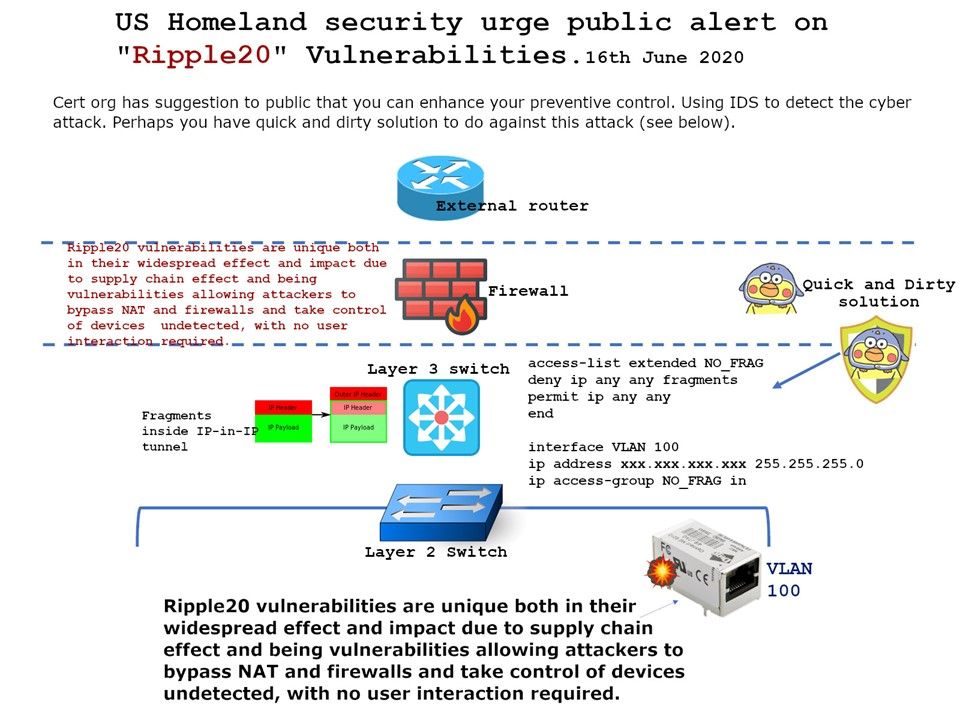
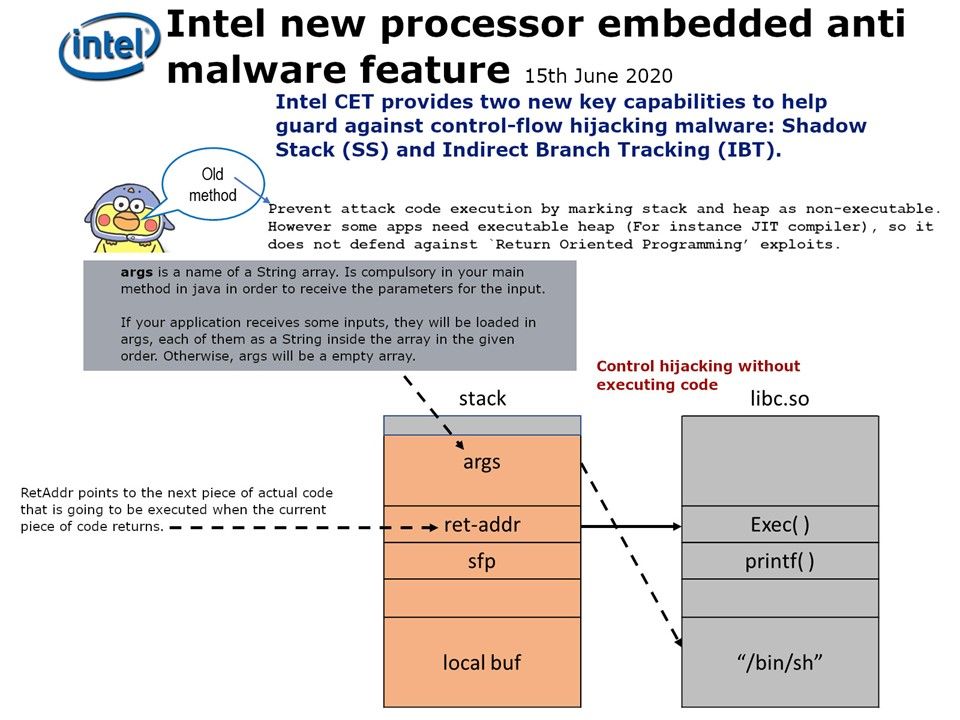
Preface: Currently, there are no known workarounds or mitigations for these vulnerabilities. Thankfully, the Redmond adds that the flaws are not publicly disclosed and that there are no known exploits in the wild. The firm credits Trend Micro’s Zero Day Initiative for privately disclosing the bugs.
Background:
From security point of view, attacker who keen to bypassing Windows Heap Protection traditionally by re-use method. However Microsoft had build heap protection since windows XP SP2 age. As of today, generic heap exploitation approaches not effective. There is no more easy write4. But attacker can relies on application technique. Which means controlling the controlling the algorithm to position data carefully on the heap. The historical method like Multiple Write4 with a combination of the Lookaside and the FreeList.
