Preface
In cyber security world, we are in frequent heard a term privileges escalation. IT guy familiar buffer overflow causes privileges escalation vulnerability of Windows 2000 operating system. Seems buffer overflow issue not only happened in Microsoft product, even through you are using Linux. It will happen. As of today, Apple iPhone and Google Android phone are possible encountered this technical issue. But what’s the major element trigger this cause. It includes software application , operating system driver, Libraries and programming language!
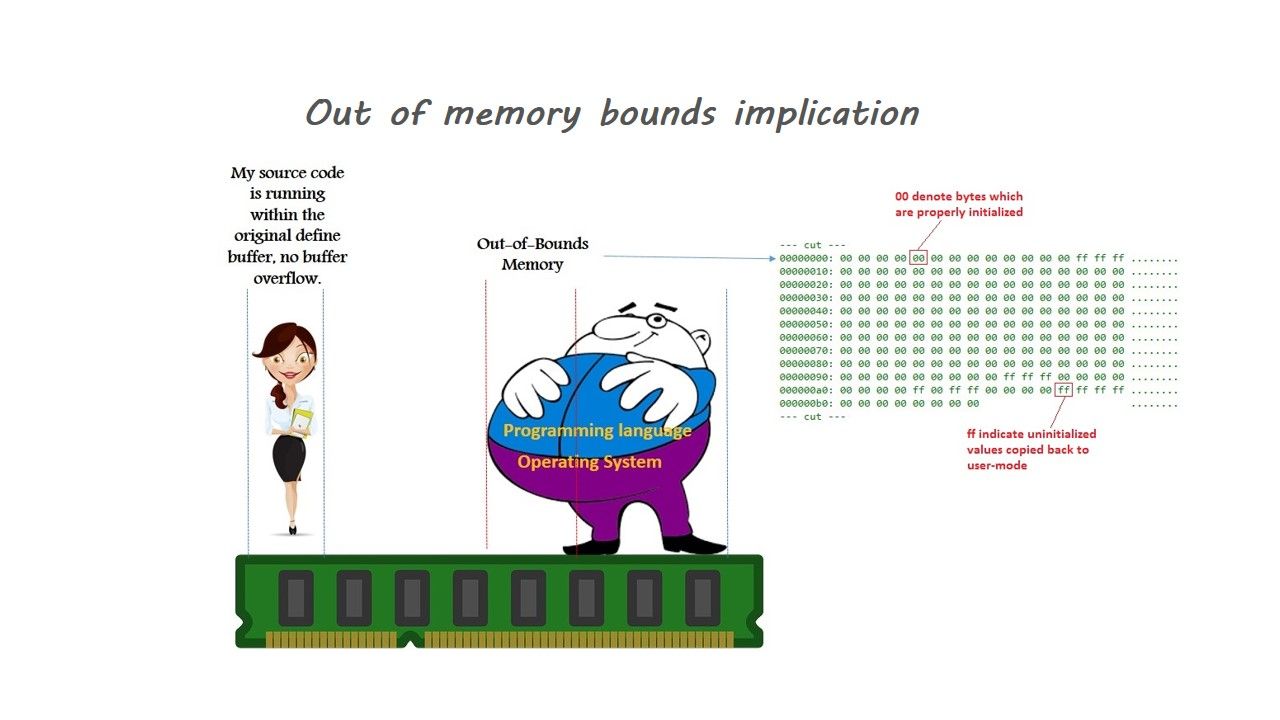
Out of memory bounds status similar a ninja, he can bypass ASLR protection
Above design limitation is an example to show the out of memory bounds concern in computer world. Yes, this issue cover all the computer world and not only limited on Microsoft products. But what is the design difficulties of system designer (OS kernel or software driver)? Basically, the system designer has flexibility to use the memory address in their design. The overall status was changed because of malware born in the computer world. Regarding to my study in Microsoft Technet blog discussion so far. It was a tremendous hard job.
We might feel that Windows 2012R2 design looks perfect since it is a mature product since it summarizes the technical weakness and design limitation experiences in former products (Windows 2008, Windows 2000 and NT). But a technical issue found in 2015 bring me to attention of this matter. The issue was that system owner only delete network interfaces on a server that is running Windows Server 2012 R2 or Windows Server 2012, a random and intermittent crashes on the system
- 0xD1: DRIVER_IRQL_NOT_LESS_OR_EQUAL
- 0X139: KERNEL_SECURITY_CHECK_FAILURE
- 0x3B: SYSTEM_SERVICE_EXCEPTION
Symptom occurs on system platform: Windows Server 2012 R2 or Windows Server 2012. Some cluster nodes that are running Windows Server 2012 R2 or Windows Server 2012 go down because of the corruption in NDIS and netcfg.
