Preface: The MoxaEDS–405A/408A are entry-level 5 and 8-port managed Ethernet switches designed especially for industrial applications.
Technical background: Turbo Ring is a self-healing technology that enables fast fault recovery under 20 ms. Moxa’s Turbo Ring and Turbo Chain Ethernet technologies maximize railway network availability with ideal redundancy technology.
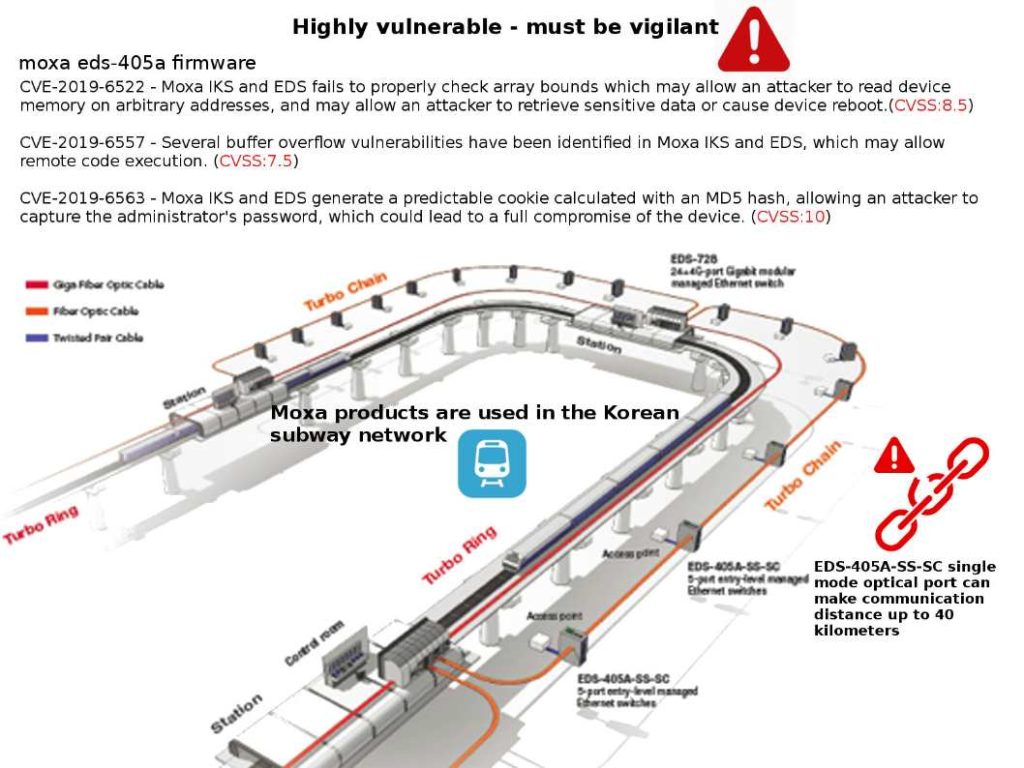
Security focus: CVE-2019-6563 (CVSS:10) – Moxa IKS and EDS generate a predictable cookie calculated with an MD5 hash, allowing an attacker to capture the administrator’s password, which could lead to a full compromise of the device.
What is Predictable cookie ? For example: Cookie: JSESSIONID=USER1. A predictable cookie calculated with an MD5 hash bring our attention because MD5 produces a 128-bit hash as an output; only 3 bytes of the hash value are used in the cookie value.
Observation: Moxa products are used in the Korean subway network on 2010. Not sure whether it is still remain usage. But believe that a remedy solution has been taken if it is still in used. Otherwise it will create a cyber security risk in the operations.
Vulnerabilities details please refer to url: https://ics-cert.us-cert.gov/advisories/ICSA-19-057-01