
Preface:
There are different countries located in the world, meanwhile so called regime has different governance concept and strategic task force in different area.
A simple introduction of regimes around the planet


Our story begin with Bear
Bear group views electronic warfare as an essential tool for gaining and maintaining information superiority over its adversaries. Therefore the bear group electronic warfare forces support denial and deception operations. Meanwhile their arsenal keen to developing the interception tools set and disruption equipment. Perhaps the war especially land to land, sea to sea combat does not happen in frequent.In order to control the communications of the enemy. The bear group break through the traditional concept. They weaponizing computer technique become a cyber weapon. As a result a series of cyber weapons was born.
The first cyber weapons aim to show to the world
On 20 July 2008, weeks before the Bear Group invasion of Georgia, the cyber attack vectors being growth. The website of the Georgian president was targeted, resulting in overloading the site.
Remark: This is the beginning phase of APT attack. However there is no such key words APT at that period time. From security point of view, this is the APT prototype. As a result such attack reform the victim workstation as a zombies. The attacks relies on the following attack criteria: OS design weakness especially zero day of attack and social engineering (spear-phishing).
Bear Group was blocking Georgian “internet portals” to supplement its military aggression. It suspend their external communications. The Internet has become a battleground at that time.
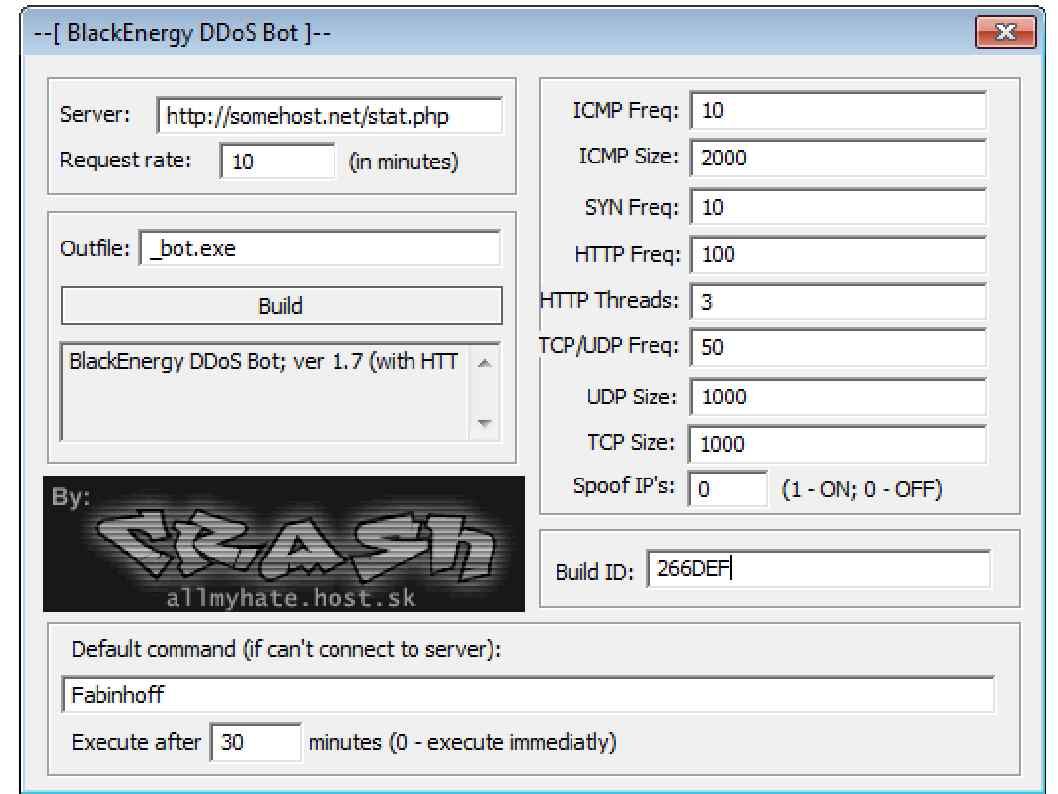
Such action provides an idea to the regime. The cyber attack will become a main trend in future since the digital world has been came. A cyber attack tool exploit so called “Black Energy”. This is a well know DDoS attack tool. A tool weaponized a computer software to fulfill the objective of military engagement.
