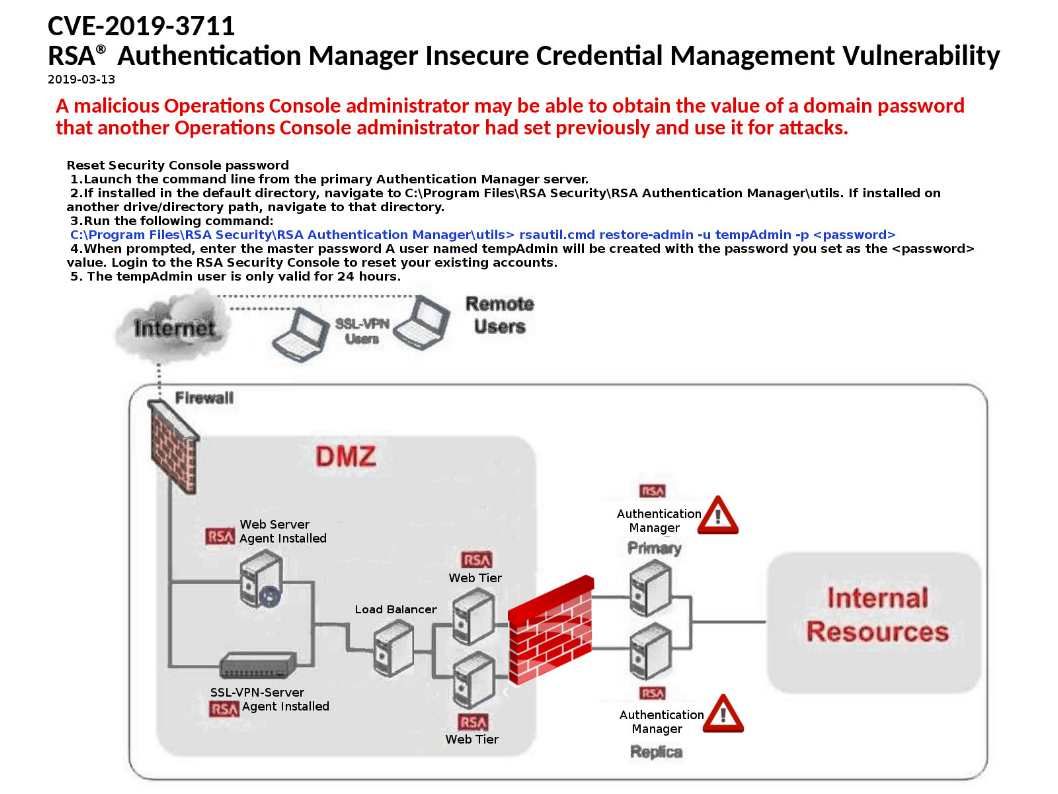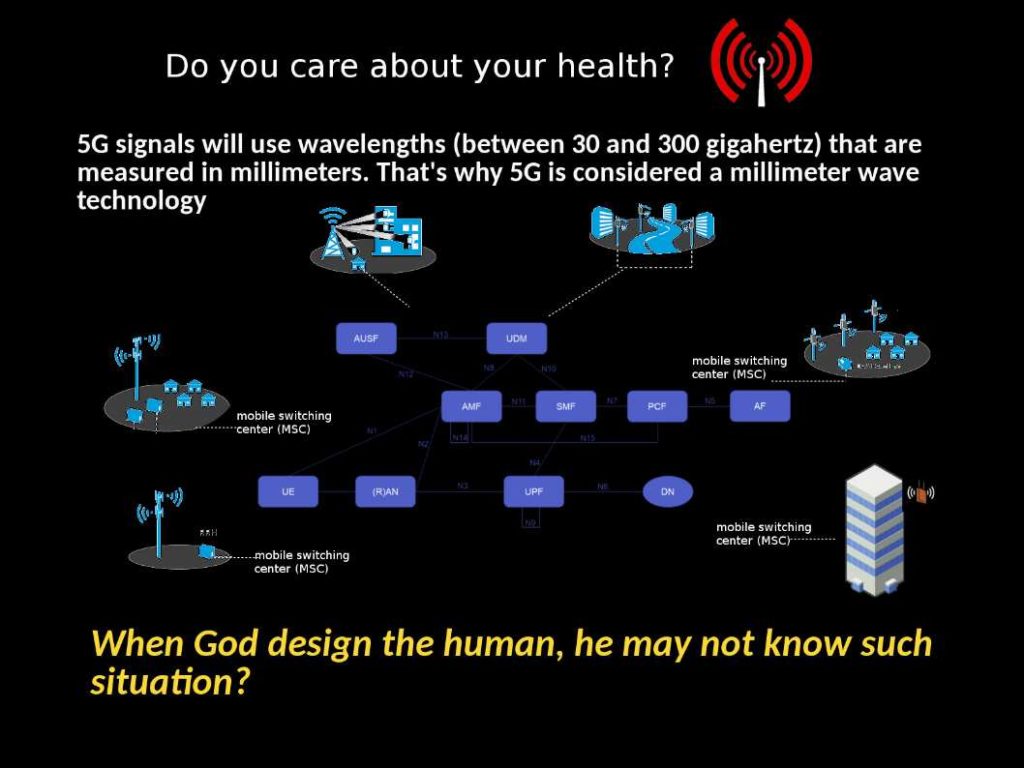