Preface: Next.js is a powerful React framework that simplifies web development by providing features like server-side rendering (SSR), static site generation (SSG), and API routes, all while offering built-in optimizations and a great developer experience. It’s essentially a framework built on top of React, adding extra functionality to create high-performance, SEO-friendly web applications.
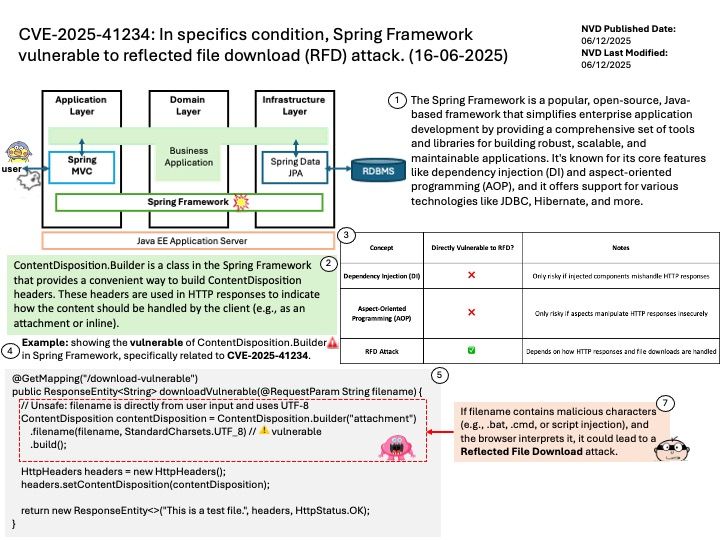
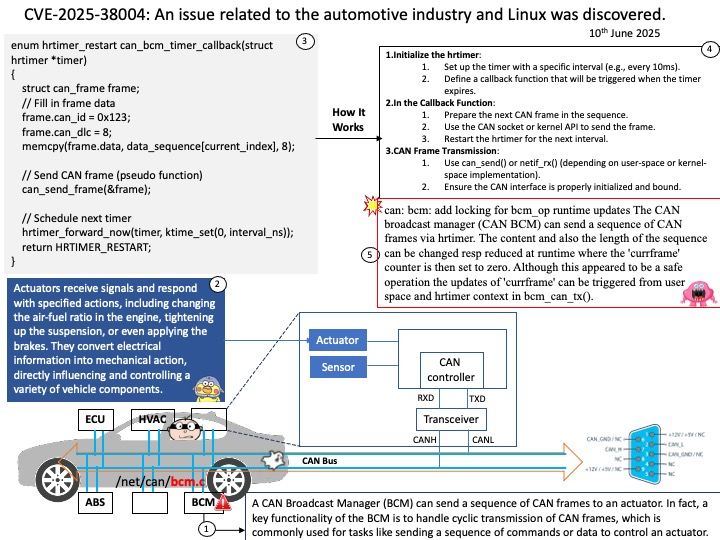
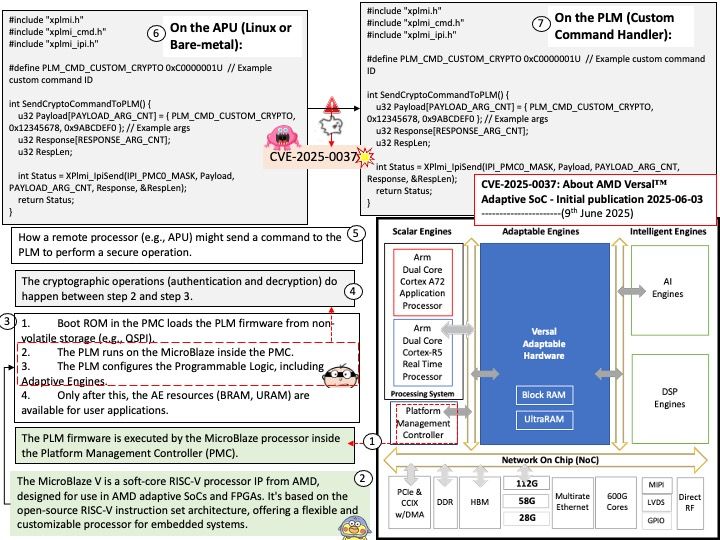
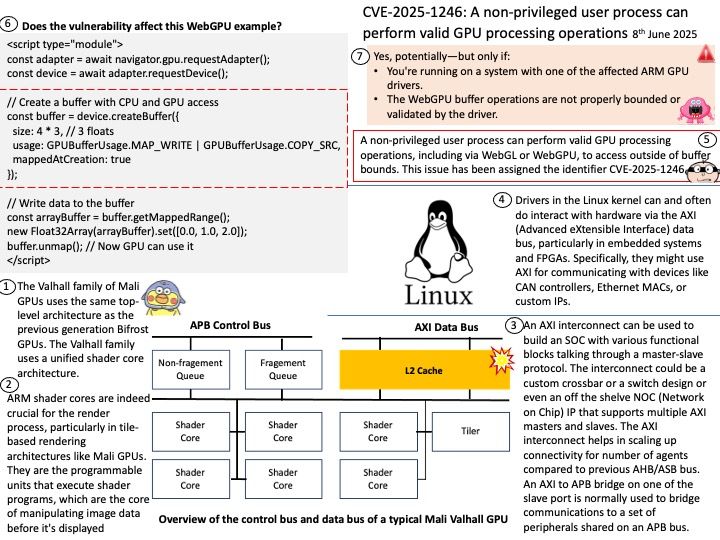
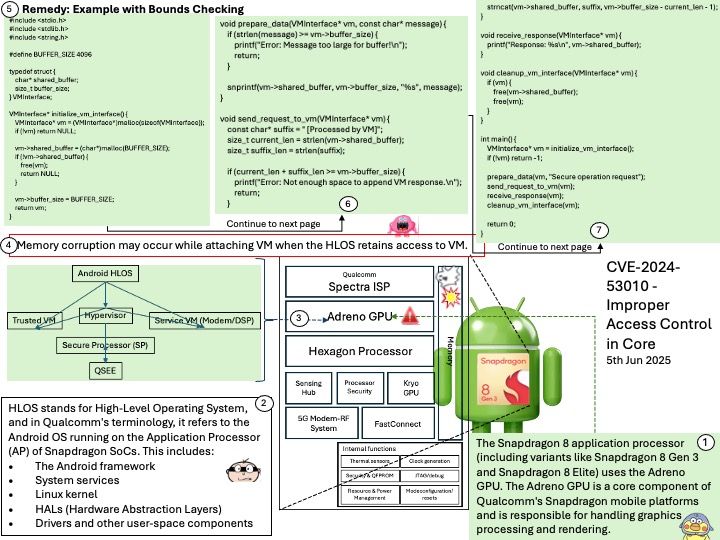
Background: The @opennextjs/cloudflare package is a Cloudflare-specific adapter that allows you to deploy Next.js applications to Cloudflare’s developer platform. It essentially transforms a Next.js application, built using next build in standalone mode, to run within the Cloudflare’s workerd runtime using the Workers Node.js compatibility layer. This enables features like server-side rendering (SSR) and serving static assets directly from Cloudflare’s edge network.
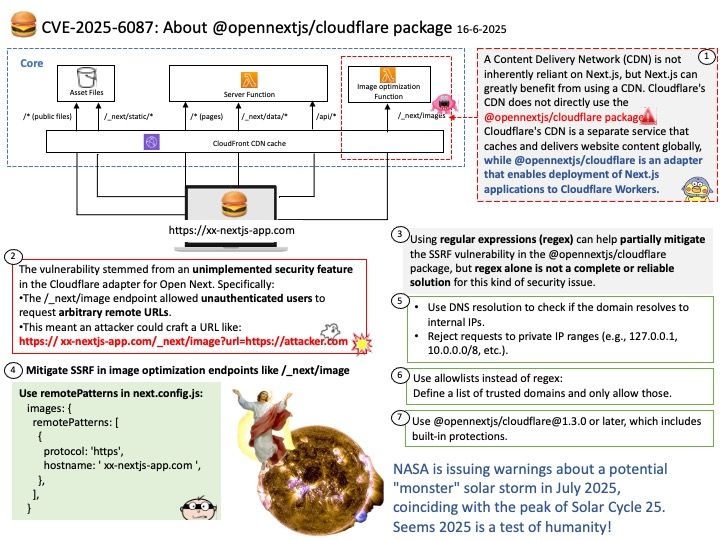
