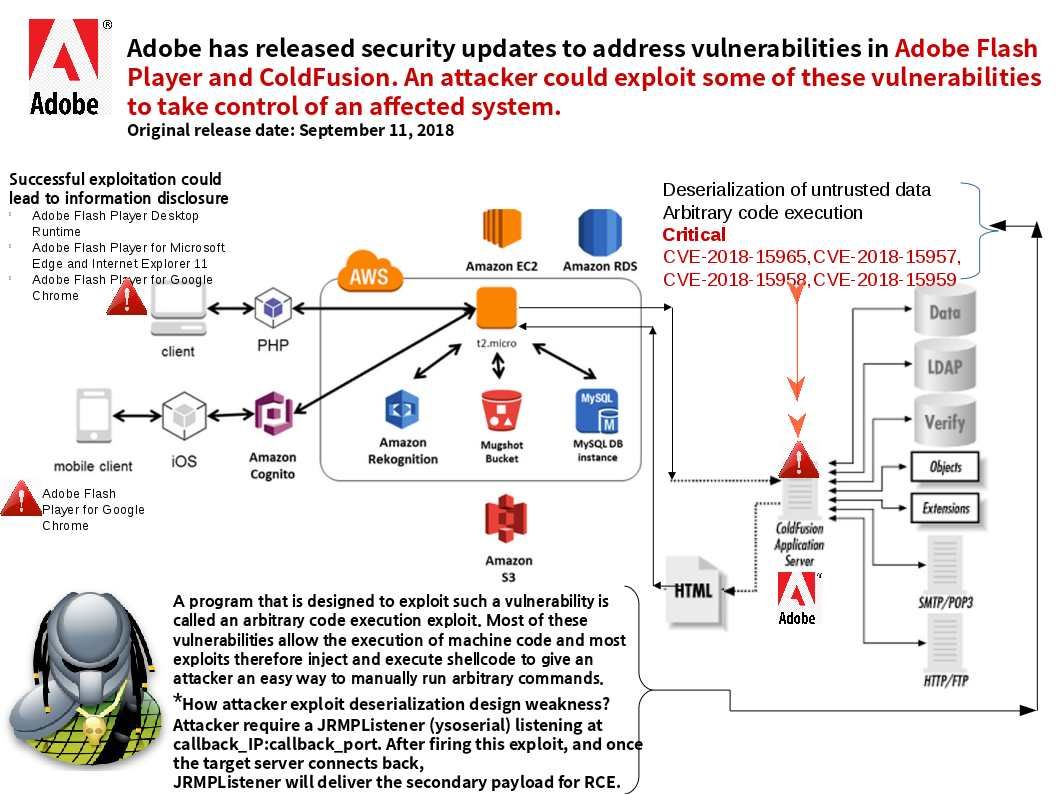
Adobe revealed that the Flash end of life will take place at the end of 2020. So we still can be use the flash. Perhaps computer products includes software and hardware.The key word vulnerability similar human not feeling well (sick) then receive medication. The patient will get well. So vulnerability occurs in cyber world do not give people any suprise! The vulnerabilities found in Adobe product not limit to Flash Player this week. Adobe ColdFusion is a commercial rapid web application development platform created by J. J. Allaire in 1995.Medical software manufacturer uses Adobe ColdFusion to more securely collect electronic clinical outcome assessment (eCOA) data.Digital solutions company uses Adobe ColdFusion to help midmarket companies manage eCommerce more effectively. Adobe has released security updates to address vulnerabilities in Adobe Flash Player and ColdFusion.
Adobe Security Bulletin can provides above details, see below:
ColdFusion – https://helpx.adobe.com/security/products/coldfusion/apsb18-33.html
Flash Player – https://helpx.adobe.com/security/products/flash-player/apsb18-31.html