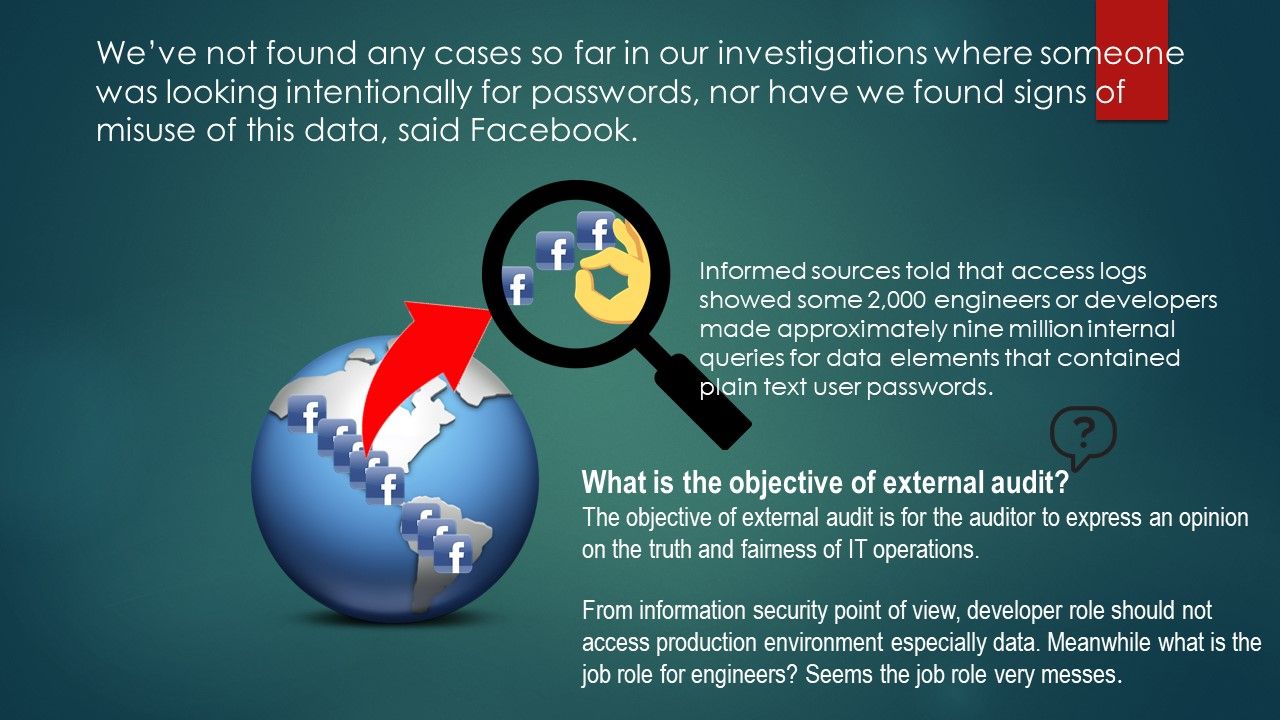
Preface: Analyzing big data not so easy.