Vulnerability details: A Server-Side Request Forgery (SSRF) vulnerability was identified in the @opennextjs/cloudflare package. The vulnerability stems from an unimplemented feature in the Cloudflare adapter for Open Next, which allowed unauthenticated users to proxy arbitrary remote content via the /_next/image endpoint. This issue allowed attackers to load remote resources from arbitrary hosts under the victim site’s domain for any site deployed using the Cloudflare adapter for Open Next.
Impact:
* SSRF via unrestricted remote URL loading
* Arbitrary remote content loading
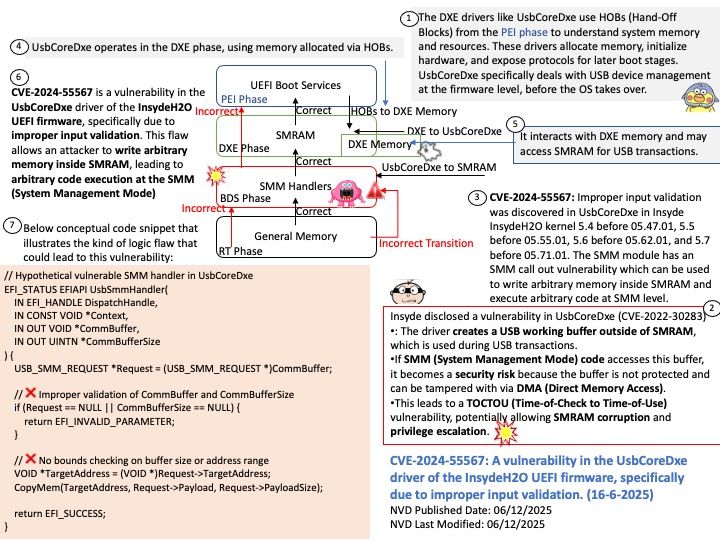
* Potential internal service exposure or phishing risks through domain abuse
Mitigation: The following mitigations have been put in place:
* Server side updates to Cloudflare’s platform to restrict the content loaded via the /_next/image endpoint to images.
The update automatically mitigates the issue for all existing and any future sites deployed to Cloudflare using the affected version of the Cloudflare adapter for Open Next
* Root cause fix https://github.com/opennextjs/opennextjs-cloudflare/pull/727 to the Cloudflare adapter for Open Next.
Official announcement: Please see the link for details – https://nvd.nist.gov/vuln/detail/CVE-2025-6087