Preface: Is ASN-1 still in use? ASN-1 is used to define a large number of protocols. Its most widespread applications remain in telecommunications, cryptography, and biometrics.
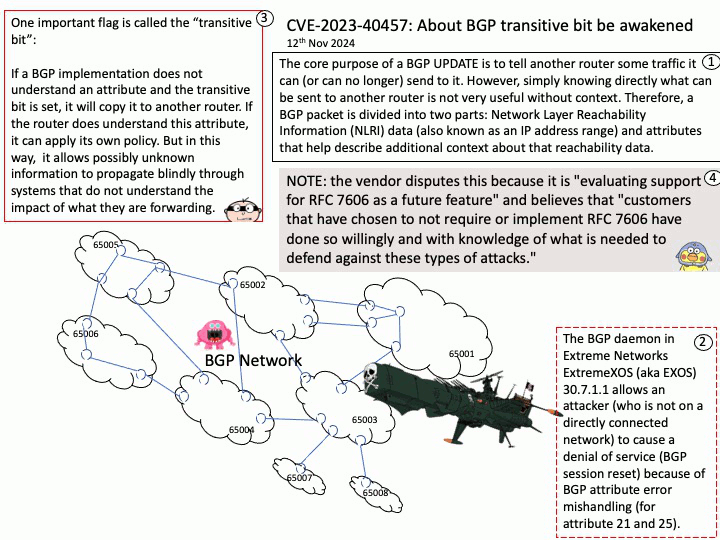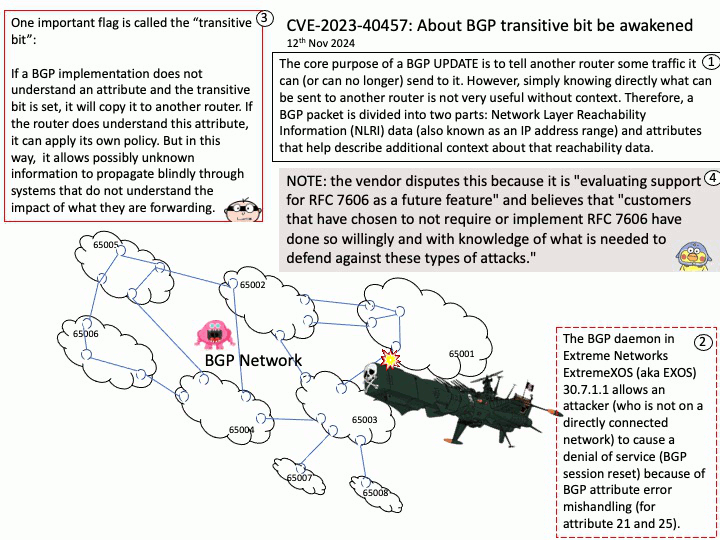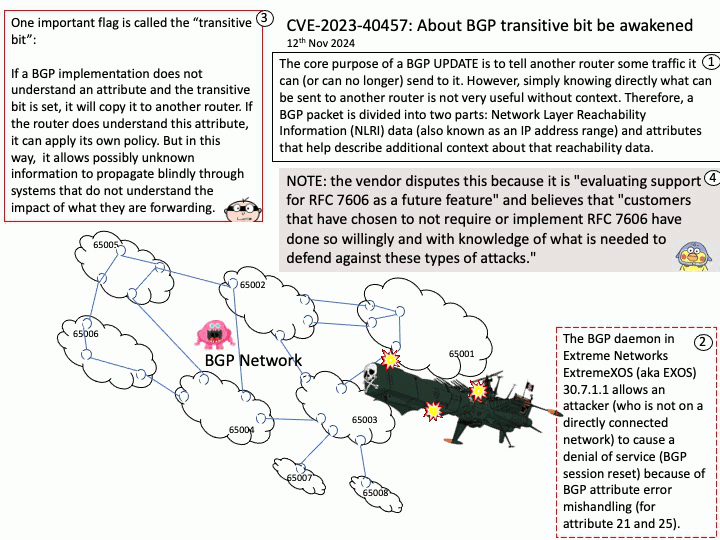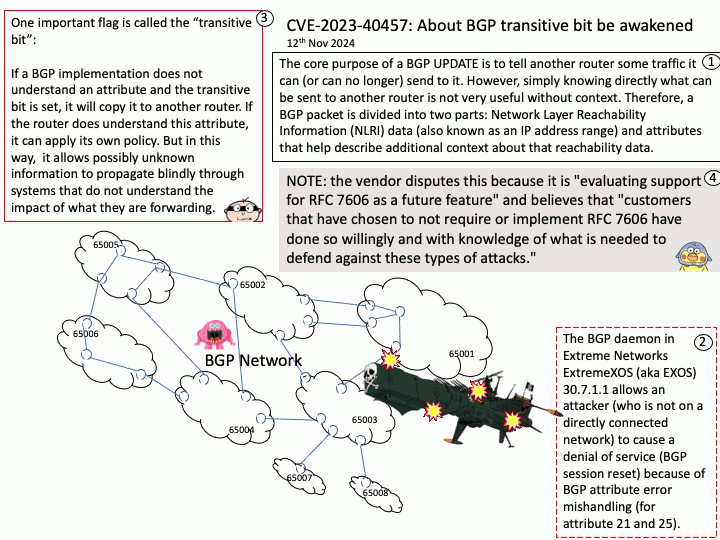
ASN.1 is used in protocols like TLS and LDAP/Active Directory because it provides a language and platform independent way to define data structures, making it a standard for interoperability. Its encoding rules, such as Basic Encoding Rules (BER), offer a compact and efficient binary format for data transmission. Additionally, ASN.1 