Preface: If an SDK contains a use-after-free (UAF) vulnerability, the consequences can range from minor data corruption and program crashes to severe security issues like arbitrary code execution, information leakage, and privilege escalation, as the vulnerability allows attackers to manipulate previously freed memory, leading to system instability or full compromise.
Background: Classic and Low Energy devices use different hardware and software stacks: Bluetooth® Classic devices can´t communicate with Bluetooth® Low Energy and vice versa. As for some applications, the power consumption of Bluetooth® Classic is still too high. The Bluetooth® SIG developed a standard lower power consumption to overcome this obstacle.
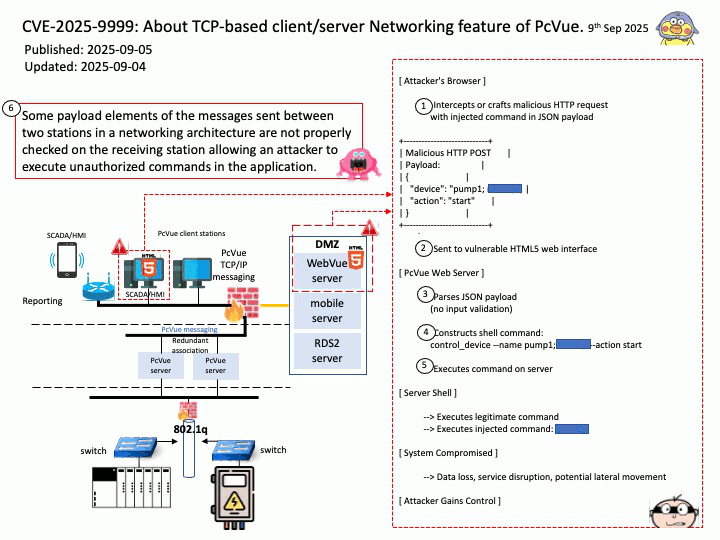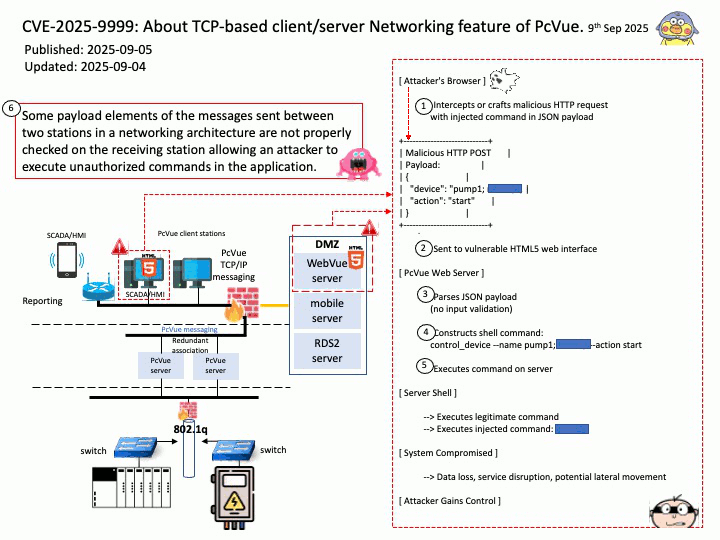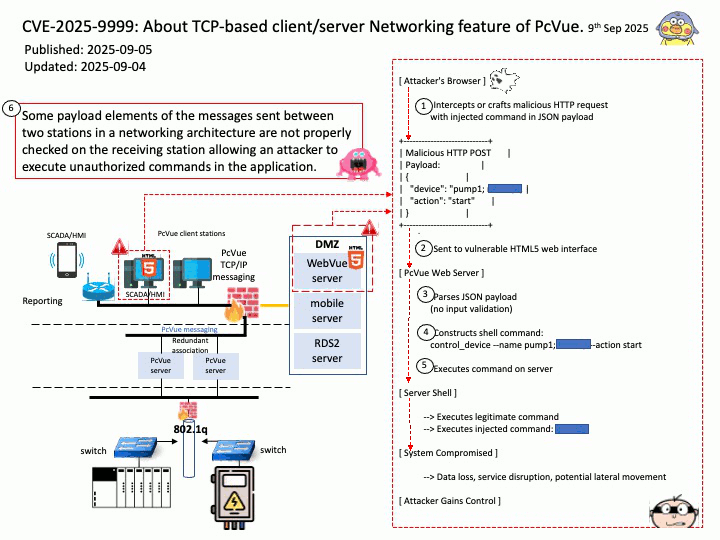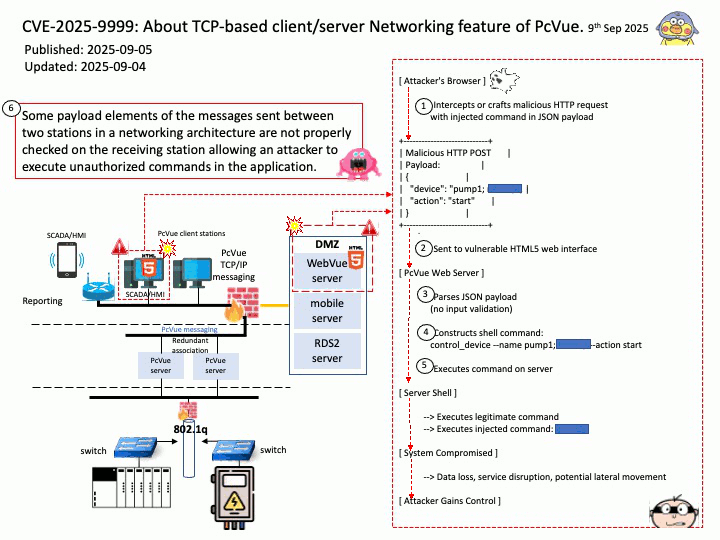
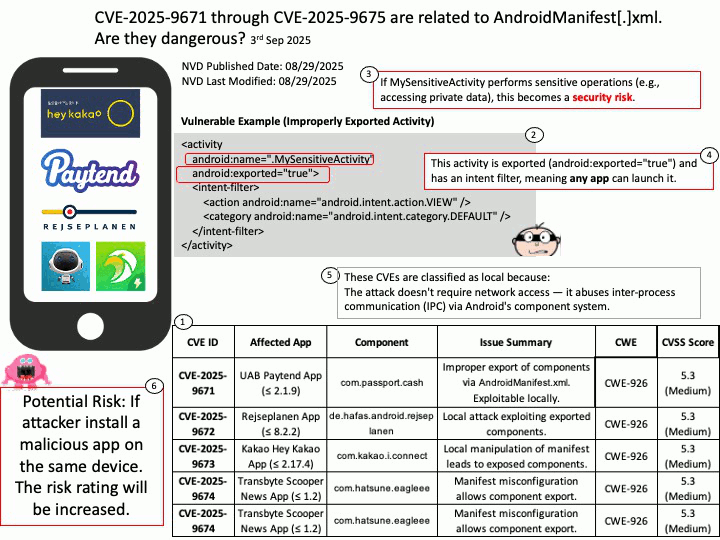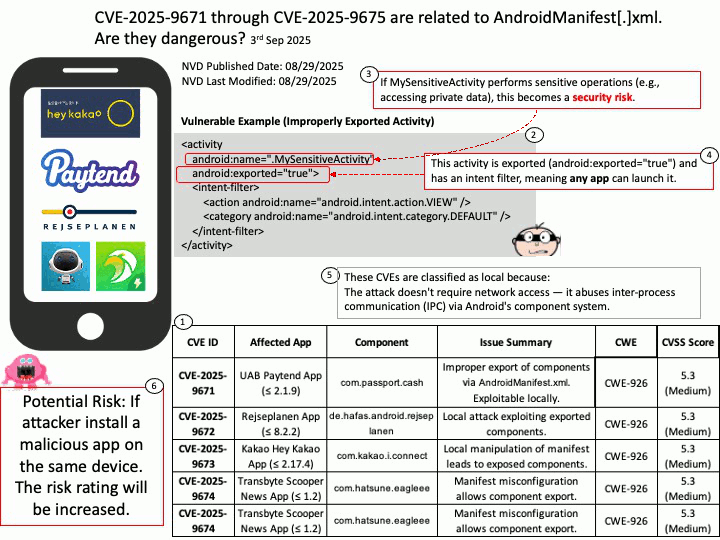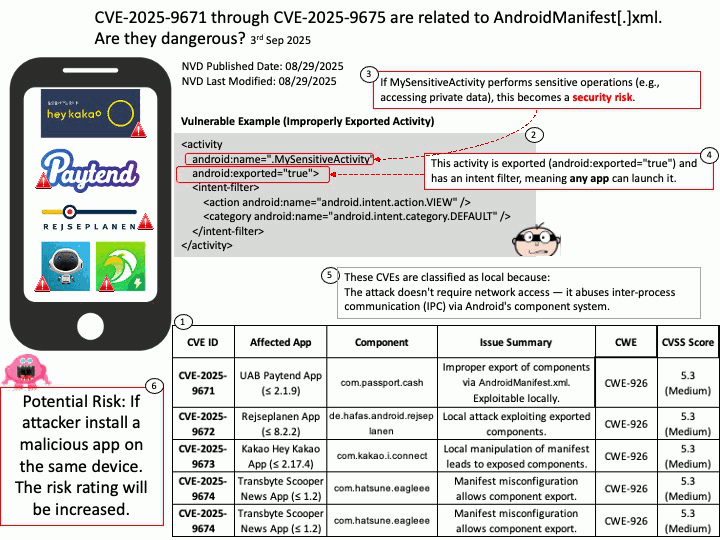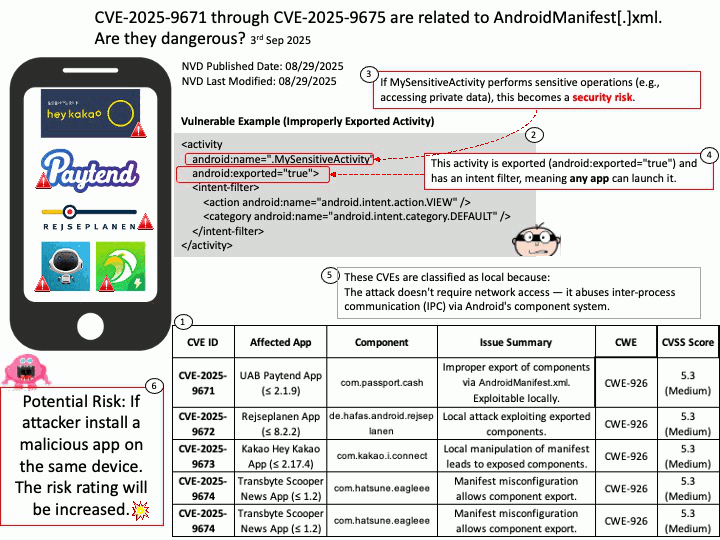
Vulnerability details: OpenSynergy BlueSDK (aka Blue SDK) through 6.x has a Use-After-Free. The specific flaw exists within the BlueSDK Bluetooth stack. The issue results from the lack of validating the existence of an object before performing operations on the object (aka use after free). An attacker can leverage this to achieve remote code execution in the context of a user account under which the Bluetooth process runs.
This vulnerability was part of a broader exploit chain called PerfektBlue, which affected millions of vehicles from:
- Volkswagen (ICAS3)
- Mercedes-Benz (NTG6)
- Škoda (MIB3)
- And an unnamed OEM
Attackers could:
- Send crafted AVRCP packets post-pairing
- Trigger the use-after-free
- Overwrite function pointers
- Achieve remote code execution (RCE) in the infotainment system
Official announcement: Please see the link for details –