Below picture shown the portable version of black energy
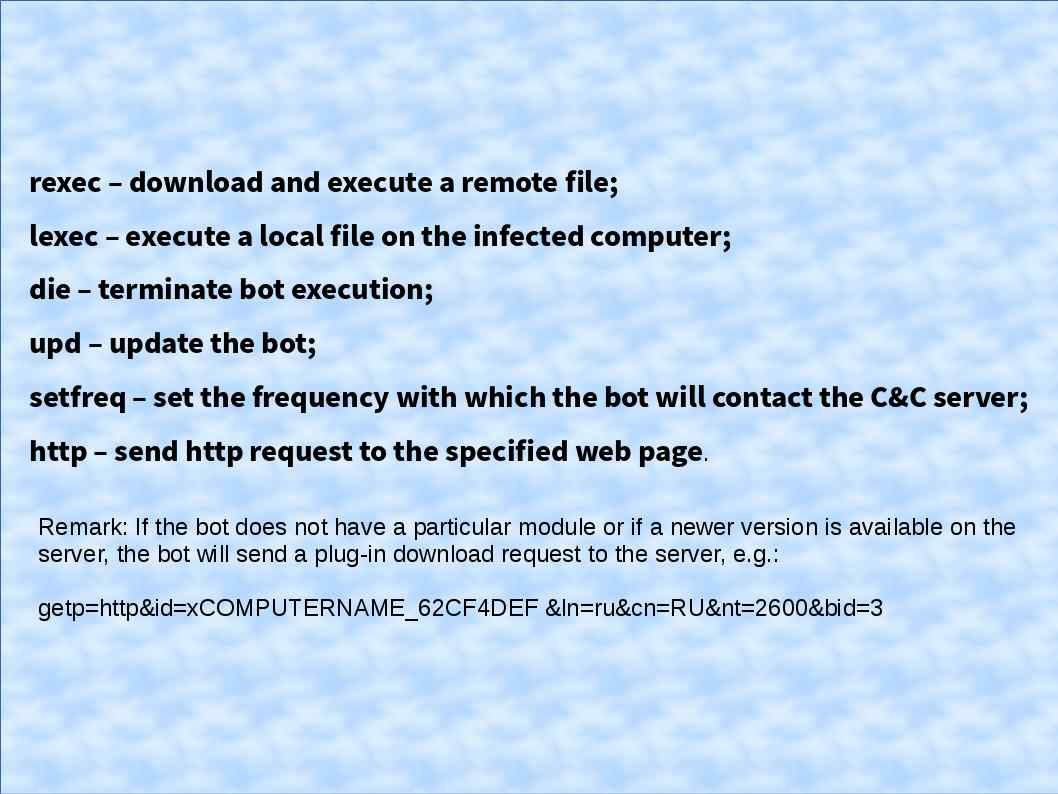
Black energy botnet infection path shown as below:

A cyber attack targeting nuclear facilities on 2010 from Eagle group. It strengthen the concept of bear group electronic warfare unintentionally. Meanwhile the developing team of bear group restructure of their arsenal. They are looking for a new model of attack method which completely suspended the hostile country operation. Thus a new cyber weapon born. It relies on Microsoft vulnerabilities found by Eagle Group security agency. A wannca cry was born and promoted to a arms sales. The preliminary objective of the tool originated South Korean nuclear power plant. But the task force looks not very smooth. And therefore the code free offer to criminal group to use.
Few months later, a enhance version of WannaCry ransomware appears in the cyber world which goal to sabotage nuclear power facilities. What is the advance feature of Not-Petya.
NotPetya spreads on its own. The original Petya required the victim to download it from a spam email, launch it, and give it admin permissions. NotPetya exploits several different methods to spread without human intervention. The original infection vector appears to be via a backdoor planted in M.E.Doc, an accounting software package that’s used by almost every company Ukraine.
