Preface: Human being life average 80 year old. Explorering space is a long time travel. So, it only relies on machine.
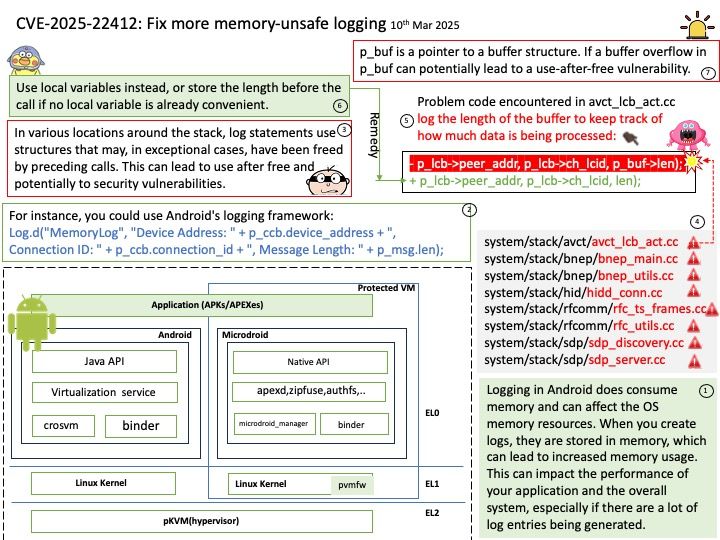
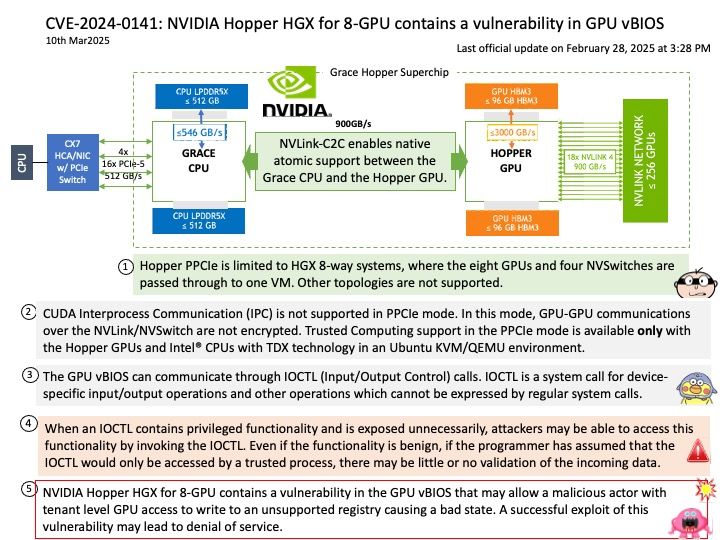
Even though exploring machine can relies on solar energy. In space there is a lot of uncertainty. For example, the shock of meteorite. Furthemore, the spacecraft operates in a unique environment, the spacecraft’s power system must also be able to operate in zero gravity and vacuum conditions, and be able to withstand large amounts of radiation (most electronic equipment will not operate in such an environment). On our earth also have gravity seems not want human being leave our earth. Believed it or not, this is our destiny.
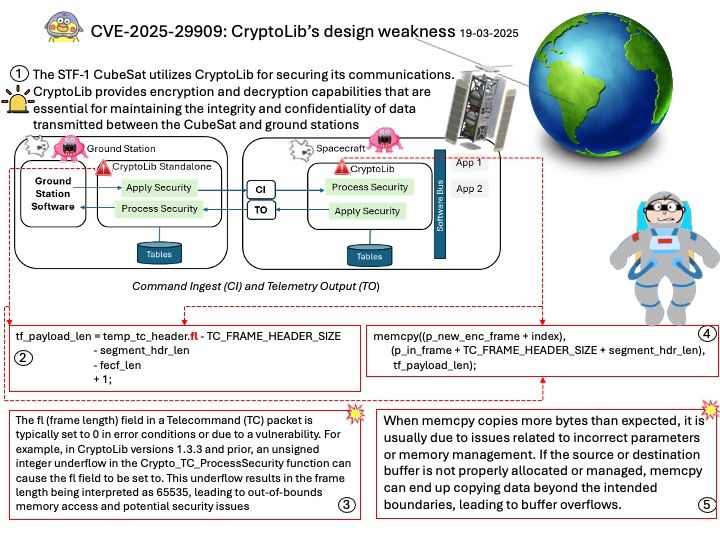
Background: CryptoLib is indeed used in space technology! It provides a C-based software implementation of the CCSDS Space Data Link Security Protocol (SDLS) and SDLS Extended Procedures (SDLS-EP) to secure communications between spacecraft flight software and ground stations. This library supports various encryption libraries and protocols, including Telecommand (TC), Telemetry (TM), and Advanced Orbiting Systems (AOS).
