Preface: SAP Adaptive Server Enterprise (SAP ASE) Protocol – Originally designed for Unix platforms in 1987 under the name Sybase SQL Server, it was renamed Sybase ASE, then renamed again when SAP bought Sybase. It is often used for online transaction management on location and in the cloud.
Background: The new SAP Adaptive Server Platform Edition (ASPE) is a packaged database solution consisting of SAP ASE, SAP IQ, and SAP Replication Server that provides.
SAP ASPE licenses SAP ASE, IQ, and Replication Server belonging to the ASPE suite in the form you want. You can choose within your license. Users can reconfigure their licenses at any time in any combination at no additional cost. This is provided to select an appropriate IT solution in a rapidly changing business processing environment. Mission-Critical OLTP From business support to data warehousing (DW) business analysis applications, disaster recovery (DR)/load balancing and data replication are supported.
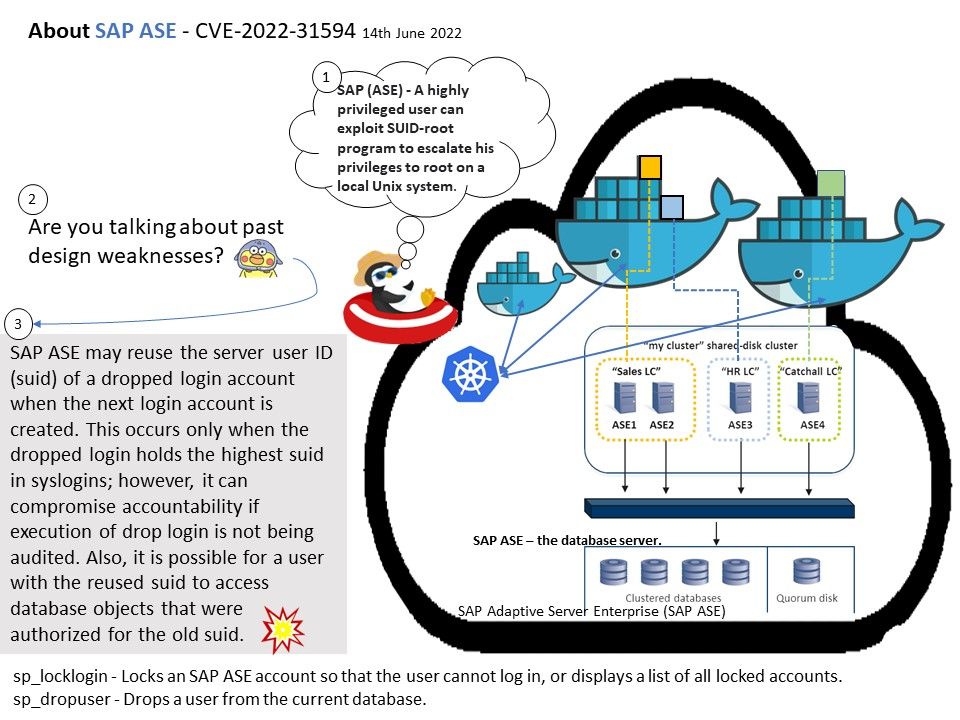
Vulnerability details: A highly privileged user can exploit SUID-root program to escalate his privileges to root on a local Unix system.
Since the supplier did not describe the details. But the following situation would be one of the ways to trigger this design weakness.
SAP ASE may reuse the server user ID (suid) of a dropped login account when the next login account is created. This occurs only when the dropped login holds the highest suid in syslogins; however, it can
compromise accountability if execution of drop login is not being audited. Also, it is possible for a user with the reused suid to access database objects that were authorized for the old suid.
Solution (Preventive control): If the above details are correct with the technical issues of the subject. According to SAP ASE security practices. You are avoid to do the following.
You cannot drop a login when:
● The user is in any database.
● The login is the last remaining user who holds the system security officer or system administrator roles.
The system security officer can lock or drop a login using sp_locklogin or drop login. If the system procedure is being logged for replication, the system security officer must be in the master database when issuing the command.
Official announcement: SAP Patch Day Blog – https://www.sap.com/documents/2022/02/fa865ea4-167e-0010-bca6-c68f7e60039b.html