Official Revision Date: 2025-08-12
Preface: AMD SEV-SNP is a confidential computing hardware technology present in AMD EPYC processors from generation 3 and newer. It is based on hardware virtualization extensions and achieves isolation by adding these measures: Full memory encryption.
SEV-SNP is not solely located in the firmware. While the firmware plays a crucial role in SEV-SNP (Secure Encrypted Virtualization-Secure Nested Paging), it’s a combination of hardware, firmware, and software working together to provide the security features. The firmware initializes the SEV-SNP context and performs attestation, but the core functionality also relies on the AMD processor’s hardware and the guest operating system’s software components. For example: SEV-SNP is supported on AMD EYPC processors starting with the AMD EPYC 7003 series processors. AMD SEV-SNP offers powerful and flexible support for the isolation of a guest virtual machine from an untrusted host operating system. It is very useful in public cloud and any untrusted host scenario.
Background: SEV-SNP is designed to prevent software-based integrity attacks and reduce risk associated with compromised memory integrity. The basic principle of SEV-SNP integrity is that if a VM is able to read a private (encrypted) page of memory, it must always read the value it last wrote.
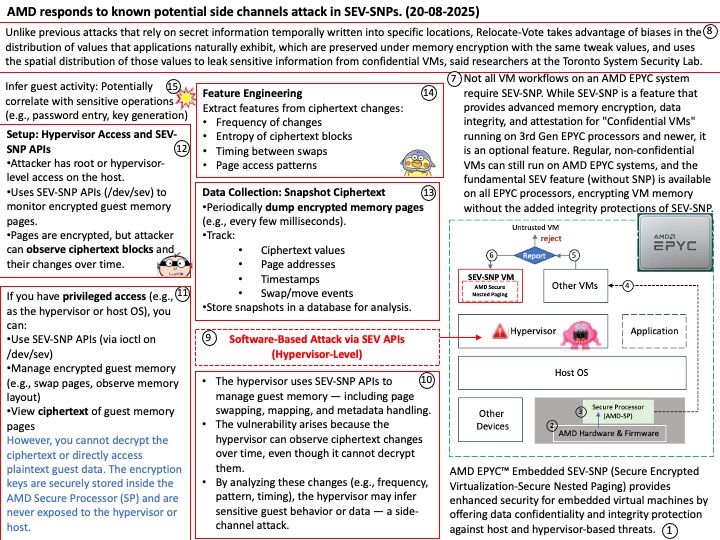
AMD SEV-SNP allows the hypervisor to move encrypted guest pages, including swapping pages to disk, but this capability can also be exploited through ciphertext side-channel attacks, where the hypervisor monitors ciphertext changes to infer guest data.
The findings of the two research teams:
AMD has received reports from two research groups detailing methods by which a malicious hypervisor could potentially execute a side channel attack against a running secure encrypted virtualization – secure nested paging (SEV-SNP) guest.
The first report, titled “Relocate + Vote: Exploiting Ciphertext Side-Channels using Sparsity Information,” was submitted by researchers at the Toronto System Security Lab of the University of Toronto.
A subsequent report from researchers at ETH Zurich titled “Chosen Plaintext Oracle against SEV-SNP,” outlines a similar exploitation technique that also leverages the ability to move or swap guest pages.
Official announcement: For more information, please refer to the link:
https://www.amd.com/en/resources/product-security/bulletin/amd-sb-3021.html