Microsoft has released security updates to address vulnerabilities in Windows 10.
https://portal.msrc.microsoft.com/en-US/security-guidance/advisory/CVE-2020-1457
https://portal.msrc.microsoft.com/en-US/security-guidance/advisory/CVE-2020-1425
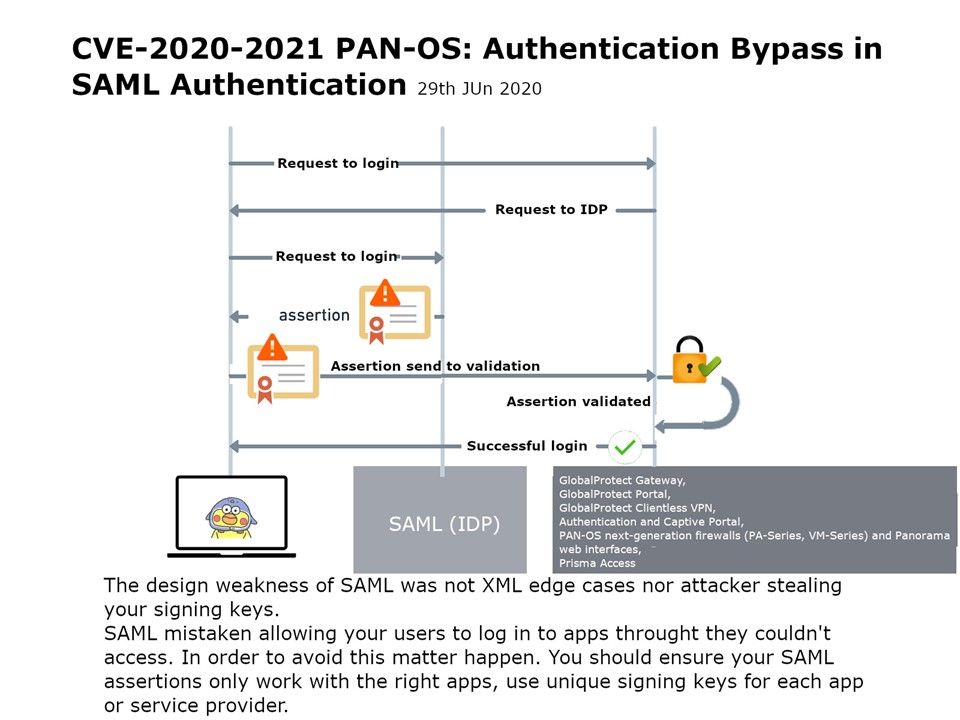
.jpg?width=1920&height=1080&fit=bounds)
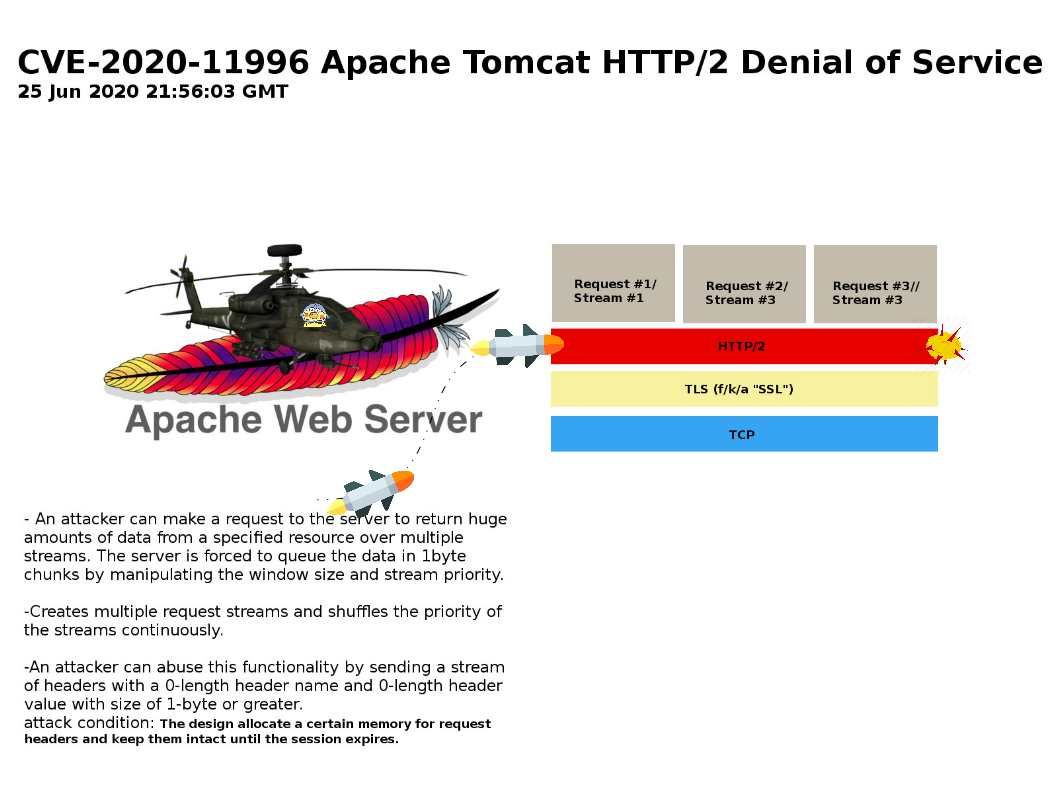


.jpg)