is used to formally define security standards, such as those in X.509 certificates, which are critical for establishing secure connections in TLS and authenticating users in LDAPIt often features in security vulnerabilities involving TLS and LDAP/Active Directory.
Background: ASN.1 (Abstract Syntax Notation dotone) is a standard for defining abstract data types and is used to describe data representation, transmission, and encoding.
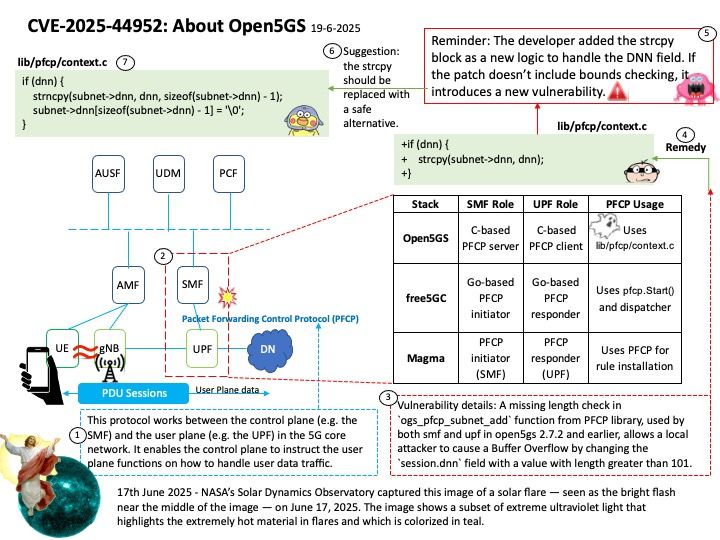
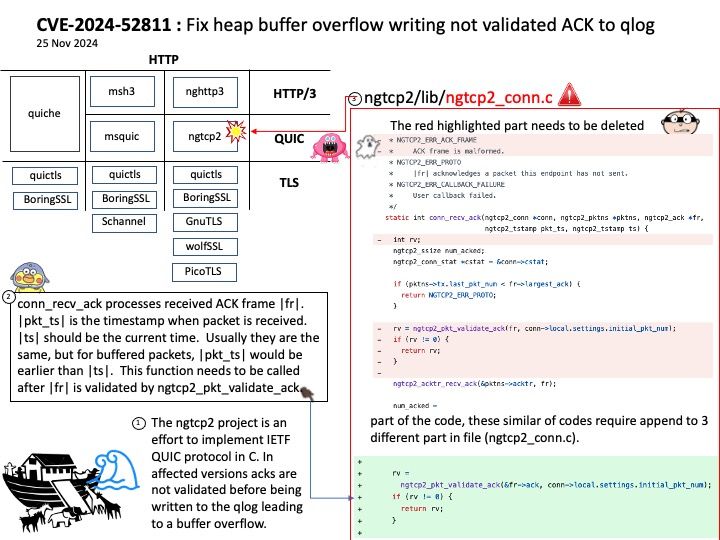
ASN.1 includes data type definitions, data description syntax, encoding rules, etc. BER and DER are one type of encoding rule.
