Preface: The DMTF’s Security Protocols and Data Models (SPDM) Working group is responsible for the SPDM standard. This standard enables authentication, attestation and key exchange to assist in providing infrastructure security enablement.
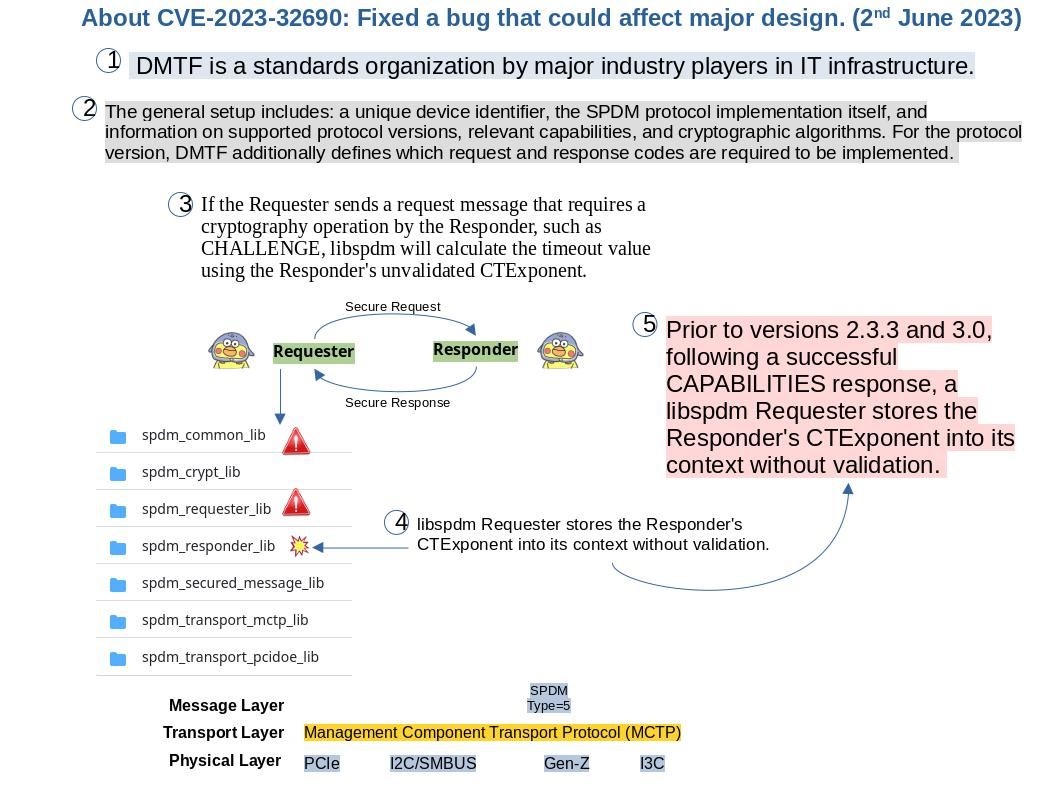
Background: Security Protocol and Data Model (SPDM) is a two-party protocol between a Requester that initiates the conversation and the Responder. DMTF is a standards organization by major industry players in IT infrastructure.
Vulnerability details: libspdm is a sample implementation that follows the DMTF SPDM specifications. Prior to versions 2.3.3 and 3.0, following a successful CAPABILITIES response, a libspdm Requester stores the Responder’s CTExponent into its context without validation. If the Requester sends a request message that requires a cryptography operation by the Responder, such as CHALLENGE, libspdm will calculate the timeout value using the Responder’s unvalidated CTExponent. A patch is available in version 2.3.3. A workaround is also available. After completion of VCA, the Requester can check the value of the Responder’s CTExponent. If it greater than or equal to 64, then the Requester can stop communication with the Responder.
Official announcement: For details, please refer to the link – https://www.cve.org/CVERecord?id=CVE-2023-32690