Preface: DevOps philosophy by practices, and tools that improve an organisation’s ability to deliver applications and services. This enables products to be developed and improved at a faster rate than organisations using traditional software development and infrastructure management processes. Efficiency, fast is the slogan of business. Step next phase after digital transformation. DevOps is important because it’s a software development and operations approach that enables faster development of new products and easier maintenance of existing deployments. Meanwhile, high efficiency boots-up productivity. Side effect is that electricity consumption will be increasing. A chain effect driver everything including natural resources. As a result in such a way of this chain effect generation the environment pollution. Our overall temperate become high and high annually. If an entrepreneur can let industry progress in our world slow down. He can rescue the world.
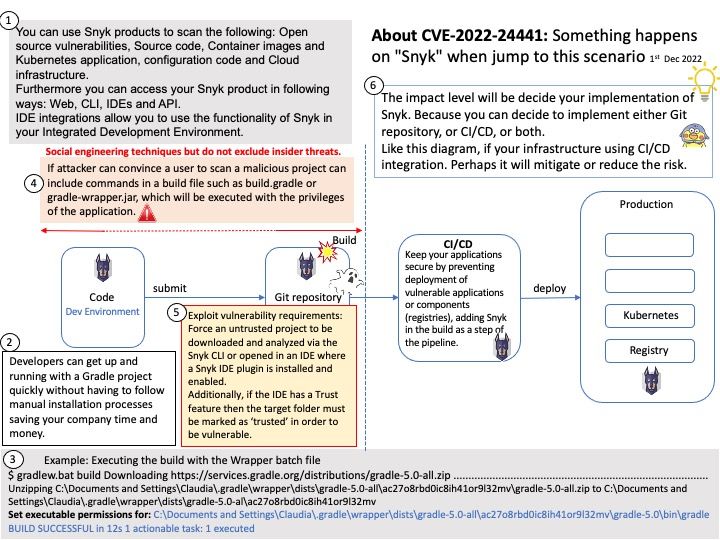
Background: Snyk (pronounced sneak) is a developer security platform for securing code, dependencies, containers, and infrastructure as code. You can use Snyk products to scan the following: Open source vulnerabilities, Source code, Container images and Kubernetes application, configuration code and Cloud infrastructure. Furthermore you can access your Snyk product in following ways: Web, CLI, IDEs and API.
IDE integrations allow you to use the functionality of Snyk in your Integrated Development Environment.
Vulnerability details: The package snyk before 1.1064.0 are vulnerable to Code Injection when analyzing a project. An attacker who can convince a user to scan a malicious project can include commands in a build file such as build.gradle or gradle-wrapper.jar, which will be executed with the privileges of the application. This vulnerability may be triggered when running the the CLI tool directly, or when running a scan with one of the IDE plugins that invoke the Snyk CLI. Successful exploitation of this issue would likely require some level of social engineering – to coerce an untrusted project to be downloaded and analyzed via the Snyk CLI or opened in an IDE where a Snyk IDE plugin is installed and enabled. Additionally, if the IDE has a Trust feature then the target folder must be marked as ‘trusted’ in order to be vulnerable.
REF: Exploit vulnerability requirements: Force an untrusted project to be downloaded and analyzed via the Snyk CLI or opened in an IDE where a Snyk IDE plugin is installed and enabled.
Additionally, if the IDE has a Trust feature then the target folder must be marked as ‘trusted’ in order to be vulnerable.
Remark: The impact level will be decide your implementation of Snyk. Because you can decide to implement either Git repository, or CI/CD, or both.
Like this diagram, if your infrastructure using CI/CD integration. Perhaps it will mitigate or reduce the risk.
Solution: Upgrading to a fixed version for this addresses that issue as well. Refer to official announcement for details.
Official announcement: Please refer to the link for details – https://security.snyk.io/vuln/SNYK-JS-SNYK-3111871