Preface: AMD’s Versal Adaptive SoCs are designed for high-performance computing, offering a blend of programmable logic, processing system, and AI engines, along with advanced memory and interfaces. They excel in cloud, network, and edge applications by combining heterogeneous compute with a wide range of hard IP. This architecture enables outstanding performance/watt and adapts to changing requirements, making them suitable for various applications like AI, data centers, and network acceleration.
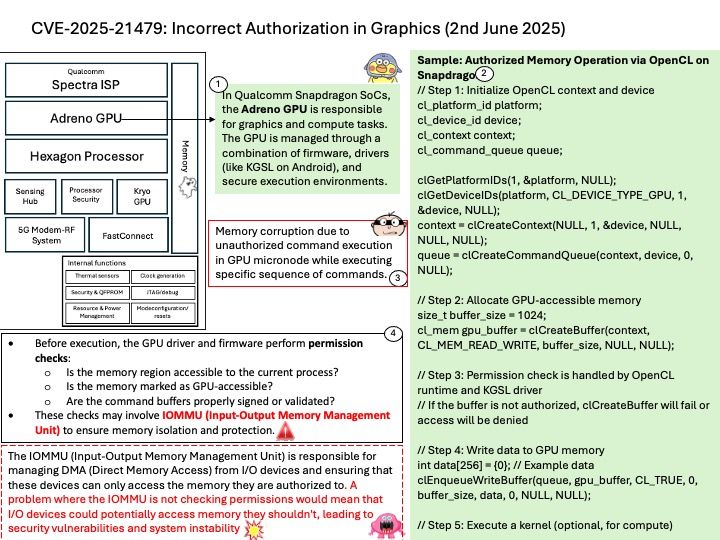
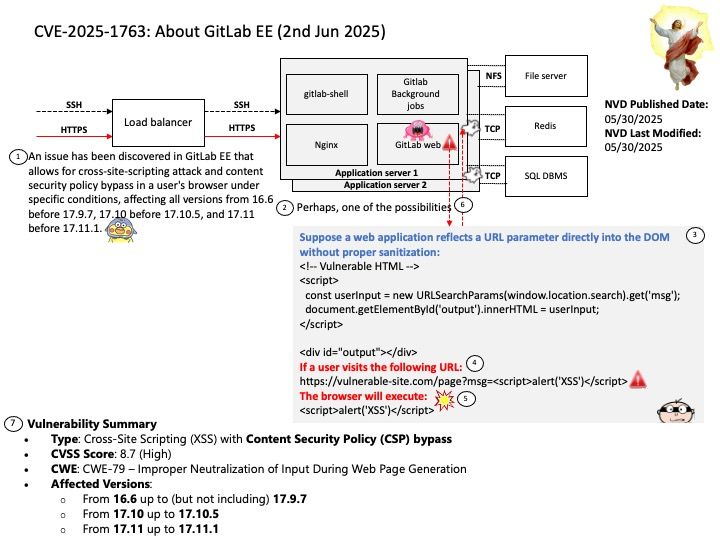
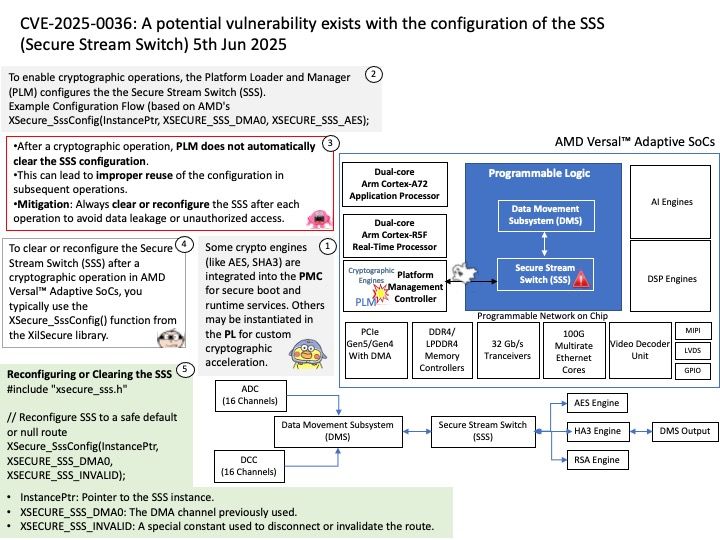
Background: In Versal™ Adaptive SoC devices, the Platform Loader and Manager (PLM) implements runtime (post-boot) software services that allows a remote processor to command the PLM to execute cryptographic operations – including AES, SHA3, RSA, ECDSA – on behalf of the remote processor. These operations require the Secure Stream Switch (SSS) to be configured such that the Direct Memory Access (DMA) hardware can send data to and read from these cryptographic engines.
