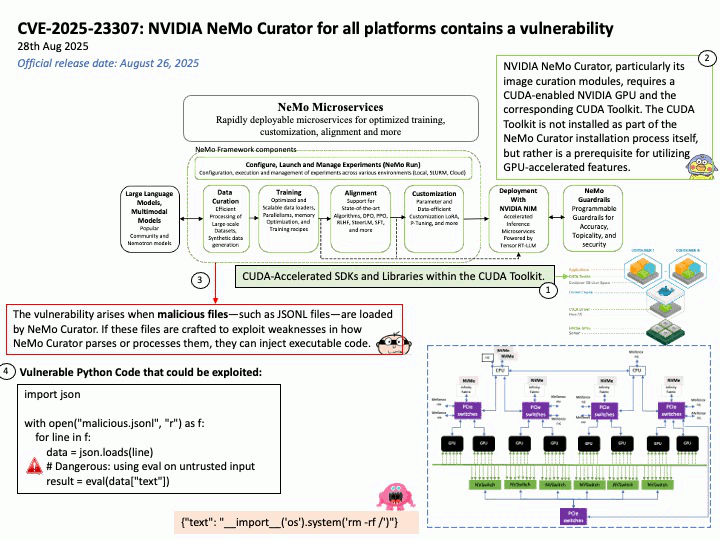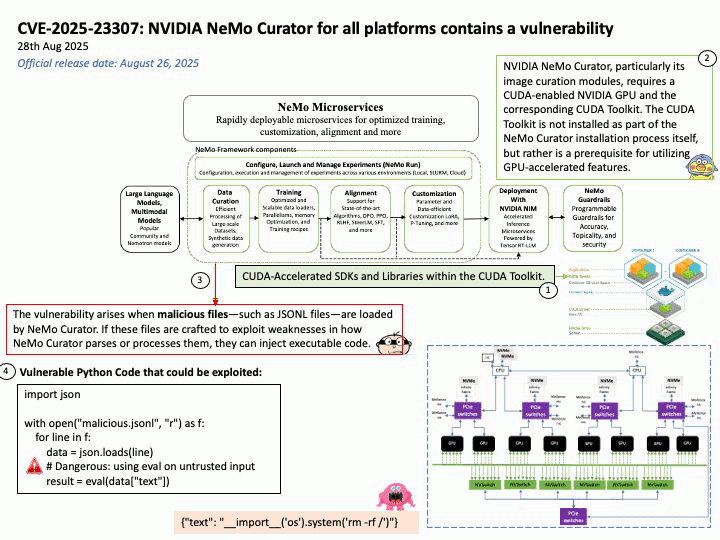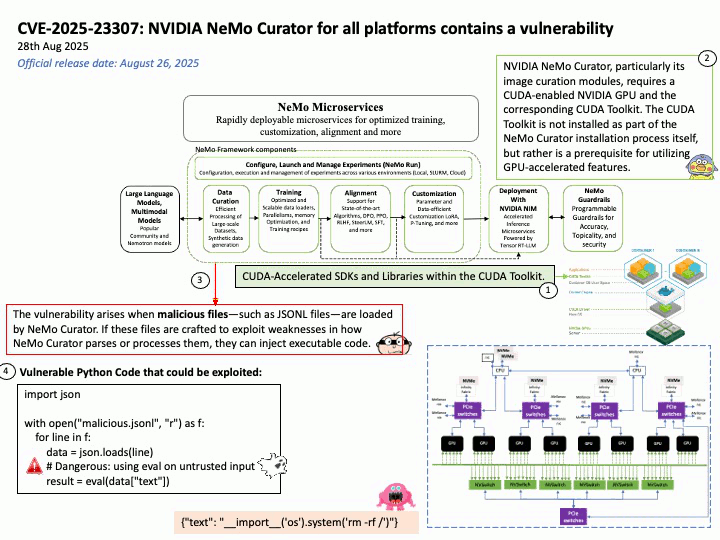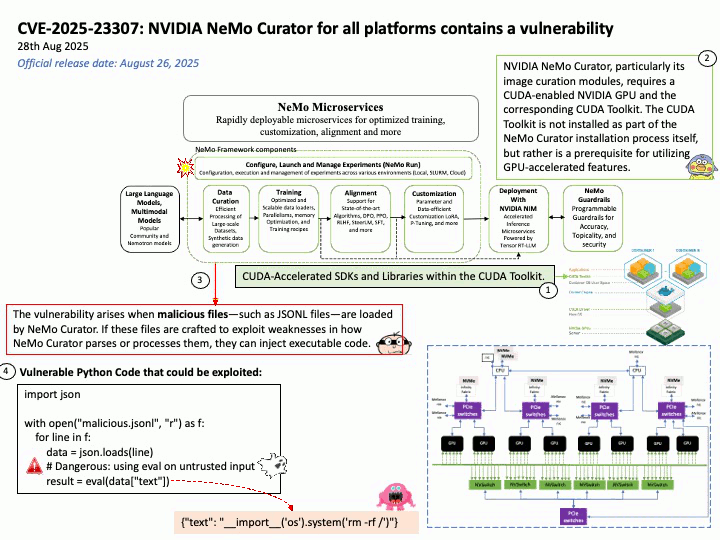
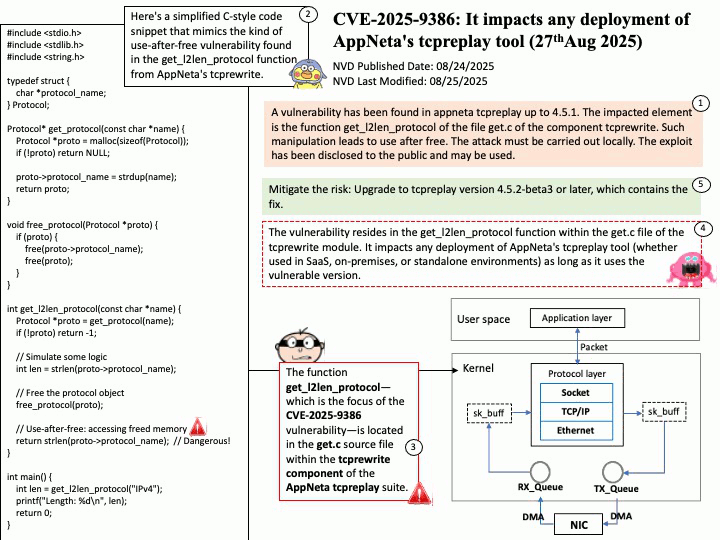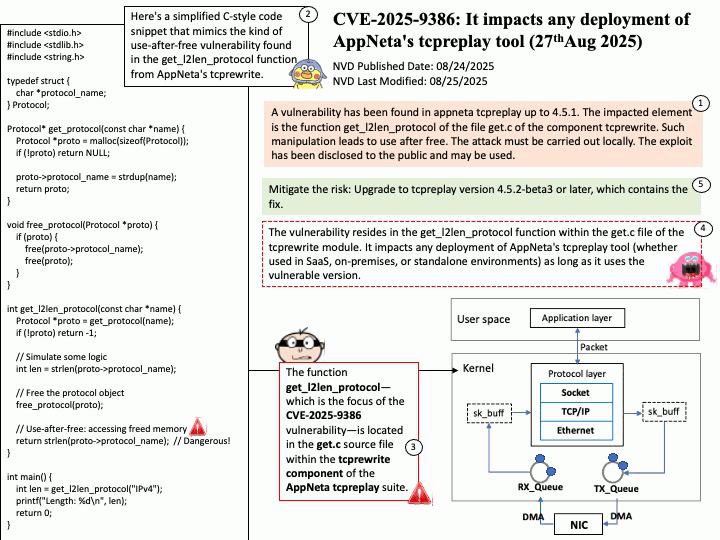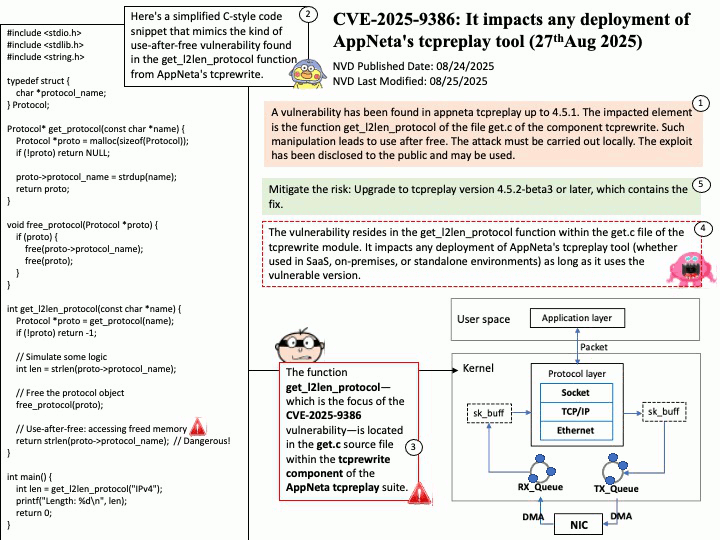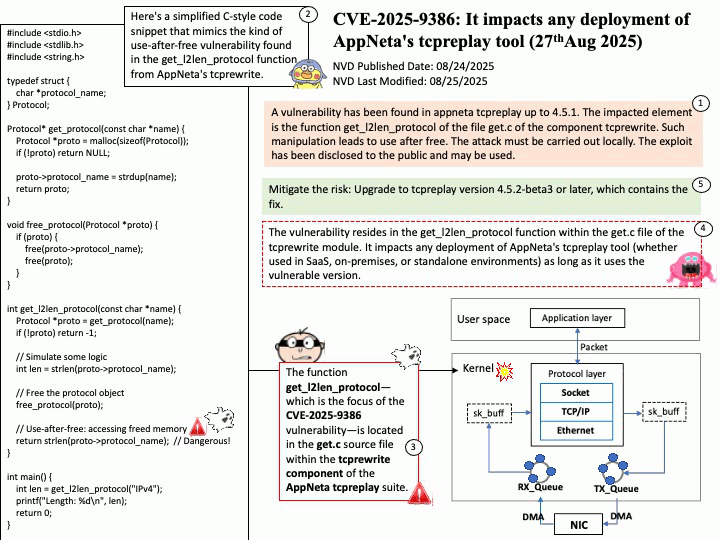
Vulnerability details:
Title – Improper Validation of Array Index in Multi-Mode Call Processor
Description – Memory corruption while selecting the PLMN from SOR failed list.
Vulnerability Type – CWE-129 Improper Validation of Array Index
Official announcement: Please refer to the link for details –
https://docs.qualcomm.com/product/publicresources/securitybulletin/september-2025-bulletin.html
Best Practices
- Always validate array indices before access.
- Use safer memory functions or wrappers that include bounds checking.
- Monitor heap usage and implement memory pressure handling routines.