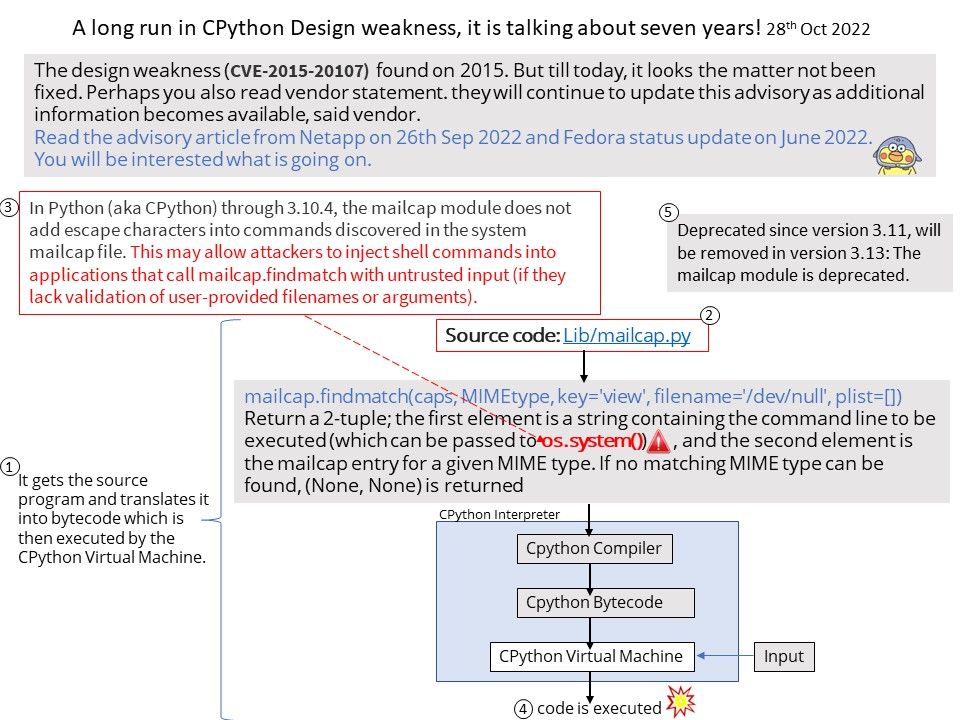
Preface: The design weakness found on 2015. But till today, it looks the matter not been fixed. Perhaps you also read vendor statement. they will continue to update this advisory as additional information becomes available, said vendor.
NetApp Advisory ID: NTAP-20220616-0001 Version: 4.0 Last updated: 09/26/2022 – https://security.netapp.com/advisory/ntap-20220616-0001/
[SECURITY] Fedora 36 Update: 18 June 2022 – https://lists.fedoraproject.org/archives/list/package-announce@lists.fedoraproject.org/message/46KWPTI72SSEOF53DOYQBQOCN4QQB2GE/
Background: When you run python at the console or install a Python distribution from python.org, you are running CPython. CPython is one of the many Python runtimes, maintained and written by different teams of developers. The unique thing about CPython is that it contains both a runtime and the shared language specification that all Python runtimes use.
The mailcap format is documented in RFC 1524, “A User Agent Configuration Mechanism For Multimedia Mail Format Information”, but is not an internet standard. However, mailcap files are supported on most Unix systems. According to Python (CPython) techincal document. Mailcap files are used to configure how MIME-aware applications such as mail readers and Web browsers react to files with different MIME types. (The name mailcap'' is derived from the phrasemail capability”.) For example, a mailcap file might contain a line like “video/mpeg; xmpeg %s”. Then, if the user encounters an email message or Web document with the MIME type video/mpeg, “%s” will be replaced by a filename (usually one belonging to a temporary file) and the xmpeg program can be automatically started to view the file.
CPython is the standard Python software implementation or the default Python interpreter. The main purpose of CPython is to execute the programming language Python. CPython has great compatibility with various Python packages and modules.
Vulnerability details: Mailcap file handling in Python through 3.10.4
In Python (aka CPython) through 3.10.4, the mailcap module does not add escape characters into commands discovered in the system mailcap file. This may allow attackers to inject shell commands into applications that call mailcap.findmatch with untrusted input (if they lack validation of user-provided filenames or arguments).
if the filename contains Shell Commands they will be executed if they
are passed to os.system() as discribed in the docs.
Remedy: Filename should be quoted with quote(filename) to fix the bug. Please refer to the link for details – https://bugs.python.org/issue24778
Status: Deprecated since version 3.11, will be removed in version 3.13: The mailcap module is deprecated