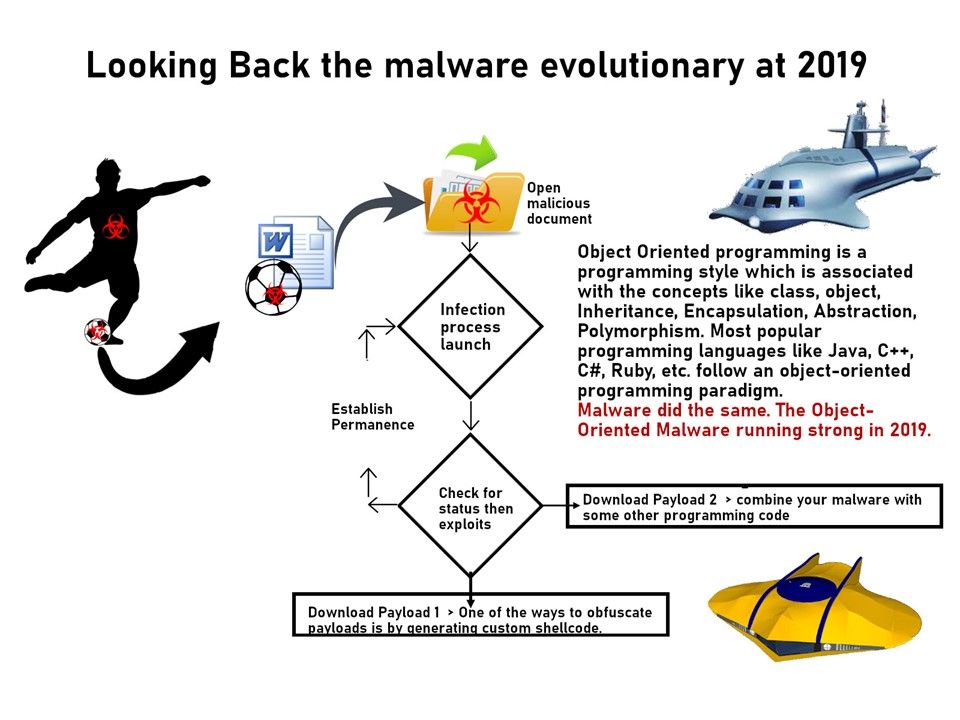
Preface: Unlike C, C++ is an object-oriented programming language, following a programming model that uses objects that contain data as well as functions to manipulate the data. Word is an object-oriented program.
Security focus: The malware author usually exploit some kind of arbitrary code execution or zero day. And therefore it have chances to evade the anti-defense mechanism detection.
The reason behind is that before reassemble of the modules, it do not take any action. But perhaps you have doubt?
How do they get another module? In modern defense technology, the machanism of the malware detector will be based on blacklist domain for the first piority. If attacker compromise a web site not included in domain blacklist. So, when download other module by http or https traffic might not detected by defense machanism. As a matter of fact, the http get and put action are frequently happens in our internet web browsing. Therefore you will understand that why does cyber criminals target to compromising a boutique shop style web site and social media. It was because the web sites still in white list before compromise.
Should you have interested to know more. F5 Lab has article for your reference. A Reference Guide to the Malware Family Tree – https://www.f5.com/labs/articles/education/banking-trojans-a-reference-guide-to-the-malware-family-tree