Preface: PcVue is a well-known and highly regarded SCADA solution, renowned for its innovation and user-friendliness, despite facing competition from larger, more dominant SCADA vendors. While not the most popular solution, PcVue’s strengths in user configuration, advanced HMI functionality, and integration capabilities have solidified its position in the market.
Background: Key Objectives of PcVue SCADA
Supervisory Control and Monitoring: To offer a centralized platform for operators to monitor and control complex industrial processes and large-scale infrastructure in real-time.
Data Acquisition and Analysis: To collect, process, and convert raw data into actionable information, providing operators with relevant alerts, reports, and historical data for informed decision-making.
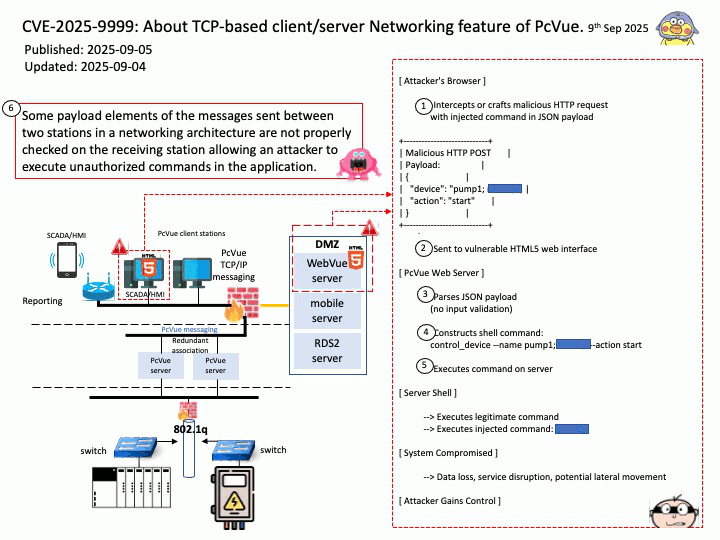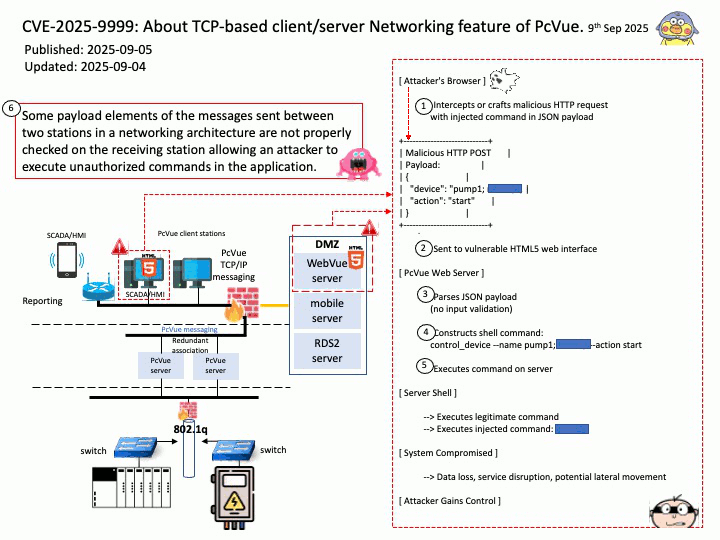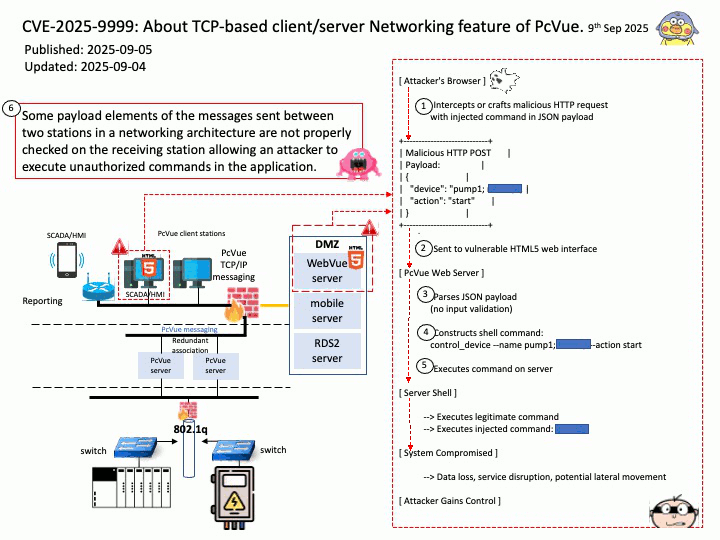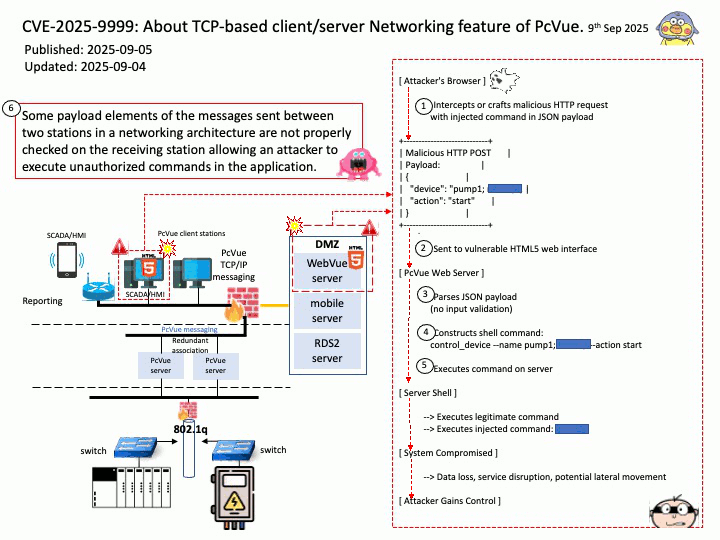
Vulnerability details: Some payload elements of the messages sent between two stations in a networking architecture are not properly checked on the receiving station allowing an attacker to execute unauthorized commands in the application.
Official announcement: Please see the link for details
https://www.pcvue.com/security/#SB2025-4
How to Prevent This:
Input Validation: Never trust client input. Use strict schemas (e.g., JSON Schema).
- Command Execution Hardening:
- Avoid os.system() or shell execution.
- Use safe APIs like subprocess.run() with argument lists.
Authentication & Authorization: Ensure only authorized users can send control commands.
Web Application Firewall (WAF): Detect and block suspicious payloads.