Preface: Does Big Data use the TLB in the Linux kernel?
Yes, big data applications in Linux utilize the Translation Lookaside Buffer (TLB) as a crucial component of memory management. The TLB speeds up address translation by caching recently used virtual-to-physical address mappings. Applications like databases, which often handle large datasets and have specific memory access patterns, can benefit from the TLB’s ability to reduce the overhead of accessing physical memory.
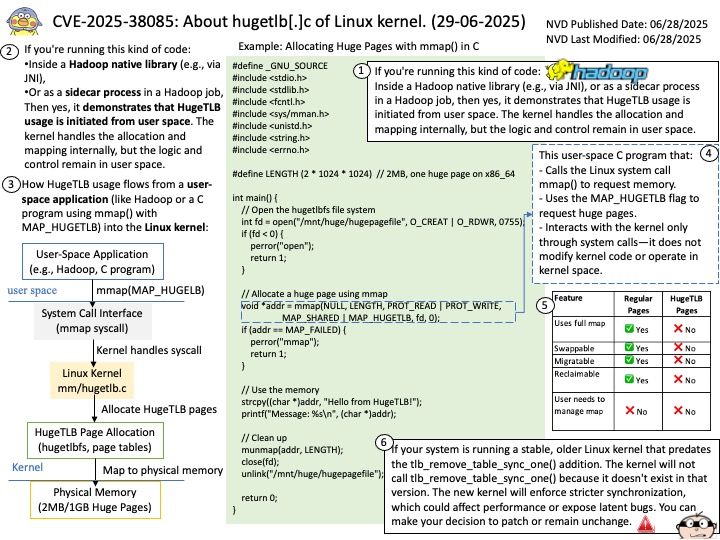
Background: The Linux kernel’s mm/hugetlb directory contains the code for Huge TLB (Translation Lookaside Buffer) support. This feature allows the kernel to use larger page sizes (like 2MB or 1GB instead of the usual 4KB) for memory management, potentially improving performance by reducing TLB misses.
Ref: syscalls are part of the operating system kernel and provide an interface for user space programs to request services from the kernel. User space refers to the memory area where applications run, while kernel space is where the operating system’s core and privileged operations reside.
Vulnerability details: In the Linux kernel, the following vulnerability has been resolved: mm/hugetlb: fix huge_pmd_unshare() vs GUP-fast race huge_pmd_unshare() drops a reference on a page table that may have previously been shared across processes, potentially turning it into a normal page table used in another process in which unrelated VMAs can afterwards be installed. If this happens in the middle of a concurrent gup_fast(), gup_fast() could end up walking the page tables of another process. While I don’t see any way in which that immediately leads to kernel memory corruption, it is really weird and unexpected. Fix it with an explicit broadcast IPI through tlb_remove_table_sync_one(), just like we do in khugepaged when removing page tables for a THP collapse.
Official announcement: Please see the link for details https://nvd.nist.gov/vuln/detail/CVE-2025-38085
My comment: If your system is running a stable, older Linux kernel that predates the tlb_remove_table_sync_one() addition. The kernel will not call tlb_remove_table_sync_one() because it doesn’t exist in that version. The new kernel will enforce stricter synchronization, which could affect performance or expose latent bugs. You can make your decision to patch or remain unchanged.