DER is a subset of BER, and it defines an encoding method that uses an octet string to represent any ASN.1 value. DER is used for applications that require encoding with a unique octet string, such as calculating digital signatures based on an ASN.1 encoding. DER is defined in Section 8.7 of X.509.
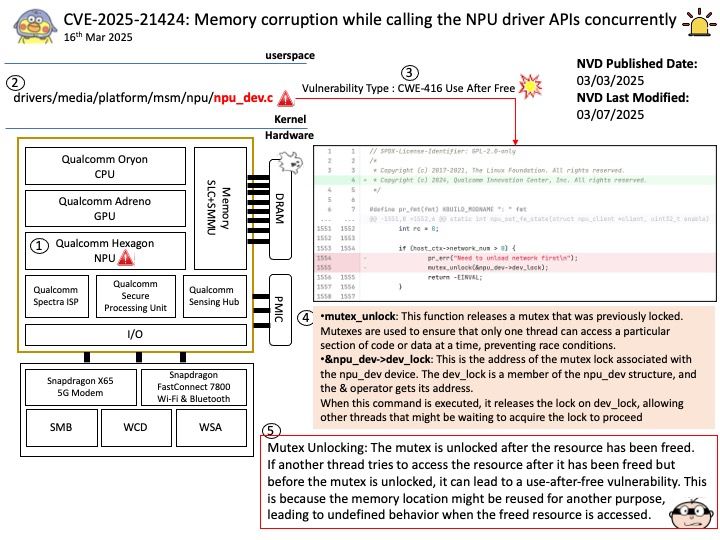
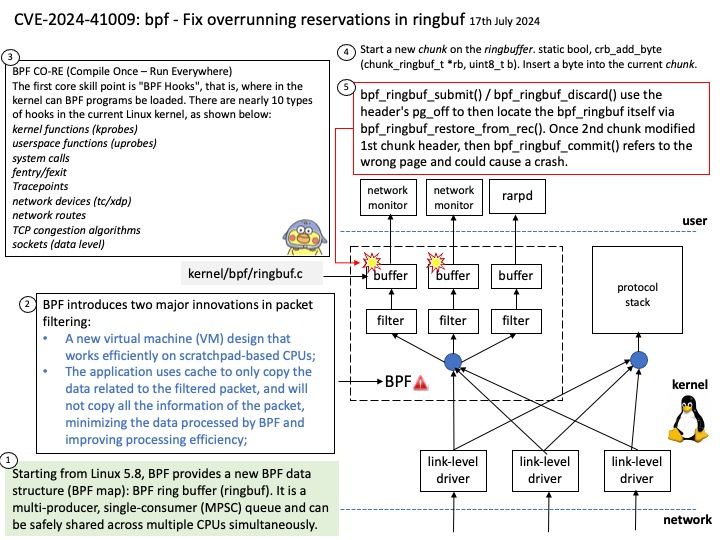
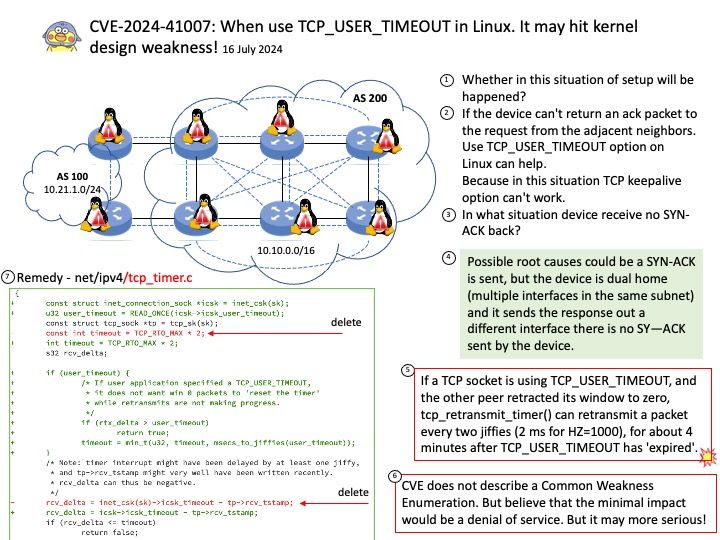
Vulnerability details: When parsing DER payloads, memories were being allocated prior to fully validating the payloads.
This permits an attacker to craft a big empty DER payload to cause memory exhaustion in functions such as asn1.Unmarshal, x509.ParseCertificateRequest, and ocsp.ParseResponse.
Official announcement: Please refer to the link for details –