Preface: Two of the most often used protocols in SCADA networks are Modbus and IEC 60870 – 5. A communication protocol is a collection of rules that enable two or more networked entities to interact with each other. Both the transmitter and the recipient of the information must agree on the protocol.
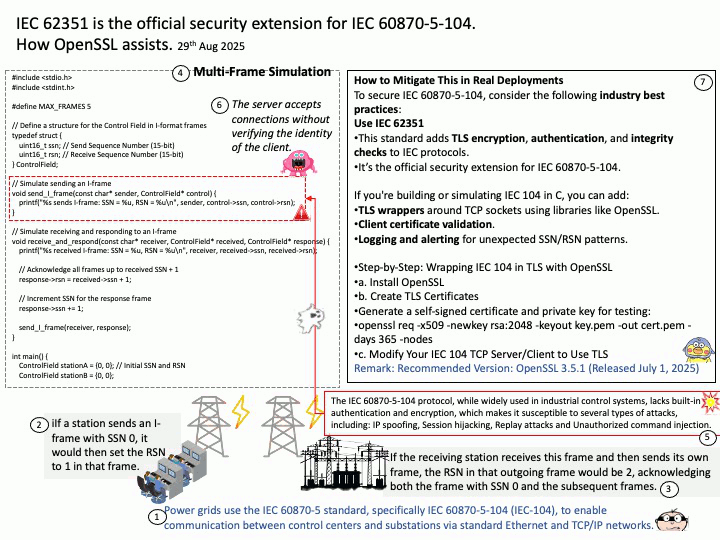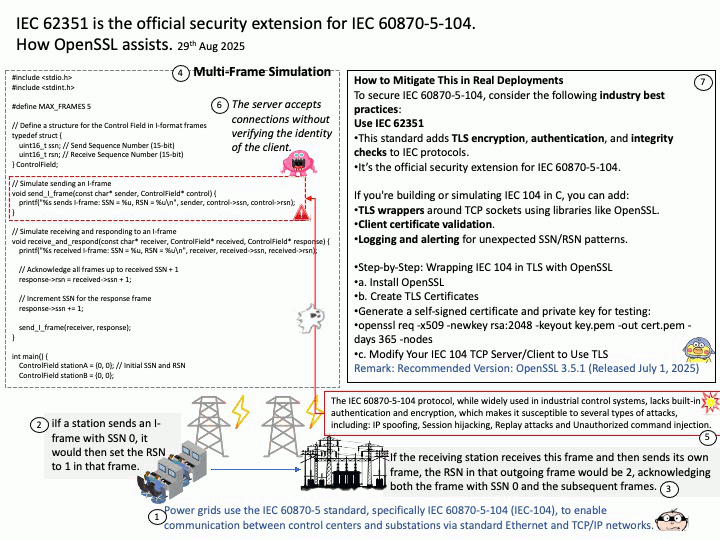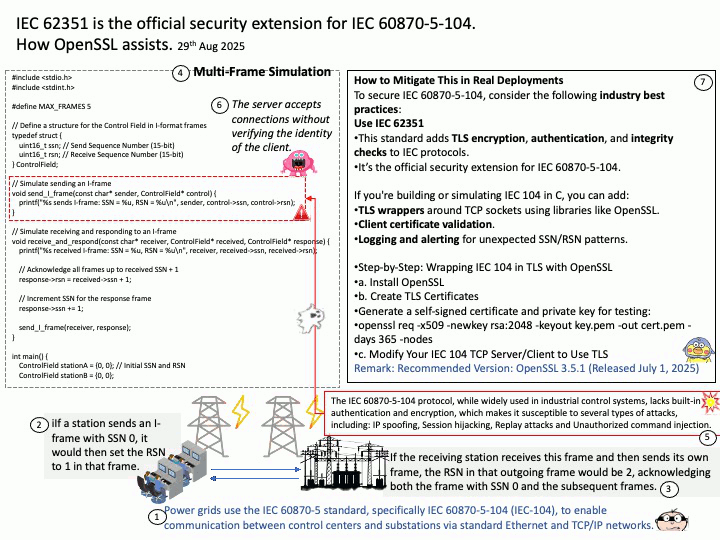
Background: In IEC 60870-5-104 (IEC-104) specifications, the Protocol Control Information (PCI) sequence number is a 15-bit value found in the Control field of frames to manage ordered information transfer. There are two types of sequence numbers: the Send Sequence Number (SSN), which the sending station increments for each I-frame sent, and the Receive Sequence Number (RSN), which acknowledges the last SSN received. The RSN effectively acknowledges all frames from the previously received SSN up to the current one
1.If a station sends an I-frame with SSN 0, it would then set the RSN to 1 in that frame.
2.If the receiving station receives this frame and then sends its own frame, the RSN in that outgoing frame would be 2, acknowledging both the frame with SSN 0 and the subsequent frames.
Cyber-security focus: The IEC 60870-5-104 protocol, while widely used in industrial control systems, lacks built-in authentication and encryption, which makes it susceptible to several types of attacks, including: IP spoofing , Session hijacking, Replay attacks and Unauthorized command injection.
How to Mitigate?
To secure IEC 60870-5-104, consider the following industry best practices:
1. Use IEC 62351 – This standard adds TLS encryption, authentication, and integrity checks to IEC protocols.
It’s the official security extension for IEC 60870-5-104.
2. Network Segmentation – Isolate control networks from corporate or public networks.
Use firewalls and VLANs to restrict access.
3. IP Whitelisting and Port Hardening – Only allow known IP addresses to connect to the IEC server.
Use non-default ports and monitor for unusual traffic.
4. Deep Packet Inspection (DPI) – Use industrial firewalls or intrusion detection systems (IDS) that understand IEC 104 traffic.
Detect anomalies in SSN/RSN behavior or unauthorized commands.
5. Secure Boot and Firmware Validation – Ensure that devices running IEC 104 are not compromised at the firmware level.
End of topic.