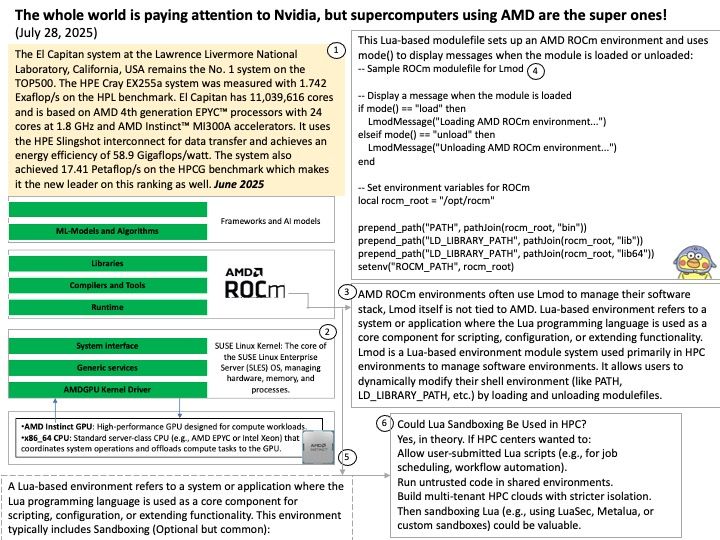
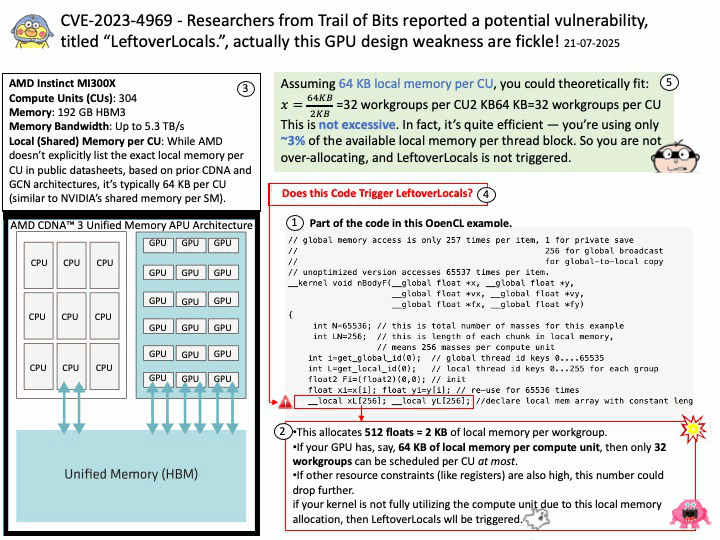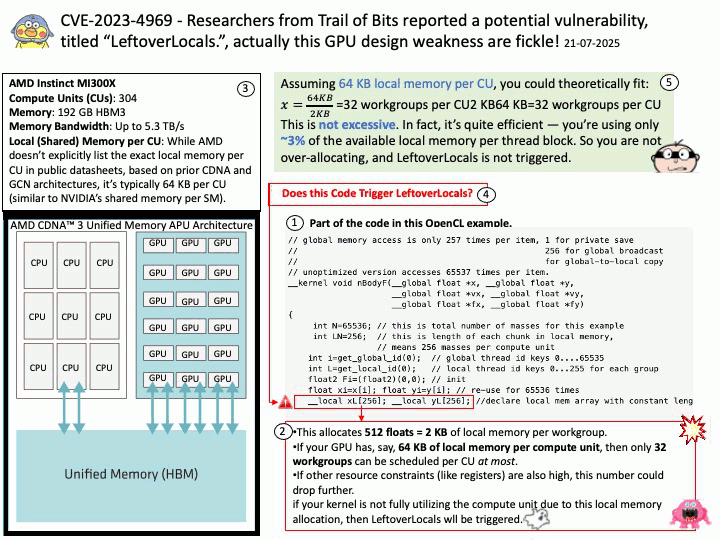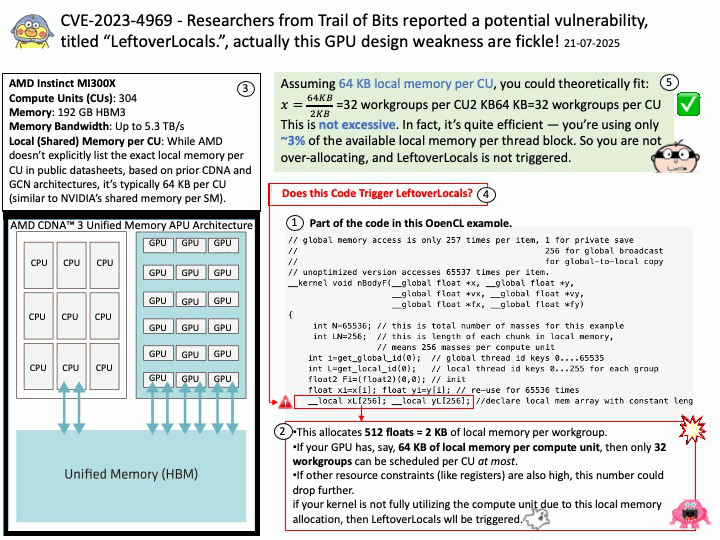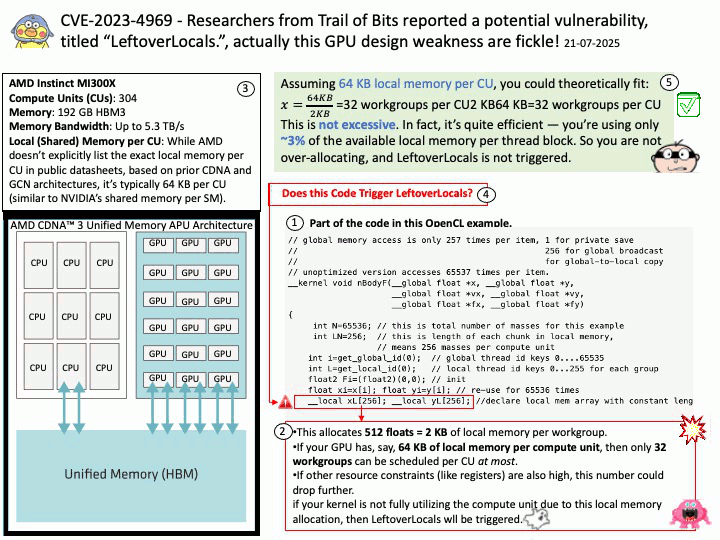
Preface: In essence, built-in browsers are not just about browsing; they are about maintaining control over the core functionality and user experience of the operating system.
Background: Safari and Edge, while built-in, utilize rendering engines derived from the KHTML project, specifically WebKit and Blink, respectively. WebKit is used in Safari, and Blink, a fork of WebKit, powers the Chromium-based Edge. These engines are not just for browsing; they handle the visual rendering of web content within the browser.
In Safari and Edge, the rendering engines (WebKit for Safari and Chromium for Edge) initially interact with the networking component to fetch the necessary resources for a webpage. This workflow prioritizes efficient data retrieval, enabling the browser to display content to the user as quickly as possible.
Safari’s rendering engine, WebKit, is developed and maintained by Apple, according to Apple. WebKit is an open-source project that was originally forked from KDE’s KHTML and KJS engines. Safari is a web browser developed by Apple and is the default browser on macOS, iOS, iPadOS, and visionOS.
Vulnerability details: An out-of-bounds access issue was addressed with improved bounds checking. This issue is fixed in macOS Sequoia 15.6, iPadOS 17.7.9, iOS 18.6 and iPadOS 18.6, tvOS 18.6, macOS Sonoma 14.7.7, watchOS 11.6, visionOS 2.6, macOS Ventura 13.7.7. Processing maliciously crafted web content may lead to an unexpected Safari crash.
Ref: Out-of-Bounds Read (e.g., CVE-2025-43209)
-Reads memory outside the allocated buffer.
-Can leak: Pointers (used to bypass ASLR) or Object metadata (used for type confusion).
-Often used as a first stage in a multi-step exploit.
Official announcement: Please refer to the link for details https://nvd.nist.gov/vuln/detail/CVE-2025-43209