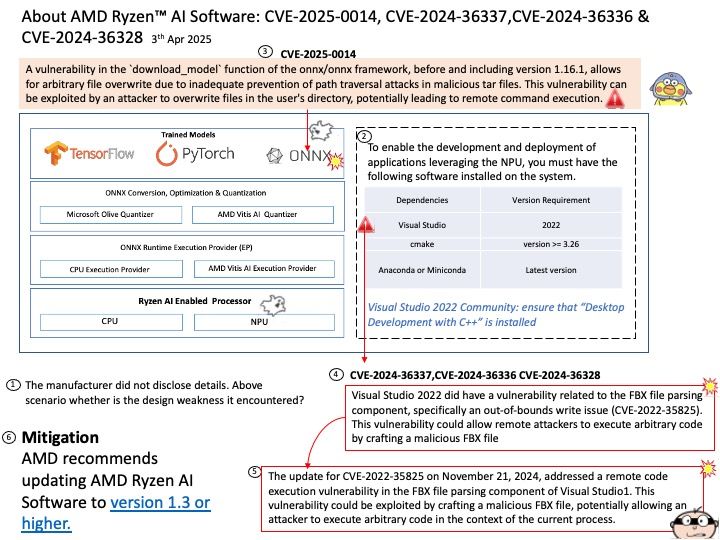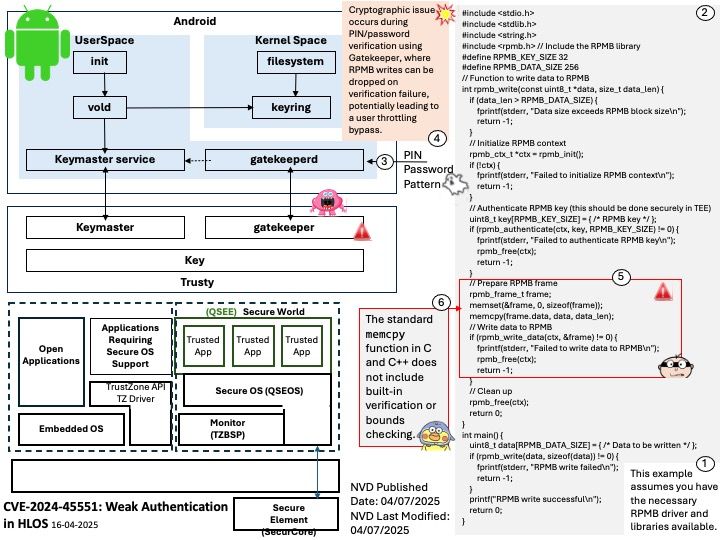
NVD Published Date: 04/07/2025
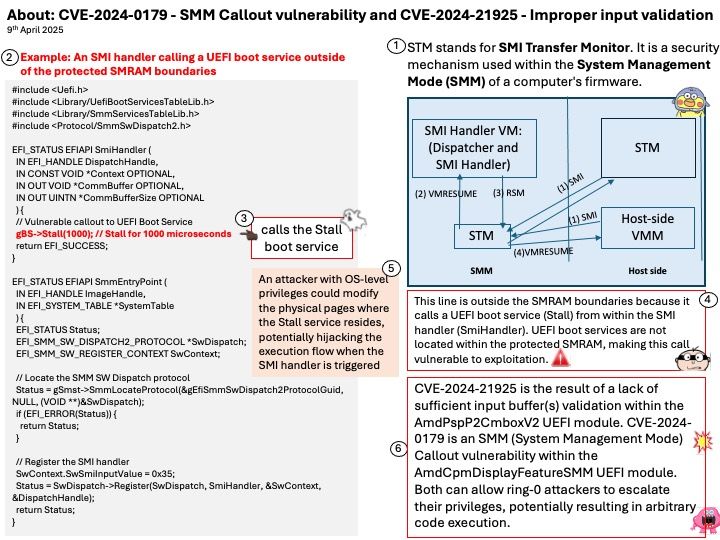
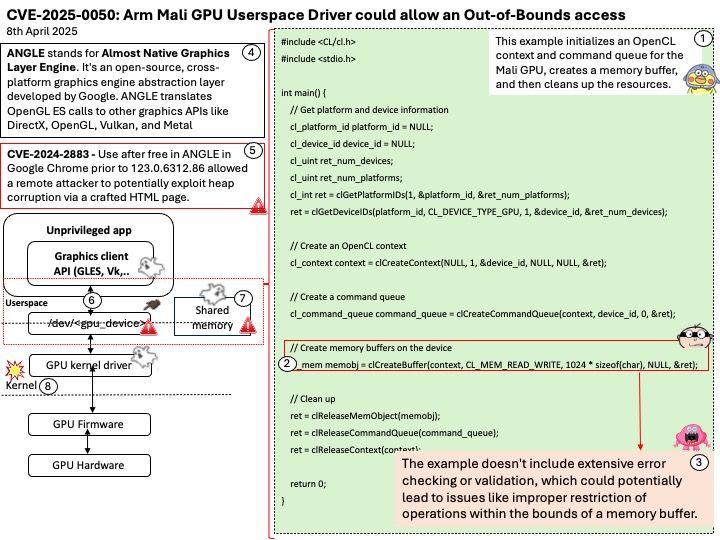
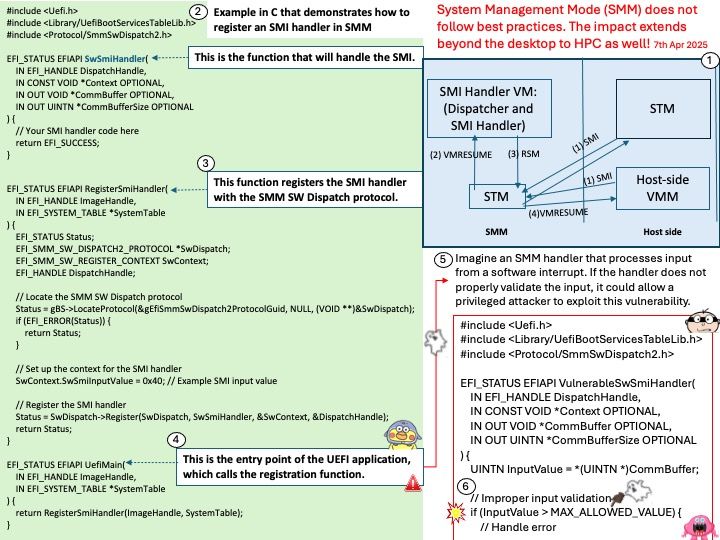
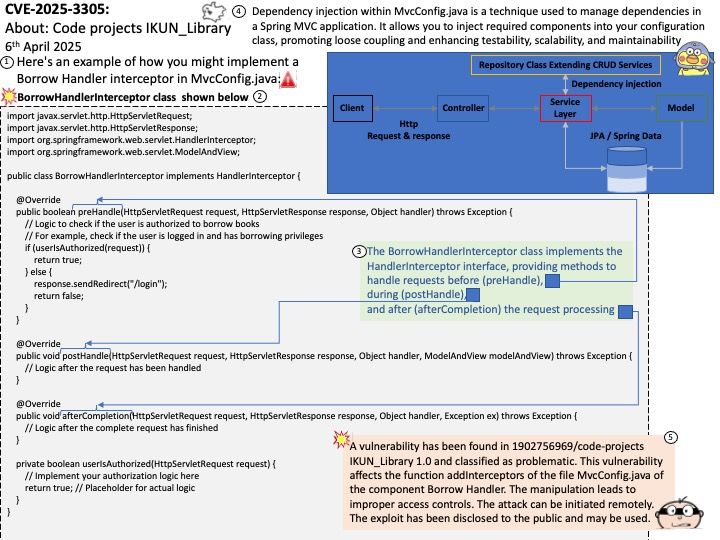
NVD Last Modified: 04/07/2025
Preface: Released on September 3, 2024 as Android 15. Android 16, Internal codename as Baklava, released on 2nd April 2025.
Background: The core of the Android OS operating system is the Android Open Source Project (AOSP), which is free open source software (FOSS) licensed primarily under the Apache License. However, most devices run a proprietary version of Android developed by Google, which comes pre-installed with additional proprietary, closed-source software, most popular Google Mobile Services (GMS), which includes core applications such as Google Chrome, the digital distribution platform Google Play, and the related Google Play Services development platform.
Qualcomm Android source code is divided into development source code and proprietary source code. Proprietary source code is further divided into proprietary non-HLOS software and proprietary HLOS software. HLOS is the High-level Operating System, and non-HLOS software refers to software below the HLOS layer.
Vulnerability details: Cryptographic issue occurs during PIN/password verification using Gatekeeper, where RPMB writes can be dropped on verification failure, potentially leading to a user throttling bypass.
Official announcement: Please see the link for details –