
IOS XE built on Linux and provides a distributed software architecture that moves many operating system responsibilities out of the IOS process and has a copy of IOS running as a separate process.
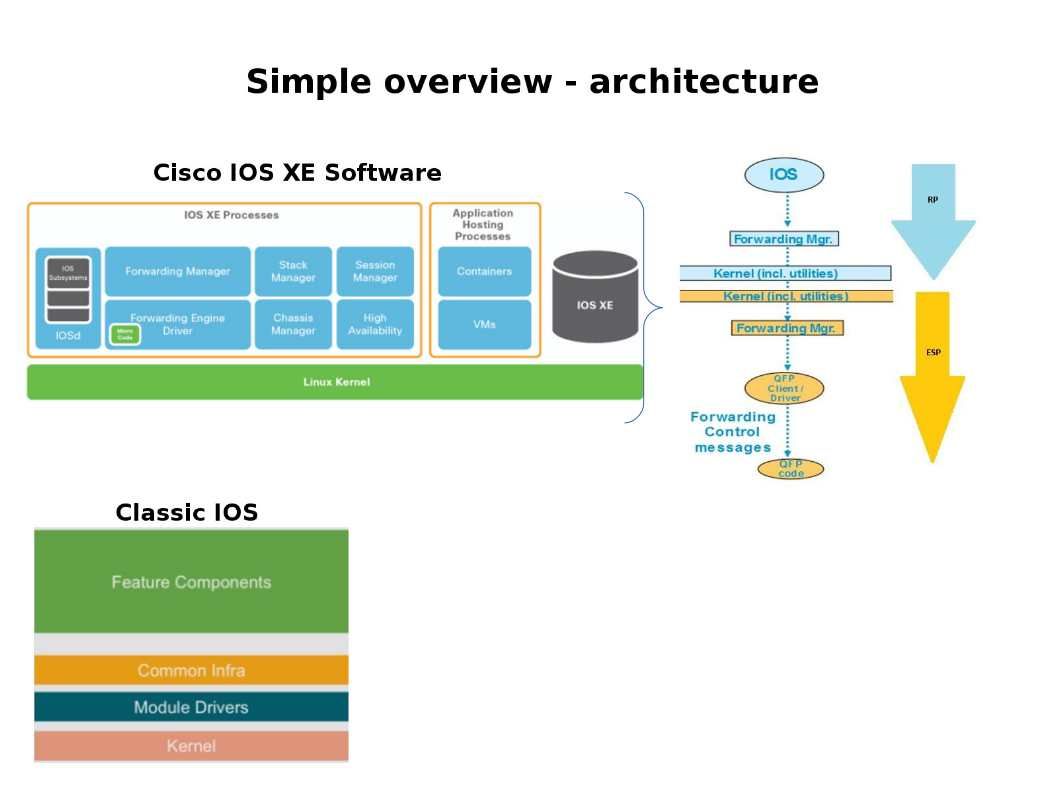
Since it runs a copy of IOS, all CLI commands are the same between Cisco IOS and IOS XE, in contrast to IOS XR which has a completely different code base and its developers implemented quite a different CLI command set.
IOS XE look like a docker container component.
Cisco has released several updates to address vulnerabilities affecting multiple products. An attacker could exploit some of these vulnerabilities to take control of an affected system.
Cisco IOS and IOS XE Software OSPFv3 Denial of Service Vulnerability(buffer overflow)
The vulnerability is due to incorrect handling of specific OSPFv3 packets. An attacker could exploit this vulnerability by sending crafted OSPFv3 Link-State Advertisements (LSA) to an affected device. An exploit could allow the attacker to cause an affected device to reload, leading to a denial of service (DoS) condition.
https://tools.cisco.com/security/center/content/CiscoSecurityAdvisory/cisco-sa-20180926-webdos
Cisco IOS and IOS XE Software SM-1T3/E3 Service Module Denial of Service Vulnerability
Cause the ISR G2 Router or the SM-1T3/E3 module on the ISR4451-X to reload, resulting in a denial of service (DoS) condition on an affected device.
