Preface: HTTP Host header attacks exploit vulnerable websites that handle the value of the Host header in an unsafe way.
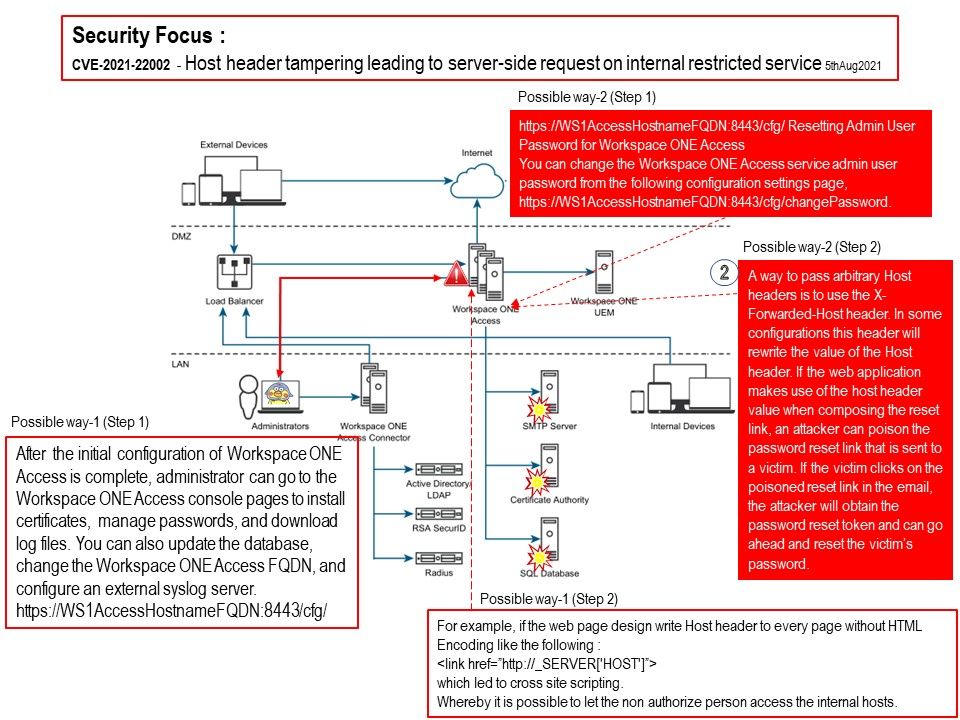
Background: After the initial configuration of Workspace ONE Access is complete, administrator can go to the Workspace ONE Access console pages to install certificates, manage passwords, and download log files. You can also update the database, change the Workspace ONE Access FQDN, and configure an external syslog server.
How do I access VMware Identity Manager?
You can log in to the VMware Identity Manger console from your Workspace ONE portal page. To log in directly to the console,
VMware Identity Manager admin users can enter the following URL [/]SAAS[/]login[/]0.
Vulnerability details: The vulnerability exists due to insufficient validation of user-supplied input in the [/]cfg web app and diagnostic endpoints. A remote attacker can send a specially crafted HTTP request with a modified HTTP Host header to port 443[/]TCP and access the[ /]cfg web application, available at port 8443. As a result, a remote non-authenticated attacker can gain access to services in the internal network.
Official announcement – Please refer to the link https://www.vmware.com/security/advisories/VMSA-2021-0016.html