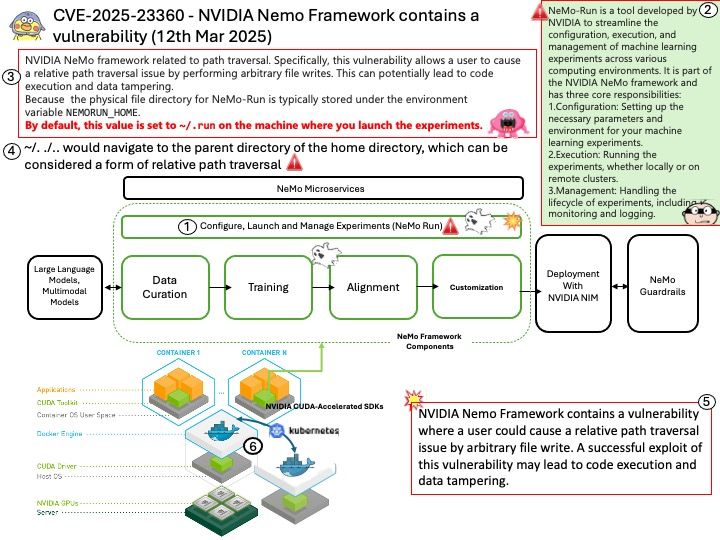
CryptoLib is designed to support smaller missions with stringent size, weight, and power constraints, making it a valuable tool for secure satellite communications.
Vulnerability details: CryptoLib provides a software-only solution using the CCSDS Space Data Link Security Protocol – Extended Procedures (SDLS-EP) to secure communications between a spacecraft running the core Flight System (cFS) and a ground station. In versions 1.3.3 and prior, a heap buffer overflow vulnerability in CryptoLib’s `Crypto_TC_ApplySecurity()` allows an attacker to craft a malicious TC frame that causes out-of-bounds