Preface: Does it good when artificial Intelligence use Open Source software? Yes, using open-source software is generally considered a positive aspect for artificial intelligence development. It fosters collaboration, transparency, and faster innovation, while also potentially reducing costs and biases. However, it’s crucial to acknowledge potential risks like misuse and the need for responsible development practices.
Background: The Model Context Protocol (MCP) is an open standard, open-source framework designed to standardize how AI models, particularly large language models (LLMs), interact with external tools, systems, and data sources. Think of it as a universal adapter, similar to USB-C, for AI applications, allowing them to easily connect to and utilize various data and tools.
A Kanban MCP Server is a server component that manages Kanban boards using the Model Context Protocol (MCP). It allows AI assistants and other systems to interact with and manipulate Kanban boards programmatically, enabling automation and integration of workflows.
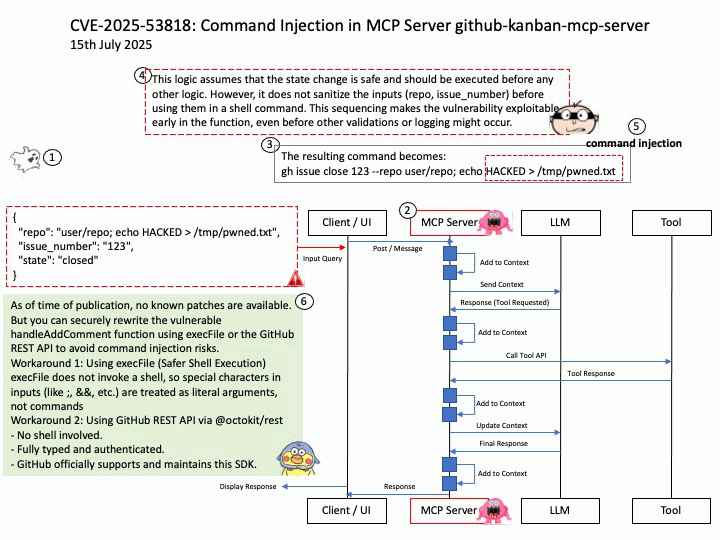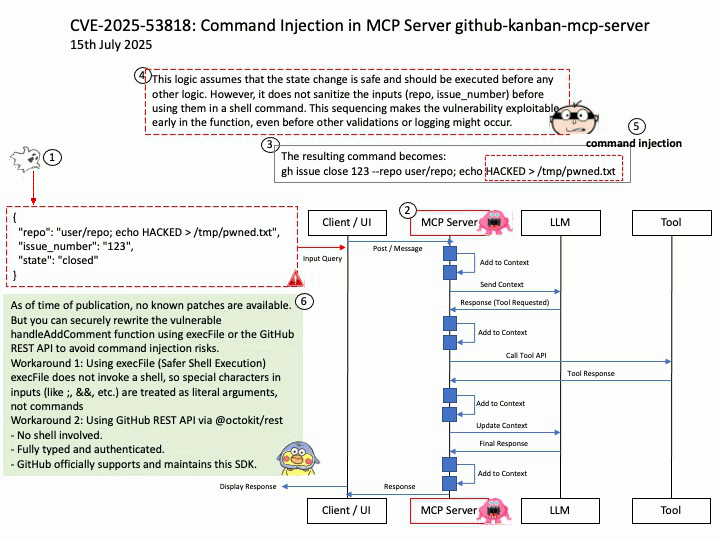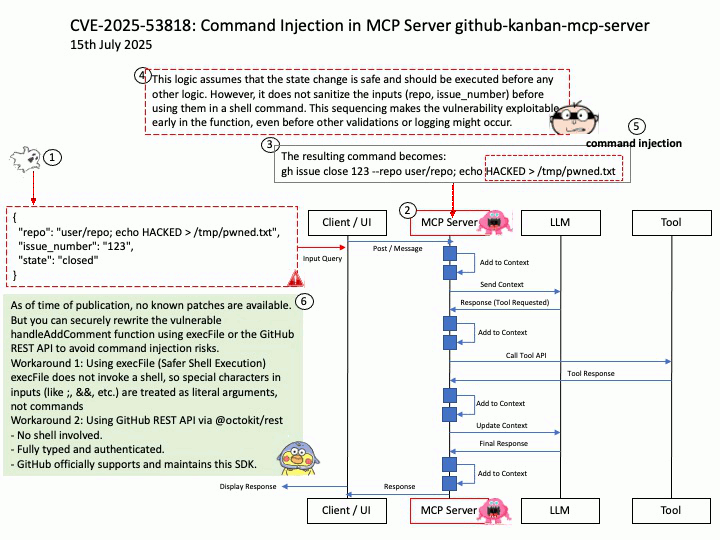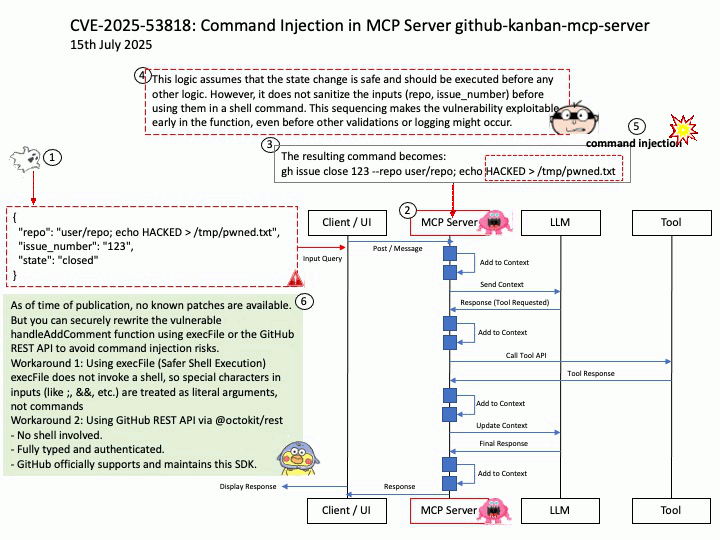
Vulnerability details: GitHub Kanban MCP Server is a Model Context Protocol (MCP) server for managing GitHub issues in Kanban board format and streamlining LLM task management. Versions 0.3.0 and 0.4.0 of the MCP Server are written in a way that is vulnerable to command injection vulnerability attacks as part of some of its MCP Server tool definition and implementation. The MCP Server exposes the tool `add_comment` which relies on Node.js child process API `exec` to execute the GitHub (`gh`) command, is an unsafe and vulnerable API if concatenated with untrusted user input.
Workaround: As of time of publication, no known patches are available.
But you can securely rewrite the vulnerable handleAddComment function using execFile or the GitHub REST API to avoid command injection risks.
Workaround 1: Using execFile (Safer Shell Execution)
execFile does not invoke a shell, so special characters in inputs (like ;, &&, etc.) are treated as literal arguments, not commands
Workaround 2: Using GitHub REST API via @octokit/rest
– No shell involved.
– Fully typed and authenticated.
– GitHub officially supports and maintains this SDK.
Official announcement: Please refer to url for details –