Synopsis: Analyzing big data not so easy. It requires knowledge of enterprise search engines for making content from different sources like enterprise database, social media, sensor data etc. searchable to a defined audience. Elasticsearch is one of the free and open source enterprise search software.
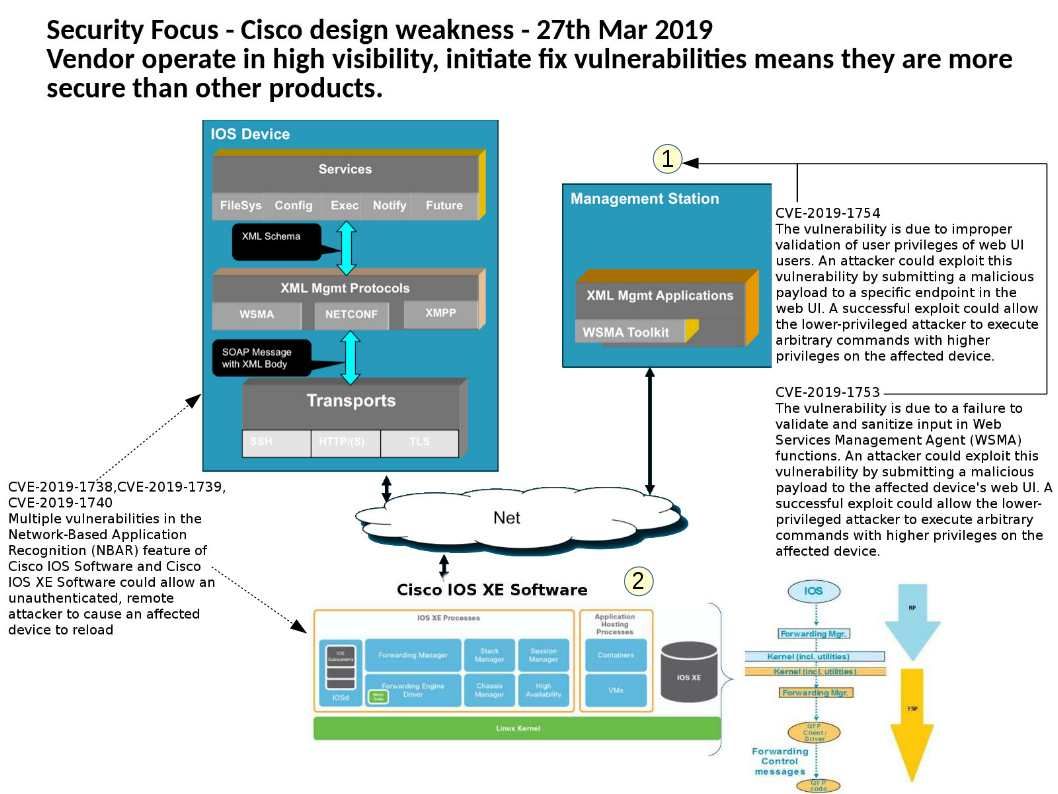
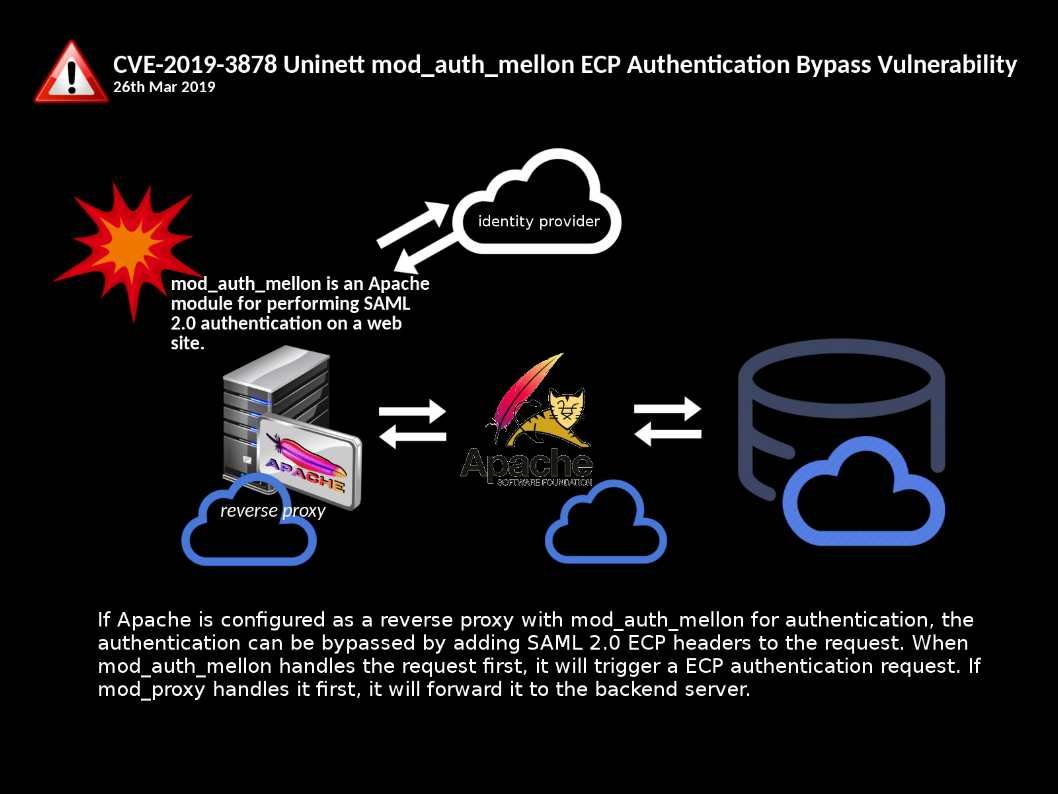