memory writes. This can result in denial of service (DoS) or, under certain conditions, remote code execution (RCE). Any application or system that relies on CryptoLib for Telecommand (TC) processing and does not strictly validate incoming TC frames is at risk. This includes satellite ground stations or mission control software where attackers can inject malformed frames.
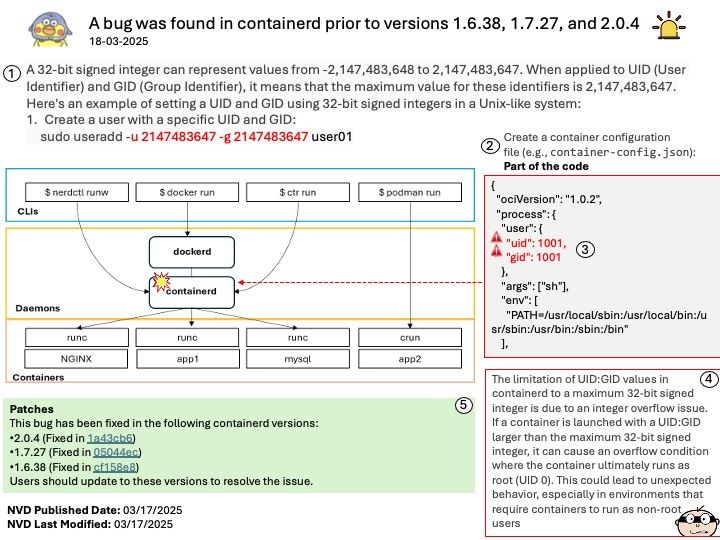
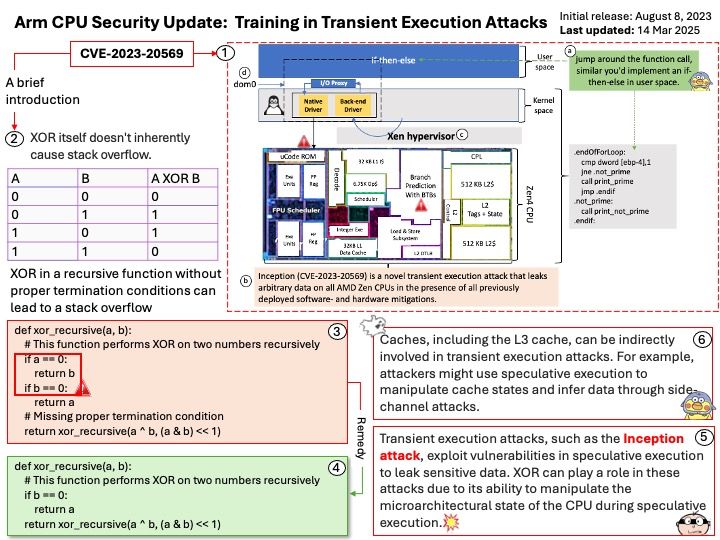
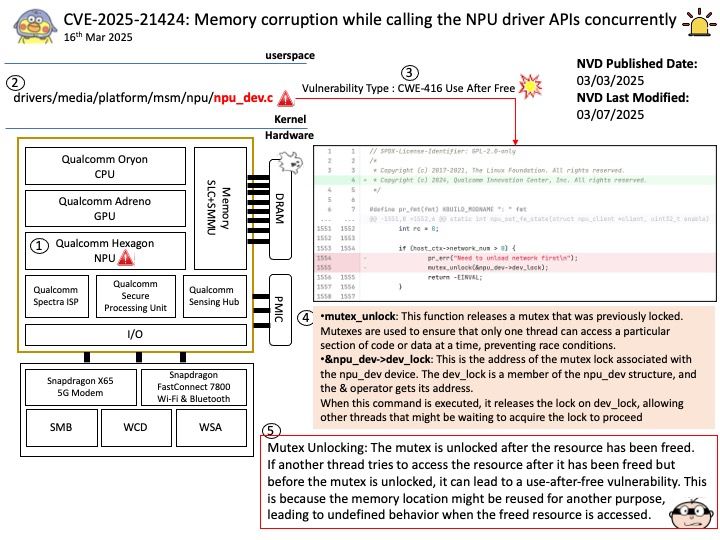
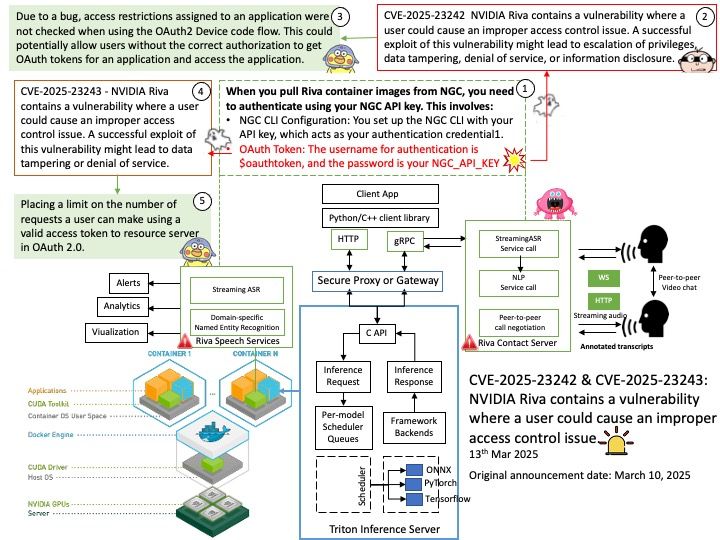
Official announcement: Please refer to the link for details – https://nvd.nist.gov/vuln/detail/CVE-2025-29909