Preface: What if , design weakness not directly effect the software component. Is it a vulnerability? Or, can we ignore?
Background: What is the difference between DNS and nameservers?
DNS records are what contain the actual information that other browsers or services need to interact with, like your server’s IP address. Nameservers, on the other hand, help store and organize those individual DNS records.
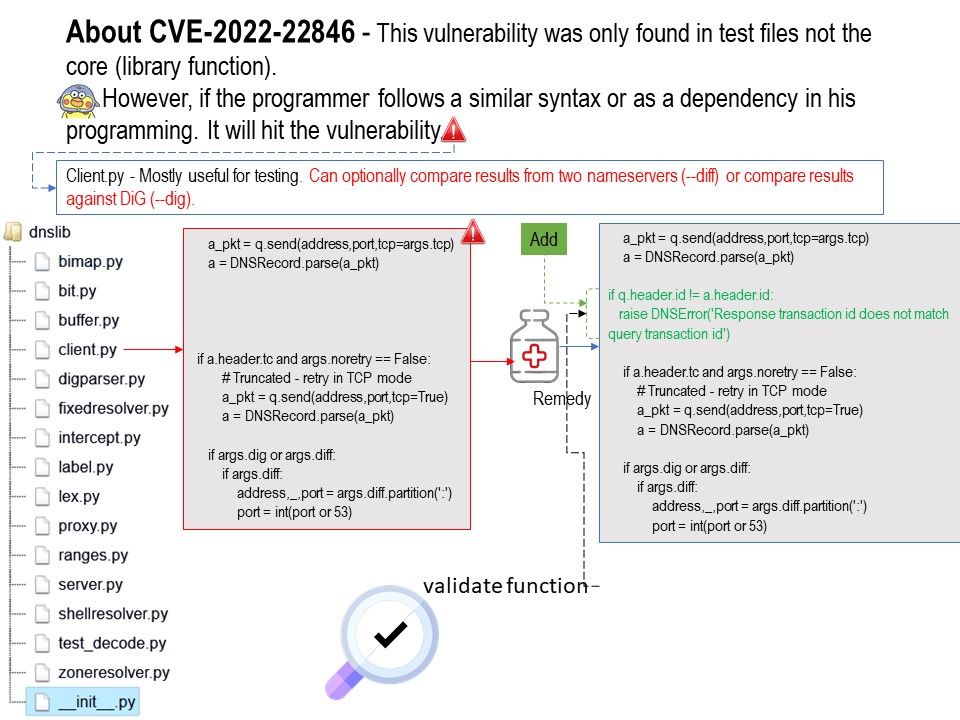
DNSLib is a Python library that provides the framework of a server. The file Client[.]py. Mostly useful for testing. Furthermore, it can optionally compare results from two nameservers (–diff) or compare results against DiG (–dig).
Vulnerability details: The dnslib package through 0.9.16 for Python does not verify that the ID value in a DNS reply matches an ID value in a query.
Official announcement: For details, please refer to the link – https://github.com/paulc/dnslib/issues/30
Remark: Application developers can write their own DNS servers using Python hosted on Kubernetes. Even if the risk of this vulnerability is not very high risk. Maybe it should know.
Just to be clear, the client is part of the package.
That is, of you install the package you can use the client.py via cmd line or from your code.
People tends to underestimate RFCs security guidelines and implementation details.
See blackhat Asia 2021 wonderful talk about RFC implementation bugs and vulnerabilities:
https://i.blackhat.com/asia-21/Thursday-Handouts/as-21-dosSantos-The-Cost-of-Complexity-Different-Vulnerabilities-While-Implementing-the-Same-RFC.pdf