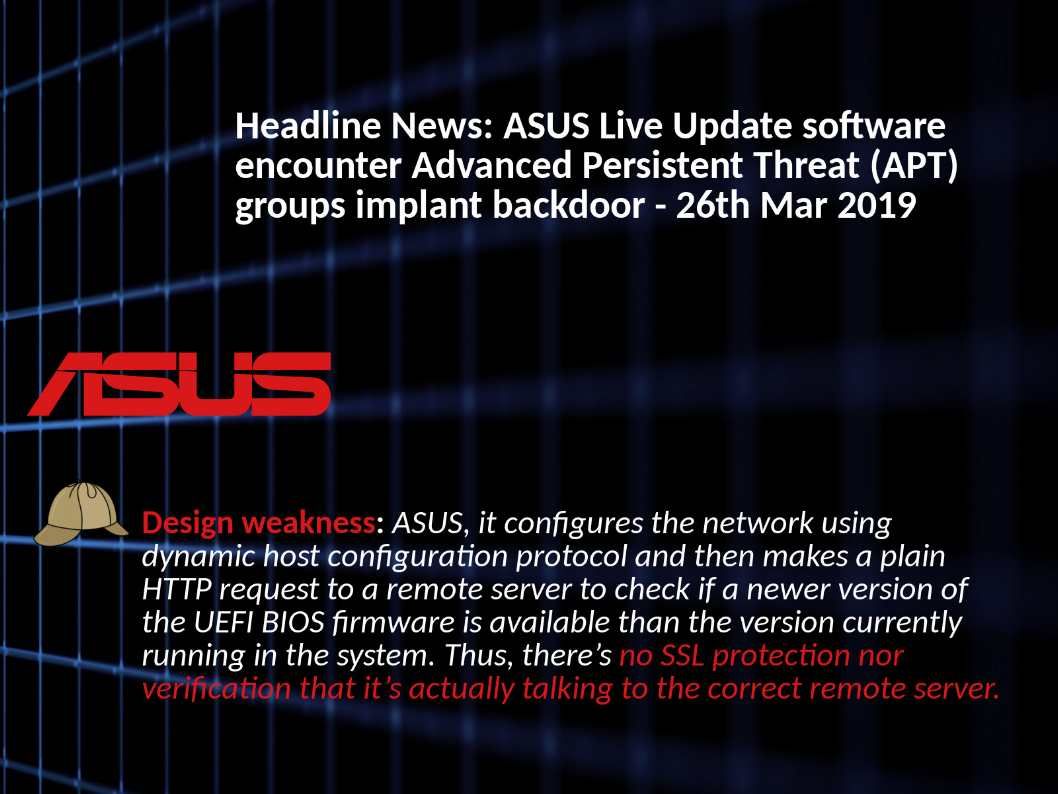
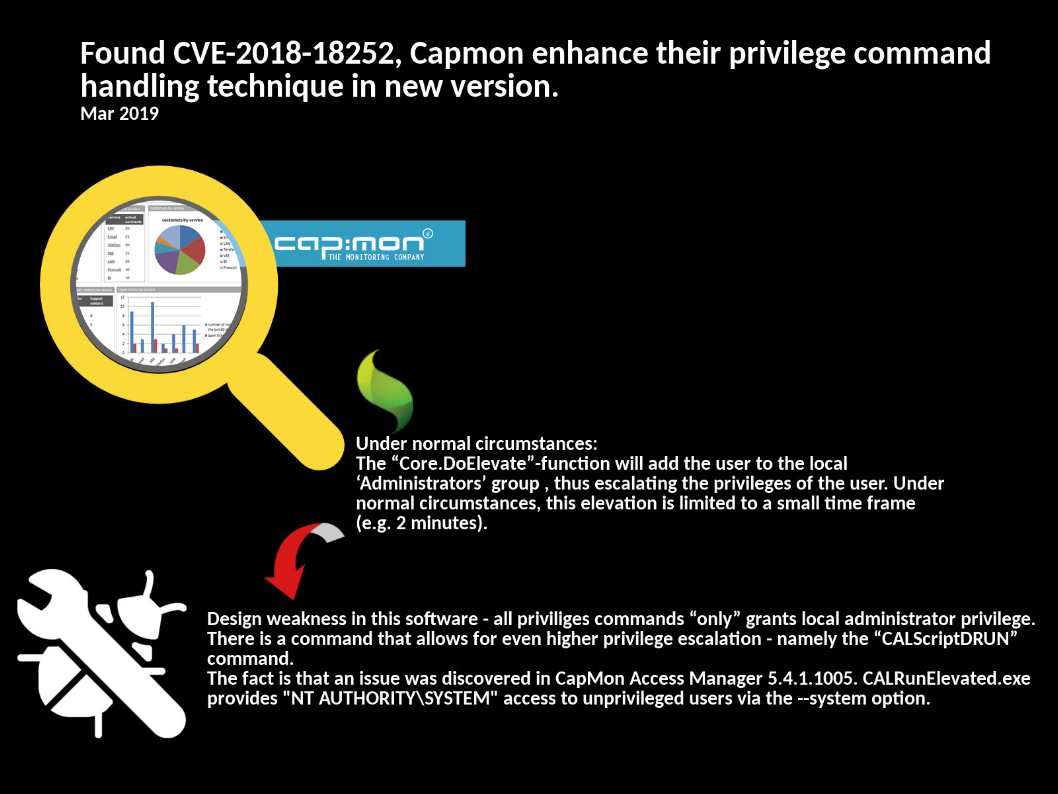
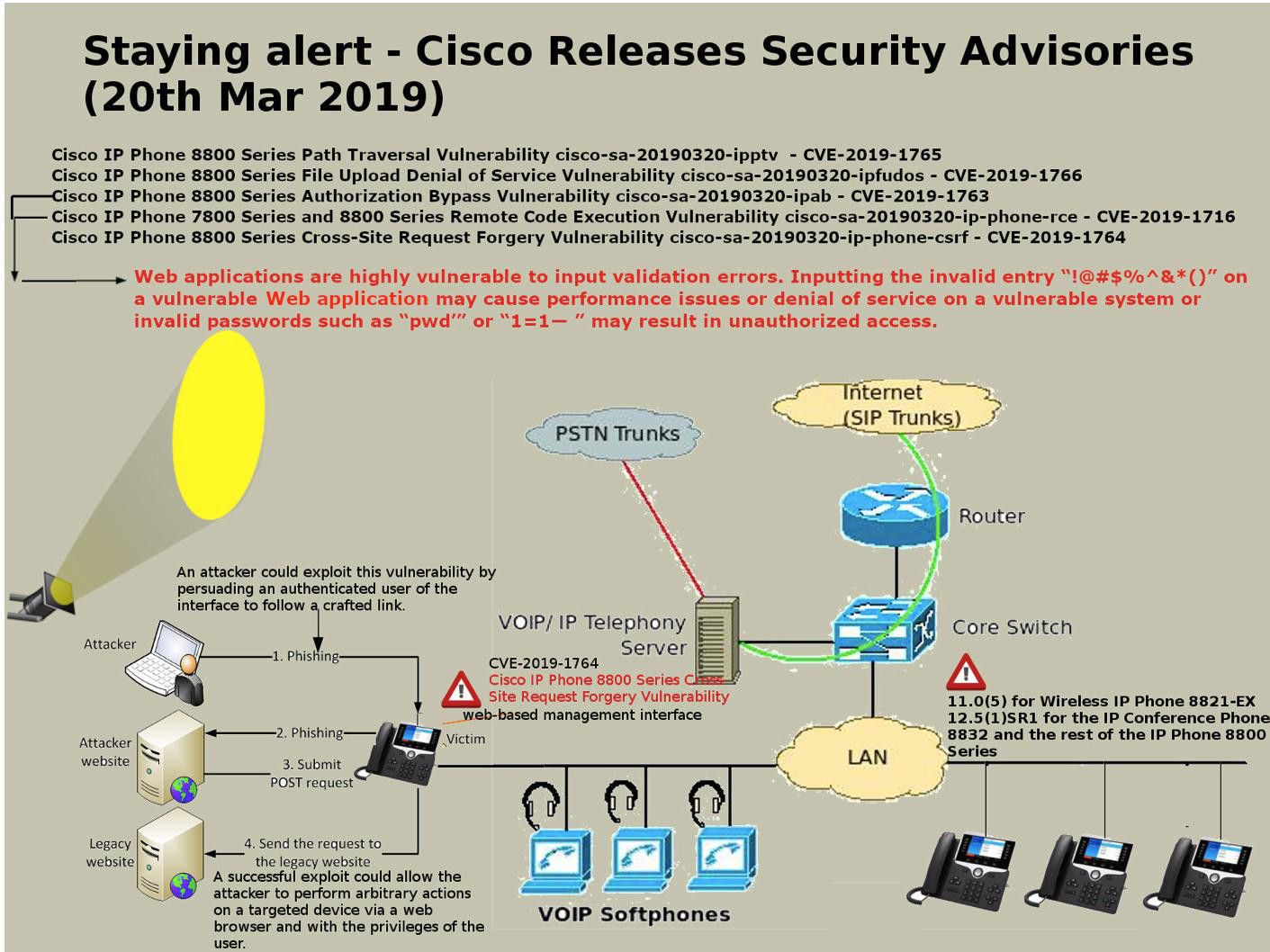
Vulnerability detail: The vulnerability exists because the affected software mishandles user-supplied input. An attacker could exploit this vulnerability by sending requests that submit malicious input to the affected software.