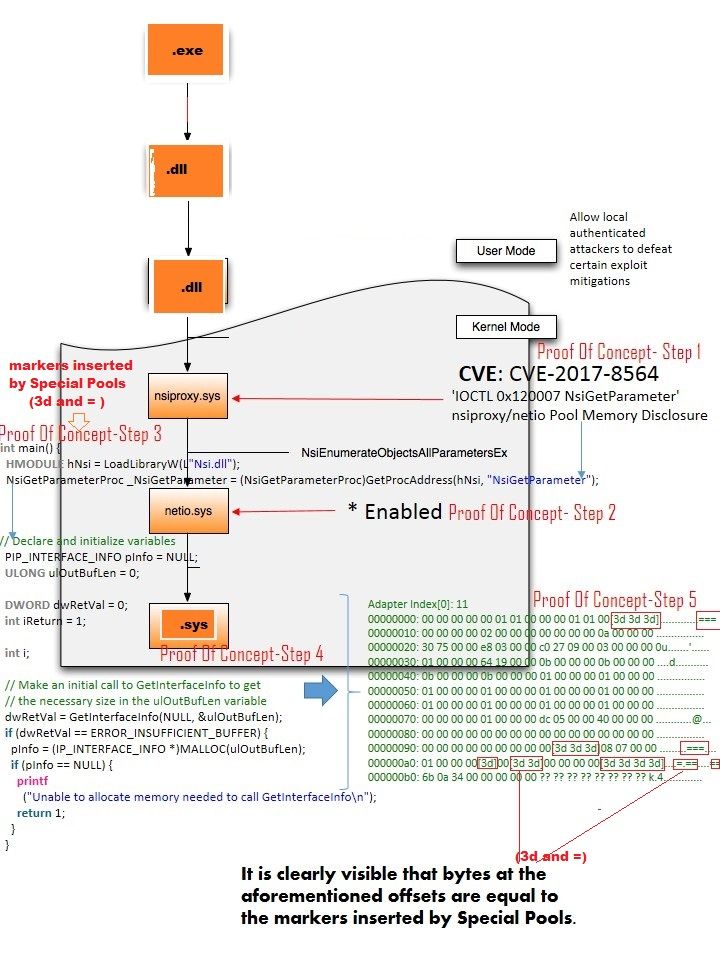
This case reveal to the computer world that memory under the memory protection features (Address space layout randomization protection (ASLR) and Data Execution Prevention (DEP) ). Kernel and driver designers are also headache in this matter. The key word “Prefect” does not appear in realistic world. Those memory protection facilities not prefect. Should you have interested of this item. Please refer below url for reference.
Hints: Cyber security experts aware that memory reuse and privileges escalation. The above our of memory bounds informative diagram specially show an idea how does hacker execute the malicious code of program in user mode instead of kernel mode.
I am a Microsoft OS. Just wonder why I was hacked even though I have protective system?
My bias pin point to Microsoft product, let’s jump to Linux world.
The BYOD and IoT devices empower Linux operating system digital world achievement. It looks that a lot of people similar to my opinion! They will accept the excuse to this baby (Linux). As far as we know, the best partner of Linux is the C or C++ programming language. There are two ways of memory accessible to the programmer.
a. User’s virtual memory space in which application to run.
b. Register memory
From technical point of view, similar embarrass situation (memory corruption) has been occurred in Linux operating system.
- Buffer overflow – Overwrite beyond allocated length
- Index of array out of bounds: (array index overflow – index too large/underflow – negative index)
- Using an address before memory is allocated and set. In this scenario the memory location is NULL or random. It is a run time error occurs when you try to point illegal memory space, usually address 0 which is reserved for OS.
- Pointer persistence – Function returning a pointer from the stack which can get overwritten by the calling function (in this case main()):
In fact that the smartphone operating system especially Android, the cyber attack hit rate are equivalent to common office automation software application. For more details, please see below diagram for reference.
