The vulnerabilities occurred so far, it awaken the SDLC (software development life cycle) process. The design bug common appear in development cycle. The bug checker may record in details and put in the report let the decision maker know the actual statis. Project management office member better to use your knowledge learned during PMP or Prince 2 lesson. Don’t let your certificate become a paper!
Default user username cannot be changed looks not strange to IT guy!
Release 1.1.0 – The default username is maglev and cannot be changed.
Release 1.0 – The default username is grapevine and cannot be changed.
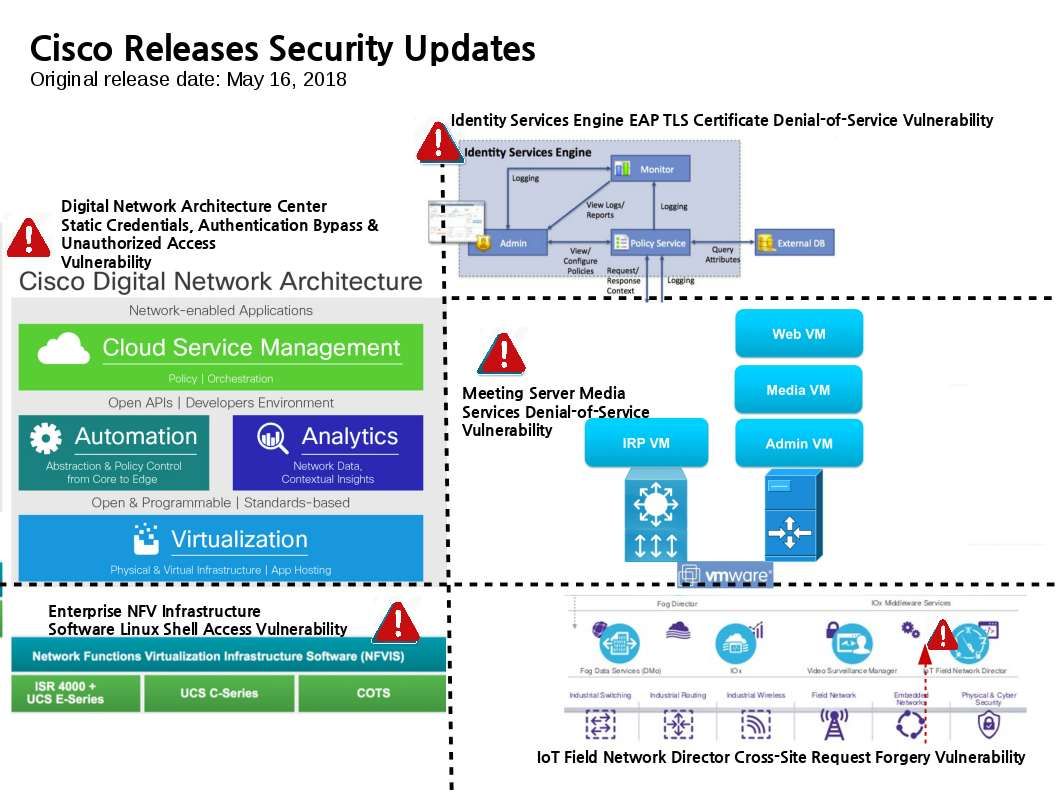
Cisco Digital Network Architecture Center Static Credentials Vulnerability
https://tools.cisco.com/security/center/content/CiscoSecurityAdvisory/cisco-sa-20180516-dnac