Preface: JSON is a text-based data format following JavaScript object syntax. Even though it closely resembles JavaScript object literal syntax,
it can be used independently from JavaScript, and many programming environments feature the ability to read (parse) and generate JSON.
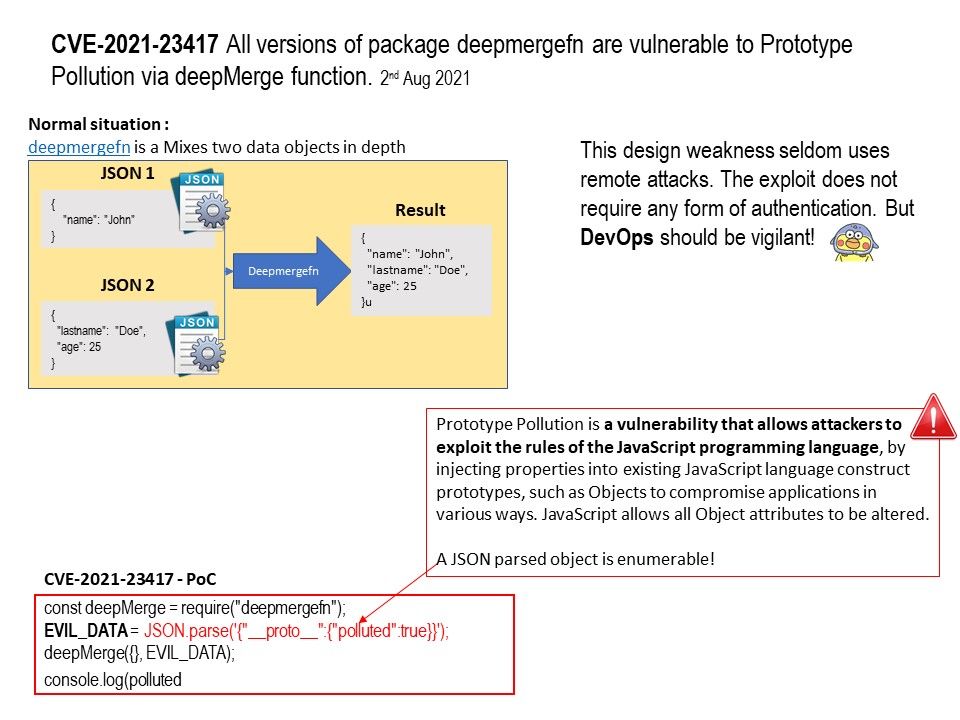
Background: Java application developer oftentimes need to combine objects into a single one which contains all the individual properties of its constituent parts. This operation is called merging. The two most common ways of doing display below:
- Using the spread operator (…)
- Using the Object.assign() method
Perhaps, developers may using another tool. For example: Deepmergefn
Alernative to deepmerge and Lodash_.merge.
Vulnerability details: JavaScript allows all Object attributes to be altered, including their magical attributes such as proto, constructor and prototype. An attacker manipulates these attributes to overwrite, or pollute, a JavaScript application object prototype of the base object by injecting other values.
Properties on the Object.prototype are then inherited by all the JavaScript objects through the prototype chain.
Workaround:
– Avoid using unsafe recursive merge functions.
-Consider using objects without prototypes (for example, Object.create(null)), breaking the prototype chain and preventing pollution.
Status: There is no fixed version release yet.