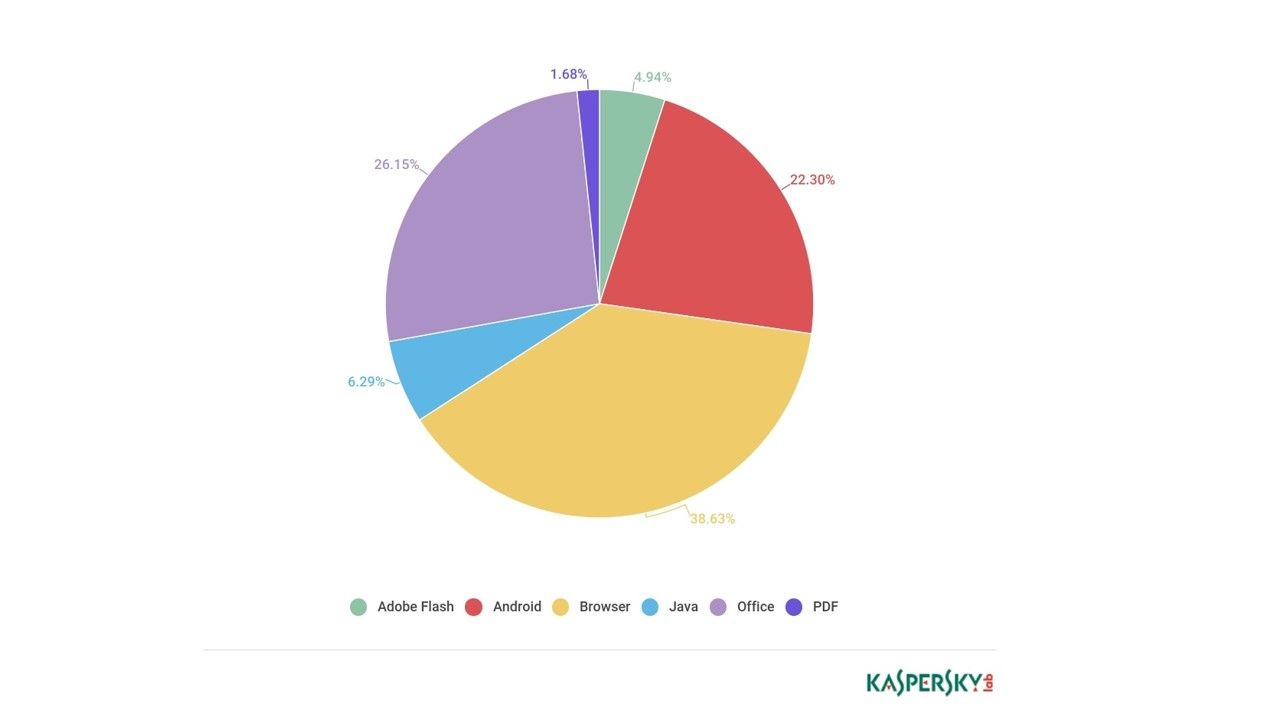
To conduct a review of the cyber attack.The cyber attack target memory address is not a new findings in mobile phone world. For instance, Huawei mobile phone encountered Out-of-Bounds Memory Access Vulnerability in the Boot Loaders on April 2017 (CVE-2017-8149). Regarding to CVE record details, this vulnerability affects an unknown function of the component Boot Loader. The manipulation as part of a Parameter leads to a memory corruption vulnerability (Out-of-Bounds). The vendor comment is that if vulnerability successful exploit. The impact could cause out-of-bounds memory read, leading to continuous system reboot.
My comment in regards to this technical issue (out of memory bounds)
The impact affects by out of bonds memory all depends on where the access lands in host memory, it could lead to information disclosure. Or crash the process trigger deny of service. It could potentially be leveraged which causes execute arbitrary code with privileges escalation.
How about in programming language, will it happen in this area?
Yes, it will happen. See what’s going on in programming language now! PHP is a server-side scripting language designed primarily for web development but also used as a general-purpose programming language. But there is no excuse given to PHP language. Details shown as below:
Out-of-bounds memory read via gdImageRotateInterpolated (CVE-2016-1903)
Details: The gdImageRotateInterpolated function in ext/gd/libgd/gd_interpolation.c in PHP before 5.5.31, 5.6.x before 5.6.17, and 7.x before 7.0.2 allows remote attackers to obtain sensitive information or cause a denial of service (out-of-bounds read and application crash) via a large bgd_color argument to the imagerotate function.A buffer over-read flaw was found in the GD library used by the PHP gd extension. A specially crafted image file could cause a PHP application using the imagerotate() function to disclose portions of the server memory or crash the PHP application.
Conclusion:
Memory out of bounds looks will be happen in digital world. Sounds like a tumor in animals and human body. The impact affects by out of bonds memory all depends on where the access lands in host memory, it could lead to information disclosure. Or crash the process trigger deny of service. It could potentially be leveraged which causes execute arbitrary code with privileges escalation.
Life is not easy especially IT world. But sometimes it have fun! Wishes Merry X’mas and Happy New year.