https://tools.cisco.com/security/center/content/CiscoSecurityAdvisory/cisco-sa-20180926-sm1t3e3
Cisco IOS XE Software NAT Session Initiation Protocol Application Layer Gateway Denial of Service Vulnerability
Improper processing of SIP packets in transit while NAT is performed on an affected device.
https://tools.cisco.com/security/center/content/CiscoSecurityAdvisory/cisco-sa-20180926-sip-alg
Cisco IOS Software Precision Time Protocol Denial of Service Vulnerability
The vulnerability is due to insufficient processing of PTP packets. An attacker could exploit this vulnerability by sending a custom PTP packet to, or through, an affected device.
https://tools.cisco.com/security/center/content/CiscoSecurityAdvisory/cisco-sa-20180926-ptp
Cisco IOS and IOS XE Software IPv6 Hop-by-Hop Options Denial of Service Vulnerability
The vulnerability is due to incorrect handling of specific IPv6 hop-by-hop options. An attacker could exploit this vulnerability by sending a malicious IPv6 packet to or through the affected device.
https://tools.cisco.com/security/center/content/CiscoSecurityAdvisory/cisco-sa-20180926-ipv6hbh
Cisco IOS XE Software Command Injection Vulnerabilities
The vulnerabilities exist because the affected software improperly sanitizes command arguments, failing to prevent access to certain internal data structures on an affected device.
https://tools.cisco.com/security/center/content/CiscoSecurityAdvisory/cisco-sa-20180926-iosxe-cmdinj
Cisco IOS XE Software Errdisable Denial of Service Vulnerability
The vulnerability is due to a race condition that occurs when the VLAN and port enter an errdisabled state, resulting in an incorrect state in the software. An attacker could exploit this vulnerability by sending frames that trigger the errdisable condition. A successful exploit could allow the attacker to cause the affected device to crash, leading to a DoS condition.
https://tools.cisco.com/security/center/content/CiscoSecurityAdvisory/cisco-sa-20180926-errdisable
Cisco IOS and IOS XE Software Cluster Management Protocol Denial of Service Vulnerability
The vulnerability is due to improper input validation when handling Cluster Management Protocol (CMP) messages. An attacker could exploit this vulnerability by sending a malicious CMP message to an affected device.
https://tools.cisco.com/security/center/content/CiscoSecurityAdvisory/cisco-sa-20180926-cmp
Cisco IOS XE Software Cisco Discovery Protocol Memory Leak Vulnerability
The vulnerability is due to incorrect processing of certain CDP packets. An attacker could exploit this vulnerability by sending certain CDP packets to an affected device.
https://tools.cisco.com/security/center/content/CiscoSecurityAdvisory/cisco-sa-20180926-cdp-memleak
Cisco Webex Meetings Client for Windows Privilege Escalation Vulnerability
The vulnerability is due to folder permissions that grant a user the permission to read, write, and execute files in the Webex folders. An attacker could exploit this vulnerability to write malicious files to the Webex client directory, affecting all other users of the targeted device. A successful exploit could allow a user to execute commands with elevated privileges.
https://tools.cisco.com/security/center/content/CiscoSecurityAdvisory/cisco-sa-20180905-webex-pe
About vulnerabilities for NX-OS – status update 18th Oct 2018
Cisco NX-OS Software Authenticated Simple Network Management Protocol Denial of Service Vulnerability – The vulnerability is due to improper validation of SNMP protocol data units (PDUs) in SNMP packets.
https://tools.cisco.com/security/center/content/CiscoSecurityAdvisory/cisco-sa-20181017-nxos-snmp
Cisco NX-OS Software for Nexus 5500, 5600, and 6000 Series Switches Precision Time Protocol Denial of Service Vulnerability – The vulnerability is due to a lack of protection against PTP frame flood attacks.
Cisco FXOS and NX-OS Software Link Layer Discovery Protocol Denial of Service Vulnerability – The vulnerability is due to improper input validation of certain type, length, value (TLV) fields of the LLDP frame header.
https://tools.cisco.com/security/center/content/CiscoSecurityAdvisory/cisco-sa-20181017-fxnx-os-dos
