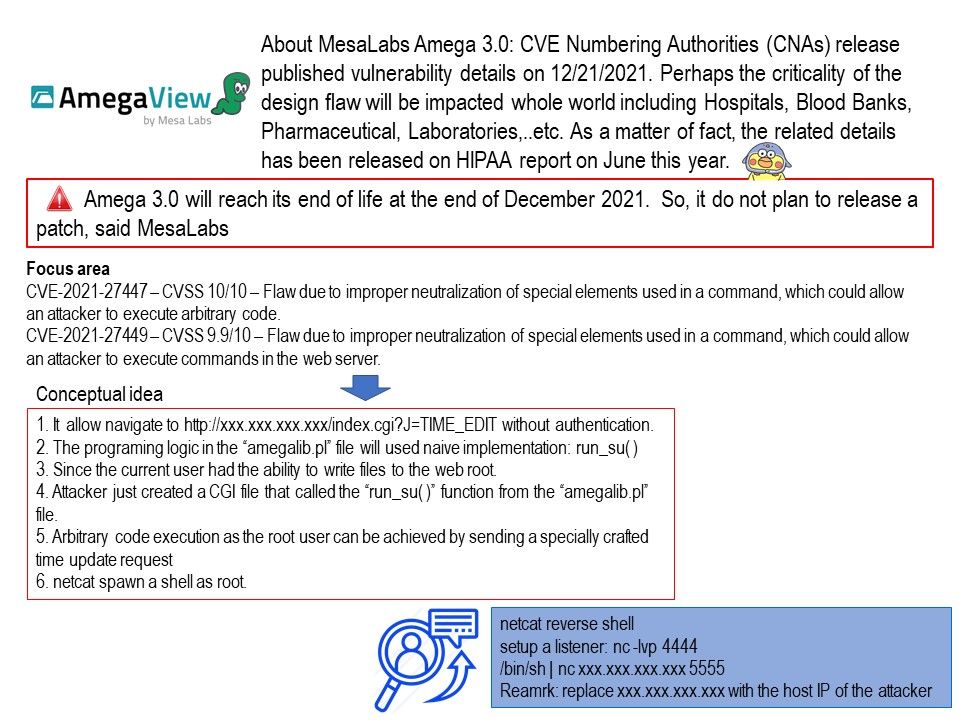
Preface: CVE Numbering Authorities (CNAs) release published vulnerability details for MesaLabs Amega version 3.0 on 12/21/2021. Perhaps the criticality of the design flaw will be impacted whole world including Hospitals, Blood Banks, Pharmaceutical, Laboratories,… As a matter of fact, the related details has been released on HIPAA report on June this year.
Background: AmegaView Environmental Monitoring system (CMS) 3.0 was released on 2015. The AmegaView CMS, consists of a robust hardware package and Mesa’s user-friendly software.
AmegaView is used to monitor parameters including Temperature, Humidity, CO2, O2, Differential Pressure, Leak Detection, Voltage, Door Switches, Switch Closures, Air Flow, Refrigerators, Freezers……
In addition, due to its function, it is used in various industries, such as hospitals, blood banks, pharmaceuticals, laboratories,..etc.
Vulnerability details:
CVE-2021-27447 – CVSS 10/10 – Flaw due to improper neutralization of special elements used in a command, which could allow an attacker to execute arbitrary code.
CVE-2021-27449 – CVSS 9.9/10 – Flaw due to improper neutralization of special elements used in a command, which could allow an attacker to execute commands in the web server.
CVE-2021-27445 – CVSS 7.8/10 – Insecure file permissions which could be exploited to elevate privileges on the device.
CVE-2021-27451 – CVSS 7.3/10 – Improper authentication due to passcodes being generated by an easily reversible algorithm, which could allow an attacker to gain access to the device.
CVE-2021-27453 – CVSS 7.3/10 – Authentication bypass issue that could allow an attacker to gain access to the web application.
If you are interested in possible attack scenarios, please refer to the attached drawings for reference.
Ref – ICS Advisory (ICSA-21-147-03): https://www.cisa.gov/uscert/ics/advisories/icsa-21-147-03