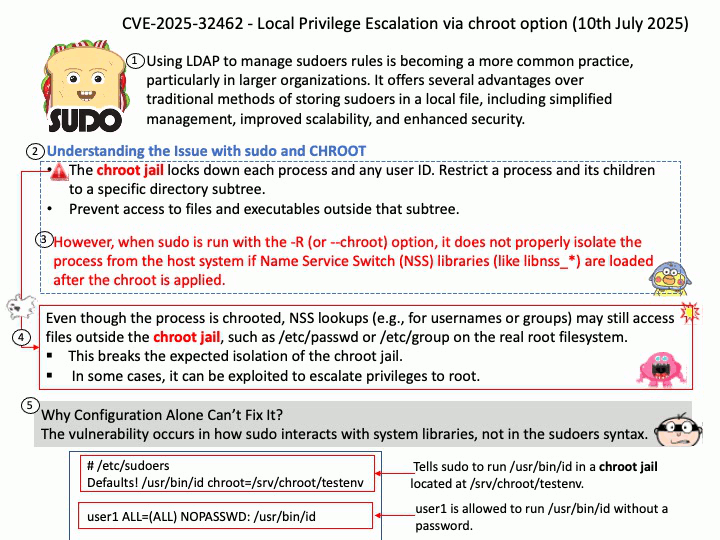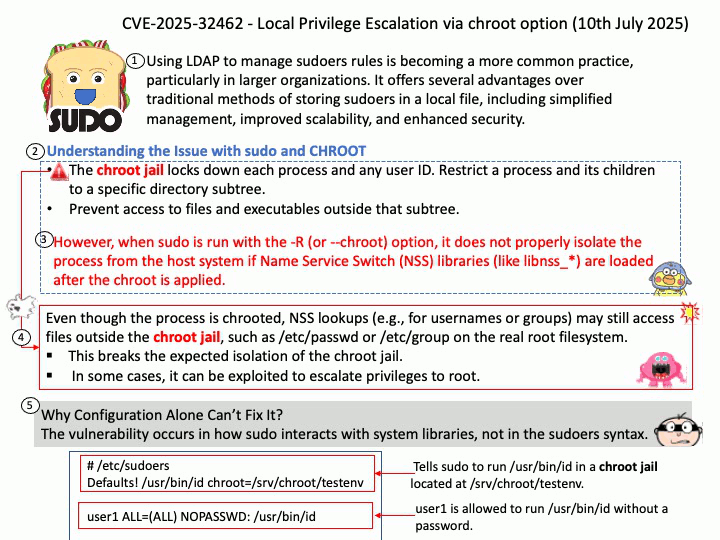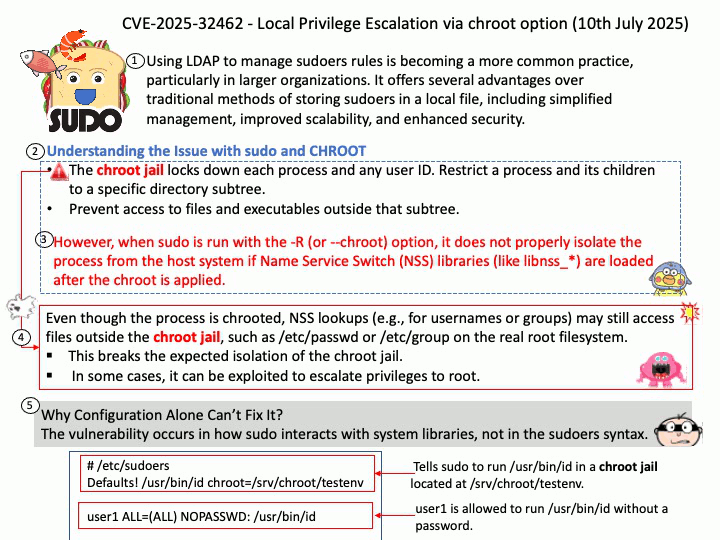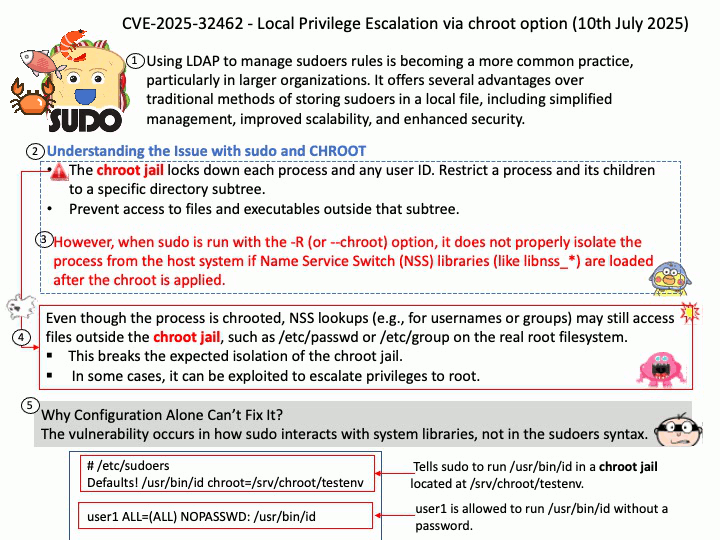
Preface: Using LDAP to manage sudoers rules is becoming a more common practice, particularly in larger organizations. It offers several advantages over traditional methods of storing sudoers in a local file, including simplified management, improved scalability, and enhanced security.
Background:
Best Practices for Using sudo.
- Avoid Logging in as Root: Use sudo instead of su to minimize security risks.
- Grant Minimal Permissions: Assign only the necessary privileges to prevent unauthorized access.
- Monitor sudo Usage: Check logs for suspicious activity
This helps to minimize security risks associated with elevated privileges.
* Specific commands: Instead of ALL=(ALL:ALL), grant access to specific commands only. For example, jane ALL=(ALL:ALL) /usr/bin/apt update, /usr/bin/apt upgrade
Vulnerability details: Sudo before 1.9.17p1, when used with a sudoers file that specifies a host that is neither the current host nor ALL, allows listed users to execute commands on unintended machines.
This vulnerability occurs when a sudoers file specifies a host that is neither the current host nor ALL. In such cases, sudo may incorrectly allow listed users to execute commands on unintended machines.
This is a configuration-based logic flaw rather than a memory corruption or privilege escalation bug. It does not involve CHROOT directly, but rather the host-specific rule matching in sudoers.
Official announcement: Please see the link for details – https://nvd.nist.gov/vuln/detail/CVE-2025-32462