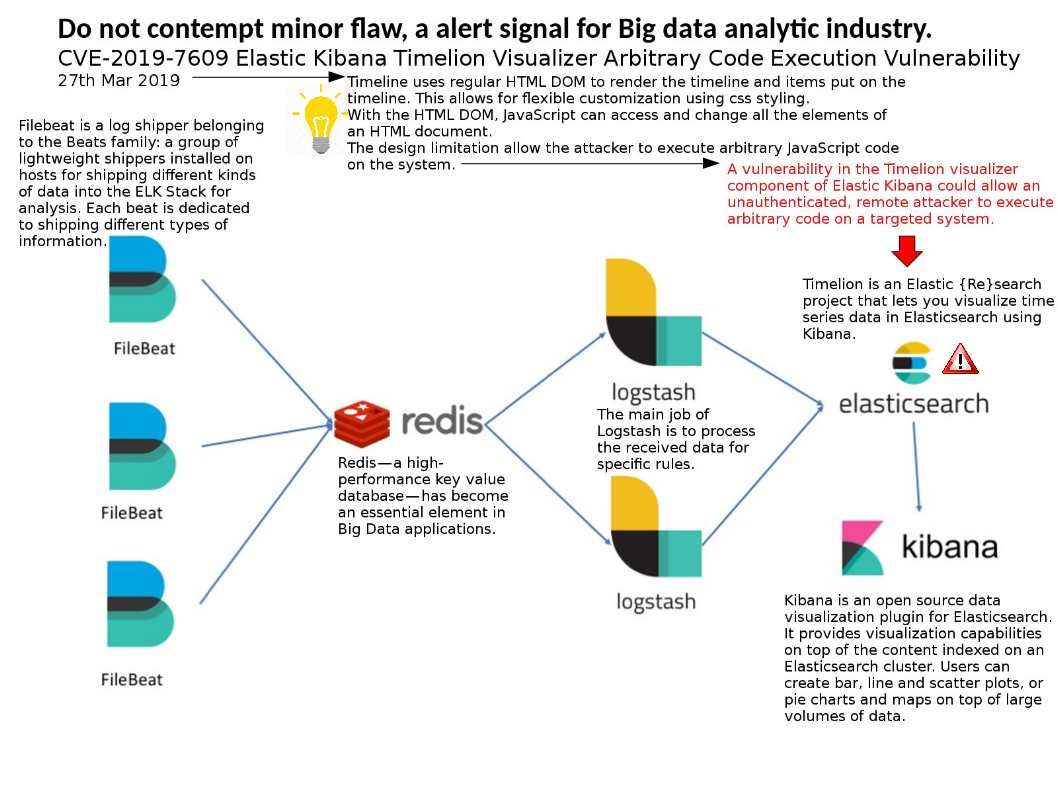
Causes: Timeline uses regular HTML DOM to render the timeline and items put on the timeline. This allows for flexible customization using css styling.
With the HTML DOM, JavaScript can access and change all the elements of an HTML document.
The design limitation allow the attacker to execute arbitrary JavaScript code on the system.
Remedy: Refer to URL – https://discuss.elastic.co/t/elastic-stack-6-6-1-and-5-6-15-security-update/169077