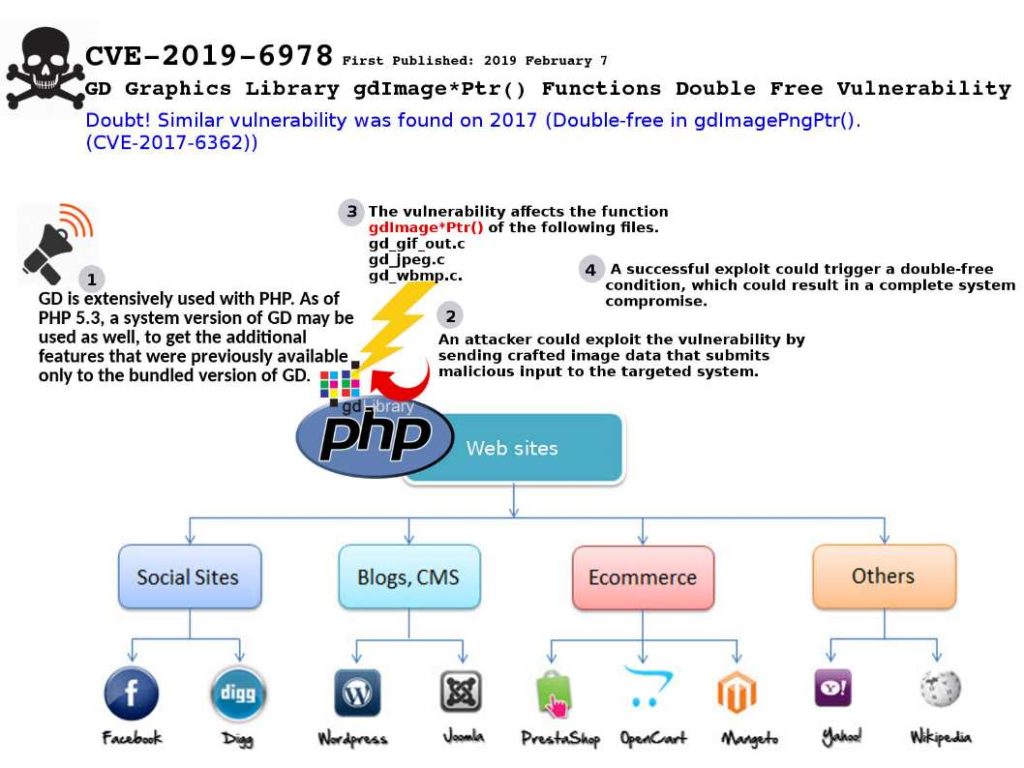
Preface: GD is extensively used with PHP. As of PHP 5.3, a system version of GD may be used as well, to get the additional features that were previously available only to the bundled version of GD.
Technical background: The LibGD 2.2.5 allow to written C code to load an entire image file into a buffer in memory, then ask gd to read the image from that buffer. But the programmer must responsible for allocating the buffer, apart from that a customized function must responsible for freeing the buffer with your normal memory management functions.
Vulnerability found: A vulnerability in GD Graphics Library (libgd) could allow an unauthenticated, remote attacker to execute arbitrary code on a targeted system.
Doubt: Similar vulnerability was found on 2017 (Double-free in gdImagePngPtr(). (CVE-2017-6362)).
LibGD 2.2.5 release announced that Double-free in gdImagePngPtr(). (CVE-2017-6362) has been fixed!
Vendor announcements: https://github.com/libgd/libgd/issues/492