Below table show the specifications of wannacry and Petya for reference.
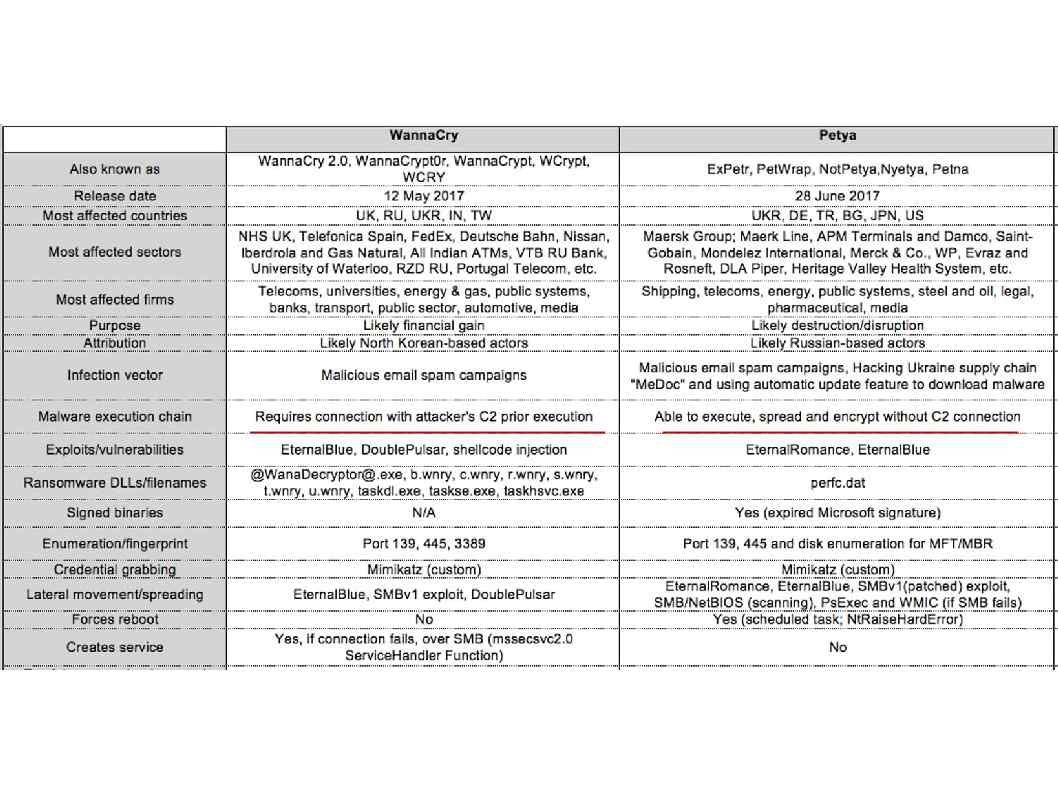
….the attack task force spread it out and become a main trend of hostile countries cyber attack.
End of story….
Bear Group intelligence agency overview:
The Iron Curtain was the name for the boundary dividing Europe into two separate areas from the end of World War II in 1945 until the end of the Cold War in 1991. And therefore people only focusing former KGB. Simple because they are not so much aware of GRU (Glavnoe Razvedytalnoe Upravlenie – Russian Military Intelligence). In the world that there is no key word “KGB” anymore. However the GRU substitute KGR original functions. But they more prefer deploy malware , malicious code implant to target engage the surveillance.
GRU strategic functions displayed as below:
- Political Intelligence
- Scientific and Technical Intelligence ( industrial espionage)
- Illegal Intelligence (Root kit, malware and ransomware)
This is a fiction. Any similarity is mere coincidence.
——- END ——-
Some truly wonderful content on this web site , appreciate it for contribution.
Hello, I think your website might be having browser compatibility issues. When I look at your website in Chrome, it looks fine but when opening in Internet Explorer, it has some overlapping. I just wanted to give you a quick heads up! Other then that, fantastic blog!