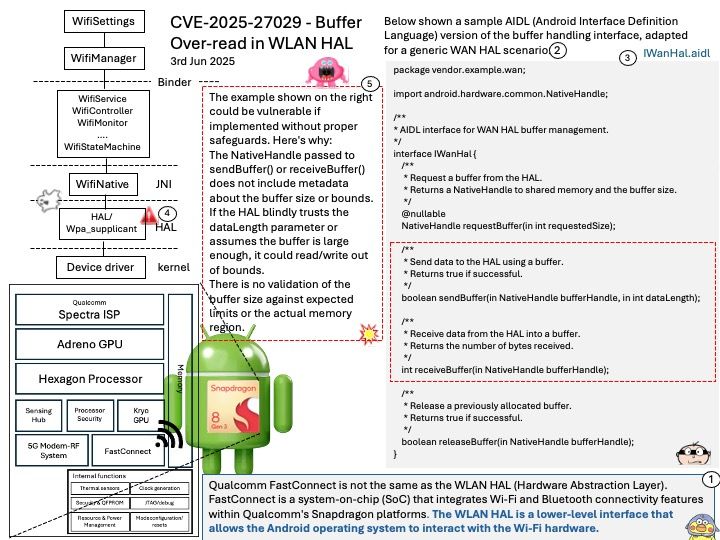
Ref: Some crypto engines (like AES, SHA3) are integrated into the PMC for secure boot and runtime services. Others may be instantiated in the PL for custom cryptographic acceleration.
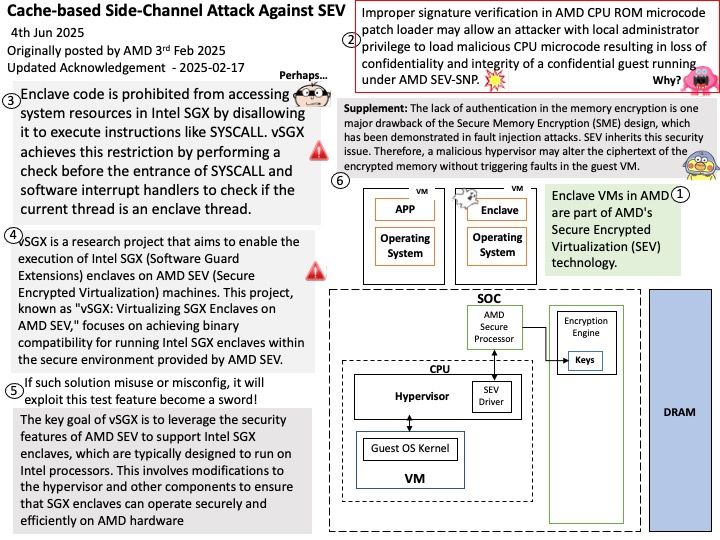
Vulnerability details: A potential vulnerability exists with the configuration of the SSS because the PLM does not clear the SSS configuration after a cryptographic operation completes. This allows an improper SSS configuration when setting up the SSS for any following cryptographic command.
Official announcement: For more details, please refer to the following link – https://www.amd.com/en/resources/product-security/bulletin/amd-sb-8011.html