Preface: Xen Project is a hypervisor using a microkernel design, providing services that allow multiple computer operating systems to execute on the same computer hardware concurrently.
Vulnerability description:
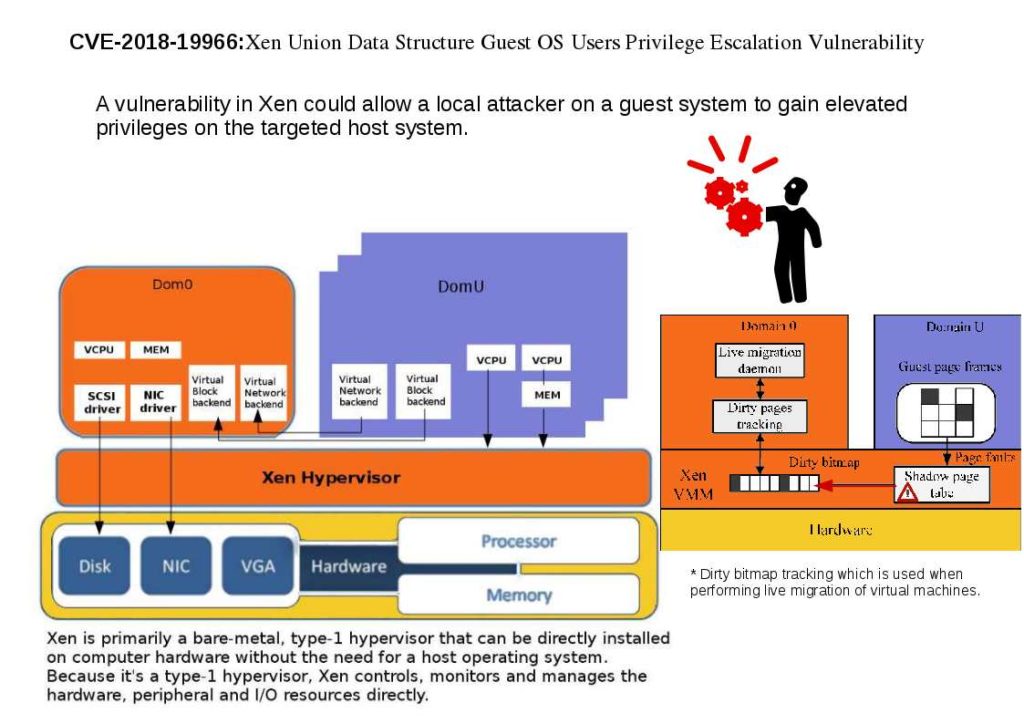
The vulnerability is due to an interpretation conflict for union data structure associated with shadow paging.The XSA-240 introduced a new field into the control structure
associated with each page of RAM. This field was added to a union data structure.Thus dirty bitmap tracking which is used when performing live migration of virtual machines. However a technical conflicts during migration, or L1TF mitigation for PV guests(L1 Terminal Fault speculative side channel mitigation – XSA-273).
Impact: All Xen versions from at least 3.2 onwards are vulnerable. Earlier versions have not been checked
Official remedy solution: https://xenbits.xen.org/xsa/advisory-280.html